Researchers Uncover A New Technique To Thwart DDoS Attack with 90% Accuracy

Recent research has confirmed a excellent 90% accuracy price in detecting traditional on-line threats and DDoS assaults, which is a valuable improvement over outdated detection suggestions.
As exclusively reported to Cyber Security Facts, the new technique operates by preserving a conclude undercover agent on the continuously shifting details superhighway site site visitors patterns.
The playbook most incessantly liable to title denial-of-service assaults, in which attackers try to bring down a domain by flooding it with requests, has been modified by scientists.
Denial-of-service threats were show camouflage on this agonize as a consequence of uneven behavior in community site site visitors and Tsallis entropy.
Specifics of the Novel Blueprint to Stop DDoS Assaults
This new technique used to be created by consultants on the Division of Vitality’s Pacific Northwest National Laboratory.
Scientist Omer Subasi from PNNL supplied the findings on August 2 on the IEEE World Conference on Cyber Security and Resilience, where the article won the award for simplest research paper supplied.
Many systems rely on a raw number known as a threshold to title DDoS assaults. A local’s defenses are activated if the preference of oldsters attempting to catch entry to it exceeds a definite threshold because it is assumed that an assault is drawing conclude.
Nonetheless, relying on a threshold exposes systems to risk.
“A threshold valid doesn’t offer vital insight or details about what is going on in your plan,” acknowledged Subasi.
“A straightforward threshold can with out agonize trot away out staunch assaults, with crucial consequences, and the defender may per chance per chance moreover not even possess in mind of what’s occurring.”
A threshold may per chance per chance moreover moreover invent fraudulent alarms, which would per chance per chance per chance moreover possess detrimental results on their bear.
The PNNL team fully refrained from the premise of thresholds to elongate detection accuracy. As but every other, the crew concentrated on the approach of entropy, a metric for plan disorder.
Researchers enlighten two measures of entropy transfer oppositely at some stage in a denial-of-service assault.
