Researchers Detailed How Letmeowin Harvest Credentials From Windows Systems
%20(1).webp)
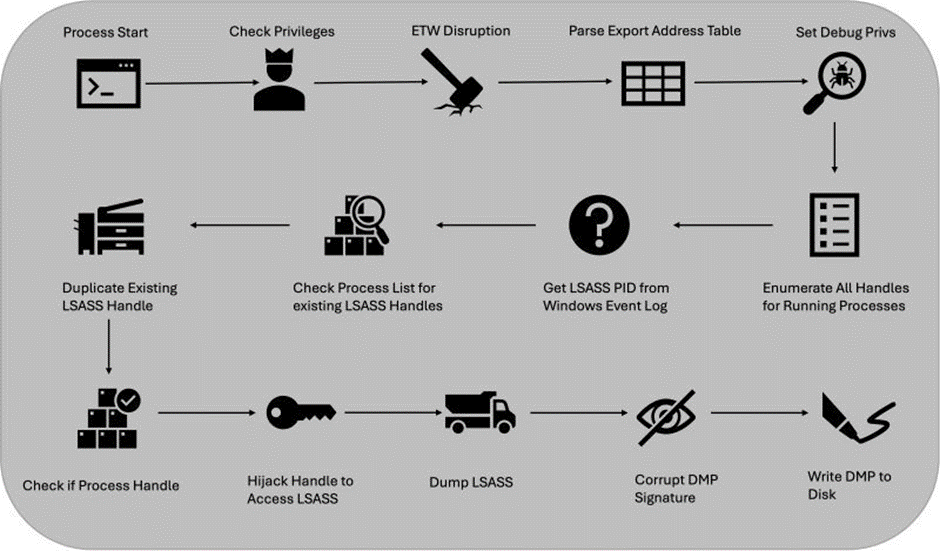
Security researcher Meowmycks unveiled a contemporary tool named LetMeowIn, designed to reap credentials from the Native Security Authority Subsystem Provider (LSASS) process on Microsoft Dwelling windows systems.
This tool has raised critical issues interior the cybersecurity community due to its evolved evasion tactics and capability to bypass day after day endpoint security products.

How LetMeowIn Works
In holding with the BinaryDefense articulate, LetMeowIn employs the MiniDumpWriteDump feature from dbghelp.dll to create a reminiscence dump of the LSASS process.
Nonetheless, moderately than writing the dump straight away to disk, it first manipulates the dump in reminiscence the usage of MINIDUMP_CALLBACK_INFORMATION.
This permits the tool to alter the dump records sooner than it’s miles written to disk, enhancing its stealth capabilities.
Obfuscation
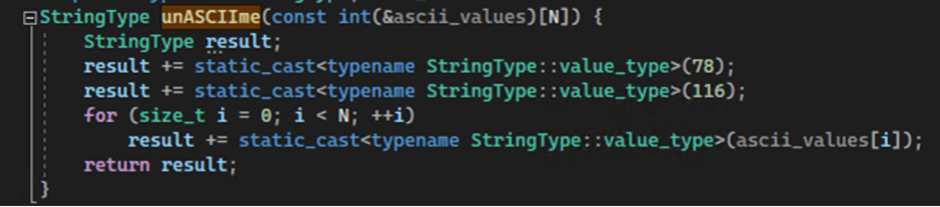
LetMeowIn uses various obfuscation the most attention-grabbing contrivance to keep away from detection.
As an example, it splits the library title “dbghelp.dll” into an array of single characters and reads it into a variable.
In the same fashion, it obfuscates Dwelling windows API functions by encoding their names with Unicode Code Aspects and storing them in an array.
A feature named unASCIIme decodes these arrays aid into the virtue names.
Oblique Syscalls
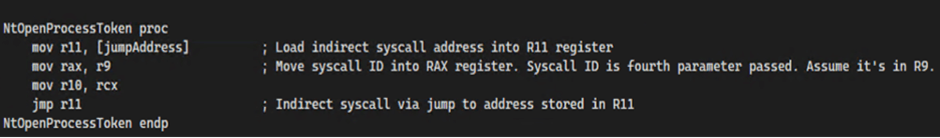
Oblique syscalls are one other evasion methodology inclined by LetMeowIn.
In position of straight away invoking design calls, the tool uses an middleman step provocative code obfuscation or redirection.
This makes it keen for long-established detection mechanisms to acknowledge the design calls.
ETW Tampering
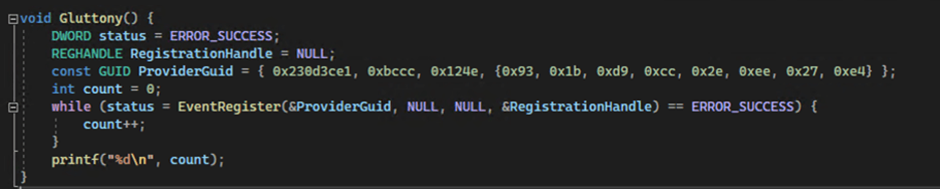
Match Tracing for Dwelling windows (ETW) is a logging mechanism endpoint security solutions utilize to amass telemetry records.
