PlugX USB worm Infected Over 2.5M Devices
.webp)
A brand original threat has emerged, affecting thousands and thousands of devices worldwide.
The PlugX USB worm, a cosmopolitan malware, has been reported to win infected over 2.5 million devices, posing a important threat to world cybersecurity.
The PlugX malware, within the starting set aside known several years ago, has obtained repute for its resilience and abilities to unfold thru USB drives.
In March 2023, cybersecurity consultants at Sophos highlighted a variant of PlugX with enhanced worming capabilities that may possibly jump borders and infiltrate networks undetected.
An infection Unfold
By September 2023, the declare escalated when researchers successfully sinkhole a expose and abet a watch on (C2) server associated with the PlugX worms.
For a mere $7, they obtained a special IP contend with linked to the worm variant, which revealed a staggering choice of infected public IP addresses.
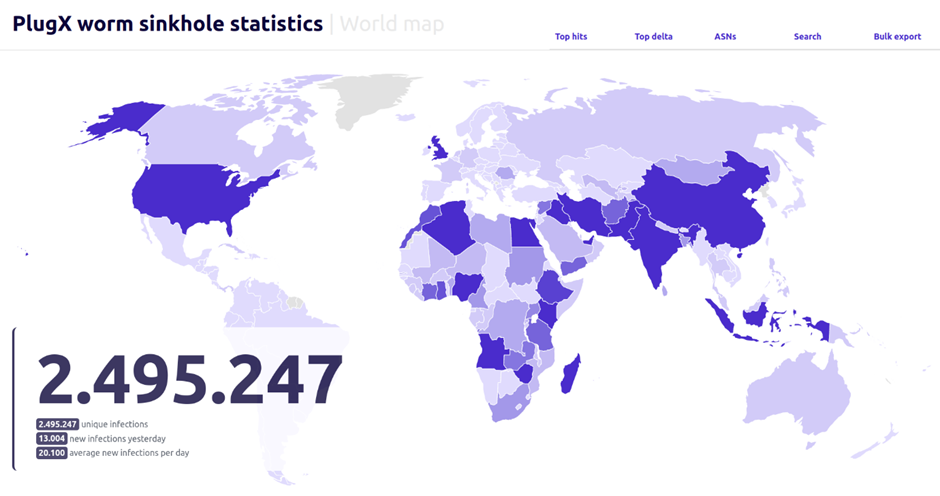
In accordance to Sekoia’s findings, No topic the malware’s inception years prior, on each day foundation requests from roughly 90,000 to 100,000 irregular IPs win been restful being sent to the sinkhole.
Over six months, extra than 2.5 million irregular IPs linked to it, indicating the worm’s broad attain.
Combine ANY.RUN in Your Company for Efficient Malware Analysis
Are you from SOC, Possibility Be taught, or DFIR departments? If that’s the case, you may possibly possibly possibly join an internet neighborhood of 400,000 just security researchers:
- Right-time Detection
- Interactive Malware Analysis
- Easy to Be taught by Unique Security Team of workers members
- In discovering detailed experiences with maximum recordsdata
- Situation Up Digital Machine in Linux & all Home windows OS Variations
- Interact with Malware Safely
In elaborate for you to check all these features now with entirely free fetch admission to to the sandbox:
Mitigation
The fight against PlugX took a flip when consultants cracked the cryptography of its communications.
This leap forward allowed the pattern of disinfection instructions which may possibly be sent to compromised workstations.
Two recommendations win been devised: one which cleanses the workstation and one other, extra intrusive technique that furthermore purges the USB force.
In an unprecedented transfer, a view of sovereign disinfection became as soon as proposed. Legislation enforcement businesses and national Laptop Emergency Response Teams win been offered the instruments to eliminate the malware from infected hosts remotely.
This blueprint objectives to empower nations to rob abet a watch on of their cybersecurity by inserting off the threat from inner their digital borders.
The PlugX USB worm’s giant an infection rate is a stark reminder of the chronic threat cybercriminals pose.
While the worm can not be entirely eradicated, the collaborative efforts of cybersecurity communities win opened a path to mitigating its impact.
The sovereign disinfection job is a novel technique that affords a glimmer of hope within the fight against pervasive cyber threats.
The PlugX USB worm saga underscores the importance of world cooperation in cybersecurity and the need for continuous vigilance in an ever-changing threat landscape.
As the sector becomes extra and extra interconnected, resilient and adaptable cybersecurity measures may possibly be paramount in safeguarding our digital future.
Indicators of compromise
Files Hashes
432a07eb49473fa8c71d50ccaf2bc980b692d458ec4aaedd52d739cb377f3428
e8f55d0f327fd1d5f26428b890ef7fe878e135d494acda24ef01c695a2e9136d
3a53bd36b24bc40bdce289d26f1b6965c0a5e71f26b05d19c7aa73d9e3cfa6ff
2304891f176a92c62f43d9fd30cae943f1521394dce792c6de0e097d10103d45
8b8adc6c14ed3bbeacd9f39c4d1380835eaf090090f6f826341a018d6b2ad450
6bb959c33fdfc0086ac48586a73273a0a1331f1c4f0053ef021eebe7f377a292
b9f3cf9d63d2e3ce1821f2e3eb5acd6e374ea801f9c212eebfa734bd649bec7a
Source credit : cybersecuritynews.com


