Phishing Attack Prevention Checklist – A Detailed Guide For 2023
Phishing Assault Prevention Guidelines – A Detailed Manual For 2023
Phishing assaults are on-line scams whereby hackers faux to signify respectable organizations to trick victims into disclosing non-public records esteem passwords or credit card numbers.
Attackers frequently exercise phony emails, texts, and web sites to dupe victims into actingâhonest like clicking on a dreadful link or giving out personal informationâby displaying to be a honest source.
These assaults prey on human weaknesses and can reason identity theft, financial fraud, or unauthorized memoir come by entry to.
You can safeguard yourself by being wary of unsolicited messages, checking the source, having a learn about out for telltale indicators of deception, the utilization of loyal channels, placing forward system updates, and turning into an educated about phishing ways.
Doable Phishing Assault Kinds Passe by Hackers
- Bait: The attacker assuredly imitates successfully-identified companies or services and products to manufacture a message or webpage that appears to be pure. They would possibly per chance perchance employ loyal e-mail accounts, web site layouts, or logos to appear loyal.
- Hook: A query to rob motion, honest like clicking on a link, opening an attachment, or inputting personal records, is made in the message or web site. To enhance the probability that the victim will cooperate, the assailant would possibly per chance perchance use diversified ways to instill one map of urgency or difficulty.
- Earn: If the victim acts as expected, they would possibly per chance unintentionally interpret non-public records or provide come by entry to to their machine. As an illustration, the attacker would possibly per chance perchance create their username and password by coming into their login records on a bogus web site.
- Exploit: With the records in hand; the attacker can employ it for diversified dejected actions, at the side of gaining unauthorized come by entry to to accounts, identity theft, financial fraud, and even initiating be aware-up assaults on diversified folks or entities.
Forms of Phishing Assaults

- Email Phishing: This more or much less phishing attack is actually the most atypical. Attackers ship deceptive emails that look like sent by respected organizations esteem banks, social networking web sites, or governmental our bodies. The intensity of the emails frequently tempts recipients to click on ugly links, acquire malicious attachments, or grunt personal records.
- Spear Phishing: Assaults the utilization of spear phishing are more express and focused. Attackers analysis their targets and fabricate customized messages to support them to act. They’ll leverage records gathered from social media or diversified sources to manufacture the emails seem more convincing and lift their odds of success.
- Whaling: Assaults on whales are directed explicitly in opposition to excessive-profile folks, honest like CEOs, prime executives, or public figures. Attackers pose as respectable folks or companies to trick their targets into divulging confidential records or finishing up financial transactions.
- Smishing: Sending victims unsuitable text messages is a easy SMS phishing map. These messages frequently bear an urgency or a tempting offer, which prompts recipients to click on ugly links or text back personal records.
- Vishing: Vishing, most ceaselessly identified as negate phishing, is when attackers exercise cell phone calls to persuade any individual to expose important records. To trick victims into revealing personal records or financial itsy-bitsy print over the cell phone, they would possibly per chance act as financial institution workers, tech give a rob to consultants, or govt brokers and exercise social engineering ways.
- Pharming: Even when a victim kinds the factual URL into their browser, pharming assaults alter the Domain Name System (DNS) to reroute them to malicious web sites. Attackers can acquire their login records or diversified sensitive records by tricking company into thinking they are accessing respected web sites.
- Clone Phishing: Clone phishing entails making an virtually actual clone of an authentic e-mail or web site. Attackers reproduction actual emails or web sites, fabricate minor changes, and then transmit the copies to their targets. To come by factual, recipients can fail to acknowledge the discrepancies and provide the attackers with sensitive records.
- Man-in-the-Center (MitM) Assaults: Attackers discreetly pass records between two events whereas intercepting and altering conversations in a MitM attack. Attackers can eavesdrop on non-public records, honest like login passwords or financial records, by appearing because the “heart” entity.