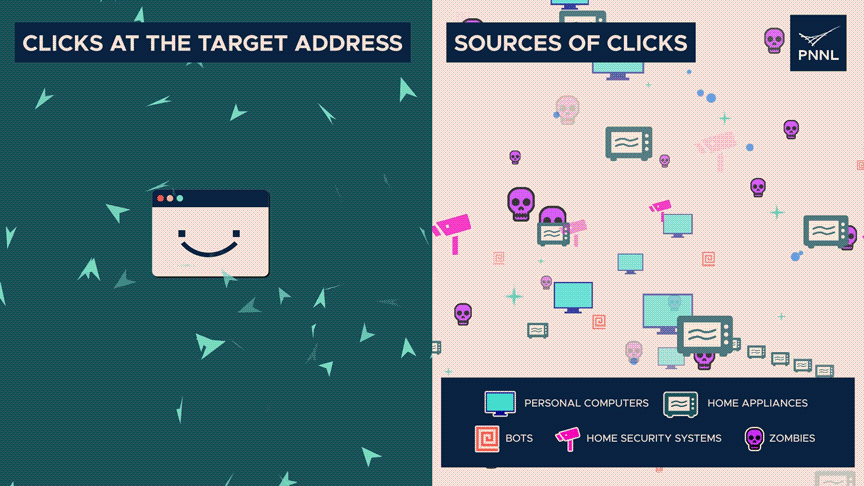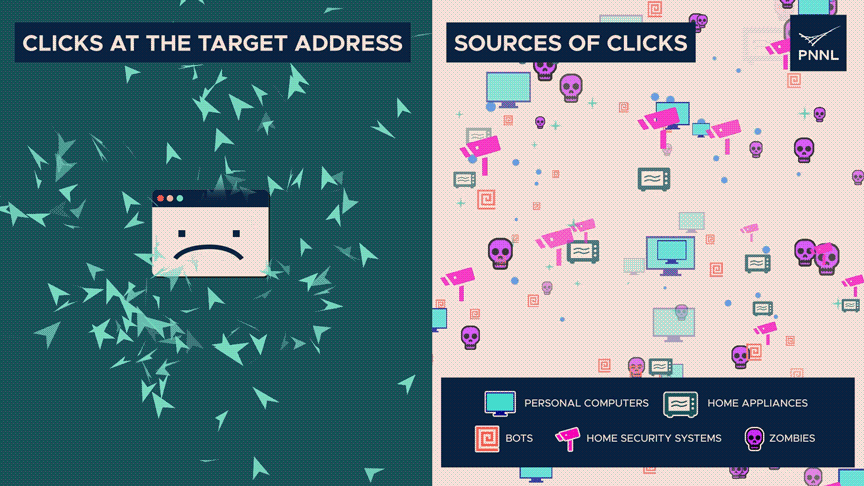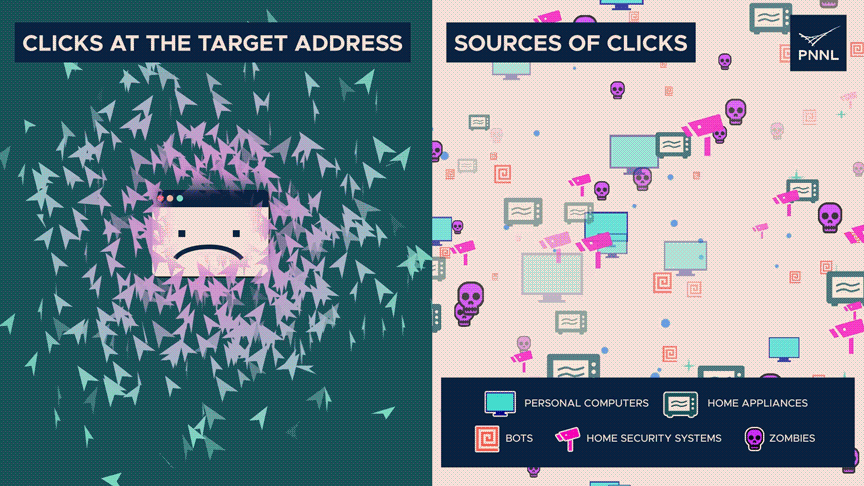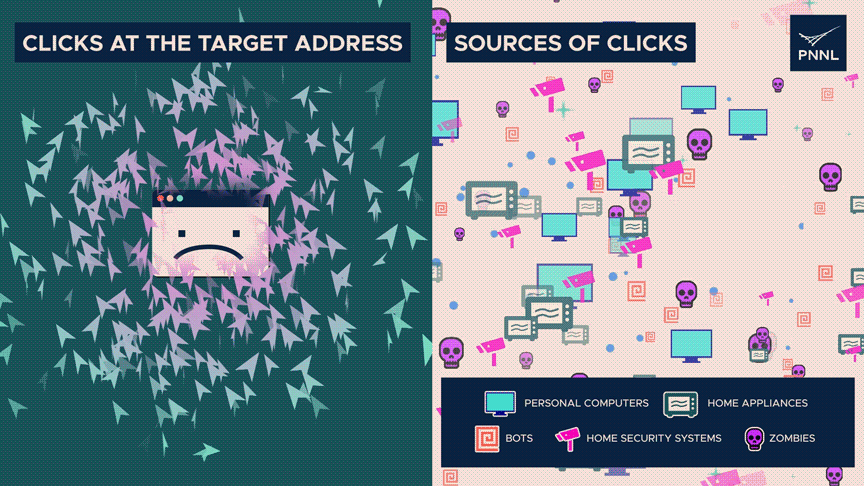
There are severely extra clicks than typical on the destination tackle, indicating unhappy entropy.
Nonetheless, the origins of those clicks—whether or not they be from staunch humans, zombies, or automated systems—are dispersed widely—high entropy. The discrepancy can gift an assault.
In tests performed by PNNL, 10 traditional algorithms wisely identified, on moderate, 52% of DOS assaults; the cease algorithm appropriately identified 62% of assaults the PNNL system precisely identified ninety nine percent of them.
To compute entropy, Subasi checked out other suggestions. A range of denial-of-service detection systems rely on the Shannon entropy system.
As but every other, Subasi susceptible a mathematical principle known as Tsallis entropy for some underlying mathematics.
The Tsallis system, basically based mostly on Subasi, is hundreds of instances extra sensitive than Shannon at identifying fraudulent alarms and distinguishing between staunch flash events like valuable details superhighway site site visitors for the World Cup and an assault.
“The PNNL resolution is automated and doesn’t require conclude oversight by a human to supply an rationalization for apart between legitimate site site visitors and an assault,” says the report.
The researchers enlighten that their program is “gentle-weight” because it valid requires a little amount of community or computational sources to attain its job.
It has been neatly-known that this differs from solutions basically based mostly on synthetic intelligence and machine learning. These suggestions steer sure of thresholds as effectively, however they moreover need plenty of coaching details.
The major investigator Kevin Barker acknowledged, “With so many extra devices and systems linked to the on-line, there are many extra alternatives than earlier than to assault systems maliciously.”
In line with reports, the team is currently having a behold into the aptitude influence that the deployment of 5G networking and the rising prevalence of the Web of Things may per chance per chance moreover possess on denial-of-service assaults.
Source credit : cybersecuritynews.com


