Quickly Check if a Sample is Malicious with ANY.RUN Sandbox Process Tree
Like a flash Test if a Sample is Malicious with ANY.RUN Sandbox Job Tree
ANY.RUN’s Job Tree reveals the total processes that initiate when a file or URL is speed in its sandbox, alongside with their hierarchical relationships.Here’s finished by capturing the preliminary process initiated by the pattern and to any extent further processes it generates. This affords a complete determining of the pattern’s habits and interactions with the blueprint.
It permits for rapid identification of mother or father-baby process relationships, tracing doable malicious order reduction to its offer, and total comprehension of the pattern’s efficiency at a undercover agent.Â
In accordance with the ANY.RUN detailed write-up, the process tree visualizes process relationships and affords tools for analysis, whereas icons camouflage suspicious activities and process signatures. Clicking icons reveals static data esteem PE small print, memory dumps, and configuration recordsdata.Â
Tags name malware families and threats; a score is calculated per process events. Highlighting permits you to circulation over PIDs in various tabs to ogle the corresponding process in the tree, whereas triangle icons can can let you know the approach to give diagram teams.Â
Clicking a process opens a tab with match descriptions, classifications (Risks, Warnings, Others), MITRE ATT&CK mappings, and match categorization by criticality, which additionally impacts the malicious score.Â
SOC analysts can use process tree analysis to resolve a file’s legitimacy in the starting up. When a apparently harmless file (esteem an image) triggers execution inside a digital machine, the resulting process tree exposes the file’s true nature.Â
Even supposing signature-based fully detection fails, the analyst can name malicious intent per the spawned processes, taking into yarn swift reporting and the removing of the possibility.Â
Integrate ANY.RUN in Your Firm for Effective Malware Prognosis
Are you from SOC, Possibility Compare, or DFIR departments? In that case, it is possible you’ll presumably presumably even be a part of an on-line crew of 400,000 unbiased security researchers:
- Steady-time Detection
- Interactive Malware Prognosis
- Easy to Learn by Unique Security Crew contributors
- Gather detailed experiences with most data
- Space Up Digital Machine in Linux & all Home windows OS Variations
- Have interaction with Malware Safely
Need to you’ll want to envision all these capabilities now with entirely free entry to the sandbox:
Studying from the Job Tree
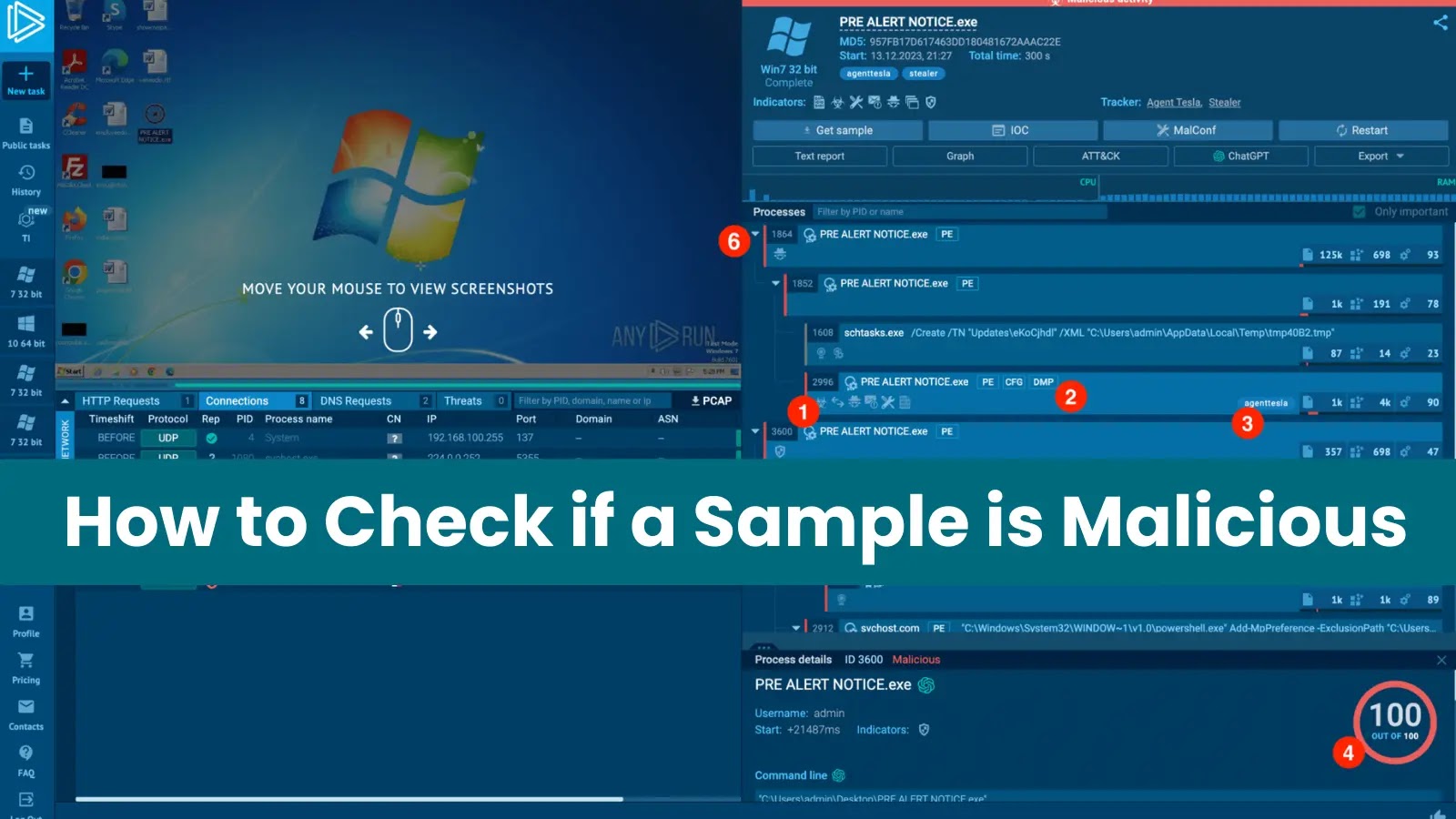