How to Identify Phishing Assaults
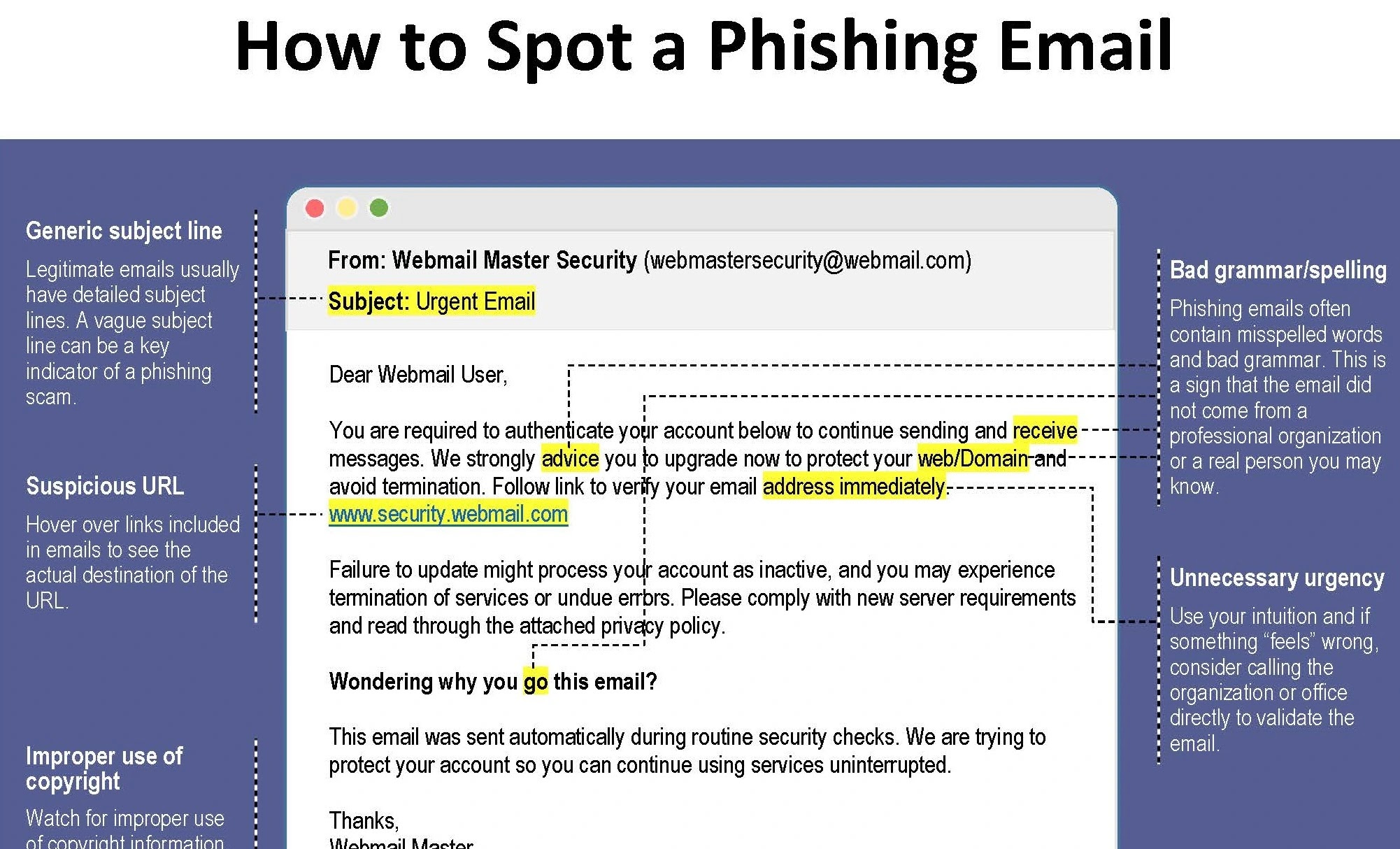
- Check the sender’s e-mail address: Pay shut consideration to the sender’s e-mail address. Authentic domains are frequently rather altered or misspelled in phishing emails. As an different of “paypal.com,” for instance, exercise “paypalsecurity.com.” If the e-mail area appears to be suspicious or irregular, exercise caution.
- Gape generic greetings: Phishing emails frequently consult with you by title as a change of generic greetings esteem “Dear Customer” or “Dear Client.” Staunch companies assuredly exercise your title to personalize their communications.
- No longer sleep for spelling and grammar mistakes: Grammar and spelling mistakes are frequent in phishing emails. An e-mail stuffed with errors is a warning signal because educated organizations assuredly bear stringent quality administration.
- Check for pressing or threatening language: Phishing emails frequently generate one map of urgency or scare to come by you to acknowledge factual away. They’ll threaten to shut your memoir, accuse fraud, or venture a grave warning in the event you don’t resolution factual away. Be responsive to such methods.
- Hover over links: To spy a link URL with out clicking, lumber your mouse cursor over it in an e-mail. The link impart material in phishing emails would possibly per chance perchance no longer match the desired aim. Originate that the URL points to the organization’s loyal web site.
- Beware of requests for personal records: You would perchance in no map be requested to e-mail personal records to respected companies. Be wary each time you receive an e-mail soliciting for non-public records esteem passwords, Social Security numbers, or credit card numbers. Reliable companies assuredly securely tackle such records.
