PoC Published for Critical RCE Vulnerability in Fortra FileCatalyst
.webp)
A proof of View (PoC) has been published for a serious Distant Code Execution (RCE) vulnerability identified in Fortra’s FileCatalyst machine.
This vulnerability, tracked as CVE-2024-25153, poses a severe threat to organizations the utilization of the FileCatalyst Workflow Net Portal. It potentially enables attackers to procure arbitrary code on affected systems.
Working out CVE-2024-25153
The core of the vulnerability lies in a directory traversal flaw within the ‘ftpservlet’ component of the FileCatalyst Workflow Net Portal.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams deserve to triage 100s of vulnerabilities. :
- The area of vulnerability fatigue this day
- Distinction between CVSS-explicit vulnerability vs risk-primarily primarily based mostly vulnerability
- Evaluating vulnerabilities fixed with the exchange impact/risk
- Automation to lower alert fatigue and improve security posture a great deal
AcuRisQ, that allows you to quantify risk accurately:
Exploiting this flaw, attackers can bypass intended security mechanisms to add files out of doorways the designated ‘uploadtemp’ directory thru a specially crafted POST seek info from.
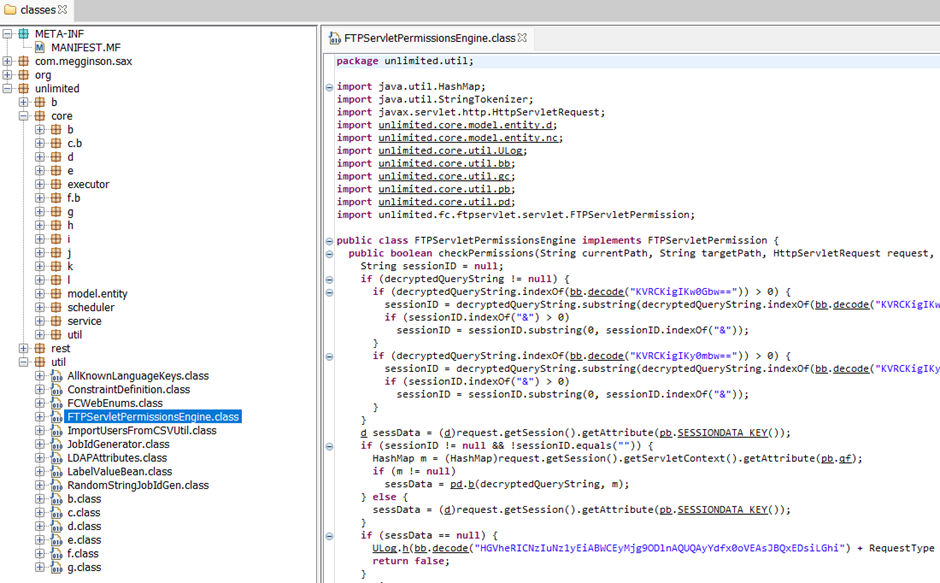
If an attacker successfully uploads a file to the web portal’s DocumentRoot, they could well well leverage specially crafted JSP files to procure arbitrary code on the server, including deploying web shells for power procure correct of entry to and control.
The vulnerability has been assigned a CVSSv3.1 gain of 9.8, categorizing it as serious on account of its skill impact on confidentiality, integrity, and availability.
Fortran has addressed this vulnerability by releasing an exchange for FileCatalyst Workflow. Users are told to toughen to model 5.1.6 Fabricate 114 or increased to mitigate the risk associated with CVE-2024-25153.Update Notification
Implications and Suggestions
The e-newsletter of a PoC for CVE-2024-25153 underscores the significance of timely patch management and vulnerability evaluation within organizations.
Given this vulnerability’s serious nature, Fortra FileCatalyst Workflow customers must practice the offered updates straight away.
Additionally, organizations could quiet grab into myth conducting a thorough security overview of their web functions and implementing layered security features to shield against linked threats.
Preserve updated on Cybersecurity news, Whitepapers, and Infographics. Apply us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