ANY.RUN, a possibility analysis platform, displays a process tree to analyze a loaded executable file, which reveals how processes are spawned and connected to every various. On this case, the process tree of “PRE ALERT NOTICE.exe” reveals extra than one pertaining to aspects.Â
First, a process (PID 2996) with the ticket “agenttesla” is chanced on, which strongly aspects to malicious order centered on two cases of “PRE ALERT NOTICE.exe” (PIDs 1864 and 3600), which appear to be working independently inside the blueprint.
Prognosis of process ID 1864 reveals a doubtlessly trojan horse named “PRE ALERT NOTICE.exe,” which replicates itself and spawns additional processes. One baby process makes use of “shtasks.exe” to impact a scheduled process named “UpdateseKoCjhdl”.
The duty seemingly makes an strive to set aside persistence on the blueprint or upload malicious data and the randomly generated process name and the use of the non everlasting record (AppDataLocalTemp) for the duty definition file (tmp40B2.tmp) are solid indicators of malicious intent.
The malicious process (PID 3600) creates fraudulent svchost.com processes to cloak itself by spawning powershell.exe cases, that will seemingly be ragged to download extra malware.
PID 3600 replicates itself by creating one other occasion of the first malware executable. For analysis functions, the Job Graph realizing is priceless for visualizing the relationships between processes and figuring out the malicious ones, even when going thru an limitless sequence of processes.Â
What’s ANY.RUN?
ANY.RUNÂ is a cloud-based fully malware lab that does most of the work for security teams. 400,000 professionals use ANY.RUNÂ platform each day to look at into events and trudge up possibility research on Linux and Home windows cloud VMs.
Advantages of ANY.RUN
- Steady-time Detection:Â ANY.RUN can procure malware and proper now name many malware families using YARA and Suricata rules inside about 40 seconds of posting a file.
- Interactive Malware Prognosis:Â ANY.RUN differs from many computerized alternate choices due to the it permits you to join with the digital machine out of your browser. This dwell feature helps end zero-day vulnerabilities and developed malware that can presumably presumably salvage previous signature-based fully protection.
- Price for cash:Â ANY.RUNâs cloud-based fully nature makes it a price-effective option for businesses since your DevOps personnel doesnât hold to end any setup or beef up work.
- Most efficient for onboarding original security personnel contributors: ANY. RUNâs easy-to-use interface permits even original SOC researchers to snappily learn to survey malware and name indicators of compromise (IOCs).
Source credit : cybersecuritynews.com