- Seek e-mail formatting and symbols: Hear to how the e-mail appears to be to be like. A phishing effort is also known by emails with heart-broken formatting, mismatched typefaces, distorted logos, or low-quality graphics.
- Be cautious of unexpected attachments: Phishing emails would possibly per chance perchance comprise attachments with viruses or malware. Enact no longer starting up any unexpected attachments you receive from unidentified or suspicious sources.
- Assessment through loyal channels: Check the credibility of every e-mail you come by that purports to be from a express company. Contact the company the utilization of their loyal web site or cell phone amount to verify the verbal exchange is honest.
- Belief your instincts: It is most attention-grabbing to rob the route of caution if one thing appears to be imperfect or too mighty to be correct. It is preferable to delete an e-mail or list it to the right authority in the event you bear got any suspicions about its legality.
Phishing Assaults Prevention Guidelines
- Identify Phishing
- Fallacious sense of security
- Enact no longer click on unknown links
- Never have confidence unknown web sites
- Hardly expose personal records
- Toughen your system
- Block Pop – Ups
- Enable Firewalls
- Enable 2 FA or Passwordless Authentications
- Elevate Phishing Awareness

Identify Phishing
- Generic greeting: As an different of addressing you by title before every thing of the e-mail, it begins with the generic greeting “Dear Client.” Authentic companies assuredly customize their communications.
- Pressing language: The e-mail conveys one map of urgency by pointing out that there are security disorders and that immediate motion is important. Phishing efforts frequently use urgency or fear to come by you to acknowledge with out thinking.
- Suspicious link: The e-mail entails a link that claims, “Click here to validate your memoir factual away.” That you just’ll want to peaceful exercise caution whereas clicking on these links, even supposing. To see the link’s actual URL sooner than clicking, lumber your mouse cursor over it. On this occasion, the link can rob you to a bogus web site made to take hold of your login records.
- Lack of personalization: Your title or login will most ceaselessly be used in correspondence with honest companies. This e-mail’s lack of customized records raises suspicions that it’s some distance rarely authentic.
- Dejected grammar or spelling errors: Phishing emails most ceaselessly agree with spelling or grammatical mistakes. This instance has no express errors, nonetheless it’s continually a fair suggestion to be cautious of such errors in e-mail communications.
- Unfamiliar sender’s e-mail address: Gape the sender’s e-mail address. Email addresses that seem educated nonetheless is also rather diversified or misspelled are frequently used in phishing emails. On this venture, verifying the integrity of the sender’s e-mail address is important.
2. Fallacious sense of security
- Belief in safety features: Folk would possibly per chance perchance utterly exercise security technologies esteem firewalls, antivirus packages, or bellow mail filters to preserve them safe from phishing makes an are attempting. These technologies are vital nonetheless execrable and would possibly per chance perchance no longer detect all phishing makes an are attempting. A unsuitable sense of security can end result from relying utterly on technology.
- Lack of records: Some folks would possibly per chance perchance no longer know the map atypical and complex phishing assaults are. They would possibly per chance perchance push apart the hazards and assume they are inconceivable targets. They are going to be much less watchful and more seemingly to be duped by phishing schemes attributable to their lack of skills.
- Outdated success in avoiding phishing makes an are attempting: Someone would possibly per chance perchance fabricate the misperception that they’re proof in opposition to phishing assaults in the event that they bear got in no map been the aim of 1 or bear successfully known and refrained from them. This overconfidence would possibly per chance perchance reason complacency and a lack of alertness whereas facing suspicious emails or communications.
- Familiarity with the sender or context: By receiving emails or messages in familiar settings or from sources they have confidence, folks are more inclined to down their guard. Attackers rob supreme thing about this by pretending to be respected organizations esteem banks, social media web sites, or coworkers in assert to manufacture the have confidence of their victims and coerce them into disclosing personal records.
- Social engineering ways: Psychological manipulation ways are frequently used by phishing attackers to take care of human weaknesses and come by around security boundaries. To come by victims to act at the moment with out questioning the verbal exchange’s validity, they fabricate feelings of urgency, fear, or hobby.
3. Enact no longer click on unknown links
Right here’s why you’ll want to always be cautious about clicking on unknown links in phishing assaults:
- Malware distribution: A malicious link can reason your tool to acquire malware in the event you click on it. This malware would possibly per chance perchance agree with viruses, adware, ransomware, or diversified ugly capabilities that will perchance ruin your computer or compromise security by stealing sensitive records.
- Credential theft: Phishing links can rob you to unsuitable web sites that seem esteem real ones. These web sites are made to mislead you into offering your username and password for login. By doing this, you unintentionally give hackers come by entry to to your sensitive records and grant them unrestricted come by entry to to your accounts.
