PoC Released for JavaScript execution Vulnerability in PDF.js
.webp)
A valuable vulnerability, CVE-2024-4367, has been came across in PDF.js, a extensively used JavaScript-primarily based totally PDF viewer maintained by Mozilla.
The procedure back affects all Firefox users with versions below 126 and a host of internet and Electron-primarily based totally applications that manufacture basically the most of PDF.js for PDF preview functionality.
PDF.js is integrated into Firefox as its constructed-in PDF viewer and is moreover available as a Node module known as pdfjs-dist, which has approximately 2.7 million weekly downloads on NPM.
Codean Labs came across this vulnerability, allowing attackers to entire arbitrary JavaScript code when a malicious PDF file is opened.
Numerous internet sites utilize this module to provide embedded PDF preview functionality, making the impact of this vulnerability a long way-reaching.
CVE-2024-4367 – Technical Significant points and Exploitation
The vulnerability stems from an oversight in the font rendering code of PDF.js.
Namely, it entails pre-computing a course generator procedure for every glyph using a JavaScript Feature object.
If an attacker can control the commands (cmds) going into the Feature physique, they are able to insert and discontinue arbitrary code.
Here is a snippet of the inclined code:
// If we can, compile cmds into JS for MAXIMUM SPEED... if (this.isEvalSupported && FeatureTest.isEvalSupported) { const jsBuf = []; for (const current of cmds) { const args = current.args !== undefined ? current. args.join(","): ""; jsBuf.push("c.", current.cmd, "(", args, ");n"); } // eslint-disable-next-line no-new-func console.log(jsBuf.join("")); return (this.compiledGlyphs[character] = new Function( "c", "size", jsBuf.join("") )); }The vulnerability is brought about by manipulating the fontMatrix array, that will likely be specified by the PDF metadata.
An attacker can fracture the JavaScript syntax and discontinue arbitrary code by inserting a string cost into this array.
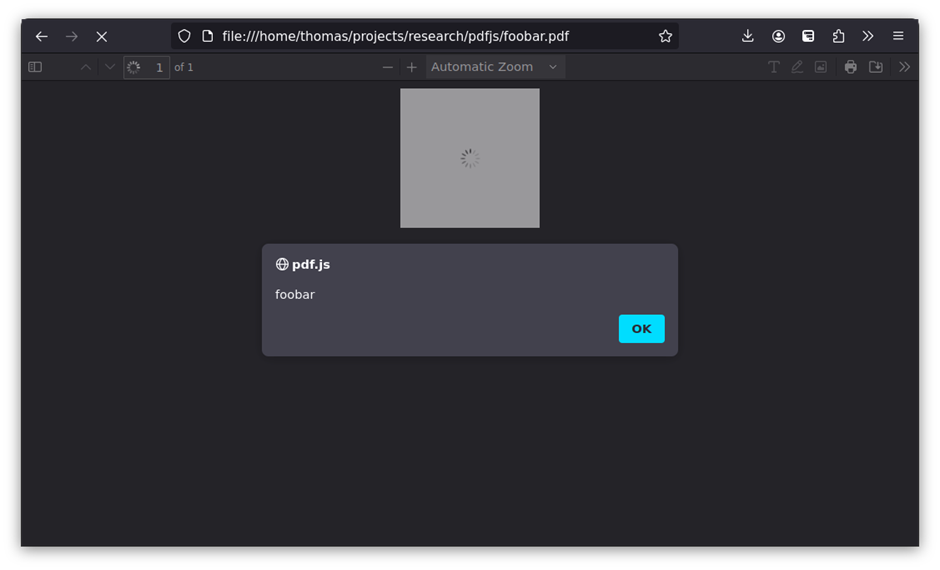
As an illustration, the following FontMatrix definition can trigger an alert:
/FontMatrix [1 2 3 4 5 (0); alert('foobar')]
To mitigate this vulnerability, it is suggested that PDF.js be up so a long way to model 4.2.67 or elevated.
Most wrapper libraries, reminiscent of react-pdf, have moreover released patched versions.
Developers might perhaps presumably moreover peaceful recursively test their node_modules folder for recordsdata named pdf.js to manufacture obvious they’re not using a inclined model.
Moreover, surroundings the PDF.js surroundings isEvalSupported to unsuitable can disable the inclined code course.
Enforcing a strict snarl material-safety protection that disables using eval and the Feature constructor can moreover prevent the vulnerability from being exploited.
Source credit : cybersecuritynews.com

