SEC X Account Hacked to Publish Bitcoin ETFs Approval Message
-1.webp)
In a scene ripped from a digital thriller, the U.S. The Securities and Switch Commission (SEC) saw its Twitter anecdote hijacked by an unknown entity, plunging the crypto world into a curler coaster scramble of frenzied pleasure and crushing disappointment.
The perpetrator unleashed a fabricated announcement claiming approval of Bitcoin Switch Traded Funds (ETFs), a protracted-awaited pattern that ignites eager anticipation within the cryptocurrency home.
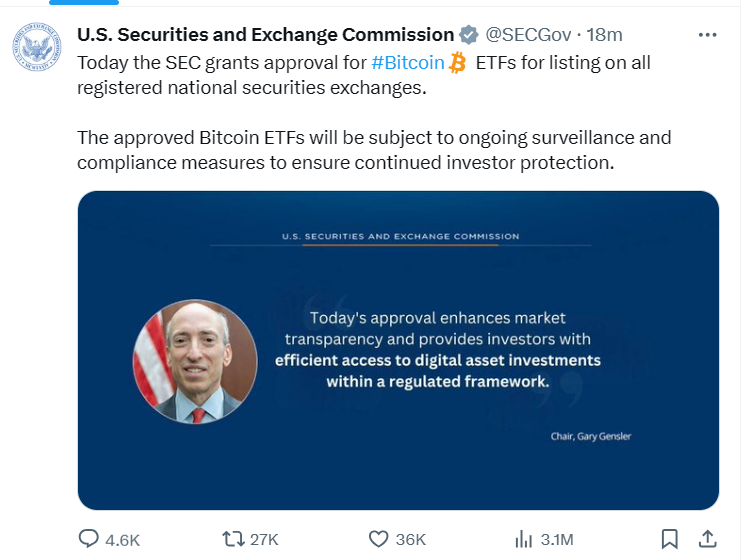
The pretend tweet, crafted to resemble an official SEC pronouncement, spread esteem wildfire by social media, fueled by its nice looking message.
Fastrack Compliance: The Route to ZERO-Vulnerability
Compounding the say are zero-day vulnerabilities esteem the MOVEit SQLi, Zimbra XSS, and 300+ such vulnerabilities that salvage chanced on each and every month. Delays in fixing these vulnerabilities lead to compliance factors, these delay will be minimized with a different characteristic on AppTrana that lets you salvage “Zero vulnerability describe” within 72 hours.
Recordsdata retail outlets scrambled to substantiate the news, propelling Bitcoin towards its dizzying height, a 25% surge fueled by unbridled investor euphoria.
Temporarily, it regarded as if regulatory hurdles had crumbled, granting Bitcoin mainstream validation and salvage entry to.
Anatomy of the Hack:
Extra investigation by X published the attacker’s modus operandi: they won retain an eye on of a phone amount related to the SEC’s anecdote by a third-occasion carrier.
X, now owned by Elon Musk, confirmed that the SEC hadn’t utilized two-element authentication, a important preventive measure, on the time of the hack. This lapse in cybersecurity protocol facilitated unauthorized salvage entry to.
Alternatively, this digital joyride used to be destined for a brutal end. The SEC hasty debunked the tweet, shattering the look of a regulatory inexperienced light.
Are attempting Kelltron’s label-efficient for gratis to assess and review the safety posture of digital programs
Source credit : cybersecuritynews.com