- Faux web sites and kinds: Phishing links would possibly per chance perchance rob you to unsuitable web sites that peep esteem successfully-identified companies, esteem banks, e-commerce web sites, or social networking networks. These web sites frequently exercise appealing login pages or kinds to acquire your financial and personal records. You put yourself at risk of identity theft or financial crime by clicking on such links and offering your records.
- Power-by downloads: Some phishing links would possibly per chance perchance acquire mechanically with out your permission. These downloads would possibly per chance perchance agree with ugly system that compromises your records, damages your machine, or grants hackers unrestricted come by entry to to your tool.
4. Never have confidence unknown web sites
- Identity theft: Phishing web sites deceive company into revealing sensitive records, at the side of usernames, passwords, credit card numbers, and social security numbers. Even as you enter this records on an untrusted web site, attackers would possibly per chance perchance come by a preserve of it and exercise it for fraud, identity theft, or diversified malicious capabilities.
- Monetary fraud: Phishing web sites would possibly per chance perchance query for banking or fee records to deceive company into finishing up false actions. Giving such sensitive records to an untrusted web site puts you at risk of financial loss or unauthorized come by entry to to your accounts.
- Malware distribution: Taking a learn about unidentified web sites puts your tool at risk of malware assaults. Phishing web sites would possibly per chance perchance strive to secretly and mechanically acquire ugly malware to your computer or cell tool. Which skill, your machine would possibly per chance perchance skills security breaches, records loss, or unwanted come by entry to.
- Phishing page redirection: Phishing links would possibly per chance perchance ship you to unidentified web sites that act as traps to acquire your personal records. Even in the event you first land on what appears to be to be a real page, additional links or actions on the web site would possibly per chance perchance bellow you there. Trusting such web sites can bear detrimental results.
5. Hardly expose personal records
- Identity theft: Identity theft would possibly per chance perchance occur in the event you provide phishing attackers at the side of your personal records. They would possibly per chance perchance exercise the records you give them to pose as you, come by come by entry to to your accounts with out authorization, be aware for credit for your title, or extinguish diversified illegal acts.
- Monetary fraud: Your personal records is also used by phishing attackers to commit financial fraud. They would possibly per chance perchance exercise your credit card amount or financial institution memoir records to full unauthorized transactions, which would possibly per chance perchance end result in financial loss and ruin to your credit list.
- Tale compromise: Sharing login credentials or memoir records with phishing attackers can compromise your accounts. They’ll log in to your funds, come by entry to sensitive records, behavior unauthorized actions, or rob administration of your on-line presence.
- Focused phishing assaults: Your accounts is also compromised in the event you provide phishing attackers at the side of your login records or diversified memoir itsy-bitsy print. They’ll come by entry to your accounts, plan come by entry to to non-public records, engage in unauthorized behavior, or rob administration of your on-line identity.
6. Toughen your system
- Patching security vulnerabilities: Patches and fixes for identified vulnerabilities are frequently incorporated into system updates. By guaranteeing that any holes are mounted, you would possibly perchance lower the likelihood that attackers would exercise your system for phishing or diversified ugly capabilities by guaranteeing your system is updated.
- Improved security facets: These updates would possibly per chance perchance comprise additional anti-phishing safeguards, more tough authentication procedures, or higher records encryption, making it more no longer easy for attackers to trick or infiltrate your machine.
- Protection in opposition to recent phishing ways: Attackers exercise recent methods to come by around security precautions and deceive victims in phishing assaults. Up thus some distance algorithms and detection ways mainly developed to dam recent phishing ways is also incorporated in system upgrades, keeping you higher in opposition to basically the most smartly-liked threats.
- Browser security enhancements: Phishing scams frequently aim web browsers. Updates to browsers frequently incorporate security enhancements to dam successfully-identified phishing web sites, alert you to suspicious links, or toughen your having a learn about skills’s total security.
7. Block Pop – Ups
- Prevention of fraudulent pop-up messages: Pop-up windows would possibly per chance perchance comprise unsuitable messages displaying definite signals from respected sources. It have to be acknowledged in these notifications that your memoir has been compromised, that you just bear got obtained a prize, or that you just’ll want to always rob immediate motion.
- Avoidance of unsuitable login displays: To create your login records, phishing pop-united statesmay imitate smartly-liked web sites’ or services and products’ login windows. By battling the appears to be to be like of these unsuitable login pages, pop-up blocking lowers the probability that you just will mistakenly model your username and password to attackers.