LetMeowIn includes Gluttony, which prevents ETW suppliers from gathering records by maxing out the series of suppliers a single process can gain.
This methodology changed into once first documented by a researcher identified as “acebond.”
To keep away from detection by antivirus and endpoint detection and response (EDR) solutions, LetMeowIn uses a contrivance to hijack an existing delivery tackle to the LSASS process.
Right here’s carried out the usage of the NtDuplicateObject feature. The tool then dumps the contents of LSASS to extract credentials.
Anti-prognosis for Dump Files
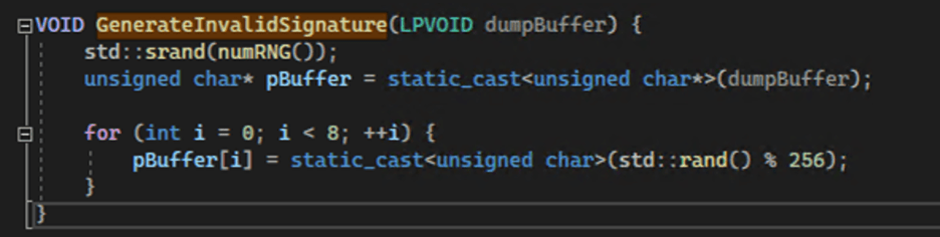
Earlier than writing the dump file to disk, LetMeowIn corrupts the file’s MDMP signature the usage of a feature known as GenerateInvalidSignature.
This prevents overall prognosis instruments from confirming whether the dump file contains credentials.
A Python script in the LetMeowIn challenge can restore the most attention-grabbing file signature, allowing instruments esteem Mimikatz to extract the credentials.
Detection Opportunities
- Direction of Introduction (4688/Sysmon 1)
One of the straight forward detection solutions is auditing process creation occasions for “LetMeowIn.exe.”
Nonetheless, defenders could maybe simply peaceful know that the process title could maybe be without problems modified.
- Image Load (Sysmon 7) for dbghelp.dll
Monitoring for the loading of dbghelp.dll can generate a Sysmon Match ID 7.
Though the binary could maybe be built statically to keep away from this event, its absence does now now not rule out suspicious exercise.
- Querying Match Log for 4608
Explore for processes querying the event log for Match ID 4608, which could maybe be at risk of make the PID of lsass.exe.
This event signifies a tool audit coverage trade and includes lsass.exe’s process ID.
- Processes with Excessive Quantity Calls to NtTraceControl
LetMeowIn registers an event supplier typically unless the most series of suppliers for a process is reached.
Monitoring for excessive-quantity syscalls to NtTraceControl by a single process can abet in detection.
- Auditing Address Manipulation (4690, 4658, 4656 occasions)
Enable auditing for tackle manipulation to grab occasions equivalent to tackle duplication, closure, and opening.
These occasions could maybe be correlated to designate actions on lsass.exe.
- Monitoring Registry Accept admission to
Video display interactions with the registry key HKLMSOFTWAREMicrosoftDwelling windows NTCurrentVersionMiniDumpAuxiliaryDlls.
Attach a System Accept admission to Defend watch over List (SACL) restricted to the SYSTEM fable to grab fetch entry to makes an strive.
- Making a Memory Dump
The reminiscence dump is on the whole written to C:tempdebug.dmp.
Look for file creation on this home, although the route could maybe be without problems changed in the code.
- Direction of Introduction for Cease Divulge
Video display for one other process creation event with the recount line C:Dwelling windowssystem32cmd.exe /c pause.
This outcomes from the design(“pause”) recount nevertheless could maybe be removed to keep away from detection.
Implementation and Monitoring Approach
Prepare Dwelling windows to log process creation occasions and configure Sysmon for enhanced monitoring.
Enable tackle manipulation auditing to log linked occasions.
Exhaust scripts or SIEM instruments to correlate ProcessID, SourceProcessId, and TargetProcessId all the perfect contrivance thru linked occasions to music actions linked with lsass.exe.
Follow a SACL on HKLMSOFTWAREMicrosoftDwelling windows NTCurrentVersionMiniDumpAuxiliaryDlls for SYSTEM-most attention-grabbing fetch entry to.
Enable Object Accept admission to auditing to grab registry fetch entry to occasions.
Video display the predefined dump file home and make utilize of heuristics or behavioral prognosis to establish reminiscence dump creation makes an strive.
The release of LetMeowIn highlights the continuing arms bustle between attackers and defenders in the cybersecurity panorama.
By working out the tactics inclined by LetMeowIn, defenders can greater put together to detect and mitigate such threats.
Source credit : cybersecuritynews.com