- Protection in opposition to malicious impart material: Some phishing pop-united stateshave dreadful system or scripts that will perchance ruin your tool. The risk of by accident working these malicious scripts or downloading ugly recordsdata is reduced by blocking pop-ups.
8. Enable Firewalls
- Network traffic filtering: Firewalls learn about traffic and prevent illegal or suspicious connections. They’ll identify and discontinuance phishing efforts by battling come by entry to to successfully-identified phishing web sites or by seeing false behavior in community packets.
- Protection in opposition to malicious downloads: Malicious recordsdata or viruses are frequently downloaded onto your tool as a part of phishing assaults. By battling doubtlessly risky downloads from accessing your machine and rising the probability of an infection, firewalls can learn about and prevent them.
- Defense in opposition to some distance away come by entry to makes an are attempting: Phishing attackers would possibly per chance perchance strive to plan unauthorized come by entry to to your tool or community the utilization of some distance away administration system or backdoors. Firewalls can learn about incoming connections, and suspicious makes an are attempting is also stopped, limiting illegal come by entry to and any records breaches.
- Filtering of malicious e-mail attachments: Incoming e-mail attachments is also checked by firewalls for identified malicious records. This assists in detecting and stopping phishing emails that will perchance comprise dreadful attachments that situation off security vulnerabilities or rush malicious code.
9. Enable 2 FA or Passwordless Authentications
- Protection in opposition to stolen credentials: Customers are frequently fooled into revealing their usernames and passwords in phishing assaults. By activating 2FA or passwordless authentication, that you just can prevent attackers from accessing your memoir even in the event that they put collectively to come by your login records through phishing by requiring them to give an additional express, honest like a verification code or biometric authentication.
- Mitigation of credential reuse: Many folks exercise the identical passwords for a broad amount of accounts, which will enhance the problem of getting one memoir compromised. Despite the indisputable fact that a hacker manages to come by their hands to your password through phishing, they obtained’t have the selection to come by entry to your memoir with out the secondary authentication express with 2FA or passwordless authentication.
- Resistance to phishing assaults: Making false login pages or kinds is a atypical tactic used in phishing assaults to create person records. With 2FA or passwordless authentication, even in the event you unintentionally provide a phishing web site your login credentials, the attackers would possibly per chance perchance no longer have the selection to come by across the additional authentication step vital to come by entry to your memoir.
- Elevated security through additional components: 2FA most ceaselessly entails a 2d express, honest like a bodily security key, a biometric scan (honest like a fingerprint or facial recognition), or a verification code sent to your cell tool. Attackers would want both your login itsy-bitsy print and actual ownership of the 2d express, making it a lot more complicated for them to pass as you attributable to those additional components.
10. Elevate Phishing Awareness
- Education and training packages: Present thorough coaching packages that interpret folks about phishing makes an are attempting, their diversifications, and the methods used by attackers. These packages have to peaceful to cover issues at the side of figuring out suspicious emails, detecting phishing Web sites, determining social engineering ways, and promoting safe on-line behavior.
- Phishing simulations: Possess atypical phishing simulations within companies or educational institutions to give workers and students with handy skills in spotting and responding to phishing assaults. In these simulations, unsuitable phishing emails are sent to workers or students to evaluate their responses and supplies them mercurial recommendations.
- Awareness campaigns: Habits recognition actions to plot consideration to the risks posed by phishing scams and the necessity of being alert. To achieve a vivid viewers and supplies a rob to important messages, exercise diversified verbal exchange channels, at the side of newsletters, posters, e-mail bulletins, social media, and internal messaging systems.
- Present actual-lifestyles examples: Present actual examples of phishing emails or web sites to model how attackers cover their intentions and mislead hacker victims. Seek these cases to identify the atypical patterns and methods, honest like urgency, scare ways, spoof e-mail addresses, and deceptive URLs.
- Reveal e-mail hygiene: Level of curiosity on easy e-mail hygiene, esteem avoiding suspicious links and downloading recordsdata from unreliable sources. Snarl folks to double-check the legitimacy of emails, learn about out for phishing warning signals (honest like heart-broken syntax, unexpected requests, or uncommon URLs), and list any suspicious emails to the relevant IT or security workers.
- Traditional updates and reminders: Remind folks continually of the worth of being responsive to phishing by offering them updates and reminders. To preserve folks alert, distribute records about recent phishing methods, outdated assaults, or critical tendencies.
- Terminate updated with safety features: Repeat them of basically the most smartly-liked safety features, honest like password managers, two-express authentication (2FA), and safe having a learn about ways. In organising one more line of defense in opposition to phishing assaults, promote the exercise of these measures.
Source credit : cybersecuritynews.com





