Sharp Dragon Hackers Attacking Government Entities Using Cobalt Strike & Custom Backdoors
-1.webp)
The activities of the Chinese language risk actor group is legendary as Intelligent Dragon (formerly Intelligent Panda) were meticulously documented.
Since 2021, this group has been serious about extremely focused phishing campaigns, essentially specializing in Southeast Asia.
Then again, contemporary traits present a important shift in their operations, with the group now focusing on governmental organizations in Africa and the Caribbean.
Historical Context
Checkpoint Blog shows Intelligent Dragon has a historical previous of deploying numerous payloads, including VictoryDLL and the Soul framework, thru refined phishing emails.
Their modus operandi has remained constant, with a spotlight on excessive-profile targets.
Then again, the group’s contemporary activities tag a notable enlargement in their geographical focal level.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
Shift to Africa and the Caribbean
Starting in November 2023, Intelligent Dragon started focusing on governmental entities in Africa and the Caribbean.
This shift changed into once facilitated by exploiting previously compromised entities in Southeast Asia.
The group inclined extremely tailored lures linked to intergovernmental relatives to construct footholds in these sleek areas.
Cyber Activities in Africa
The first known phishing assault focusing on Africa changed into once sent from a Southeast Asian nation to an African nation in November 2023.
The lure doc, which looked as if it would perhaps well be an unswerving correspondence about industrial relatives, changed into once at risk of deploy the Cobalt Strike Beacon.
By January 2024, inform focusing on interior Africa changed into once seen, indicating profitable phishing makes an are attempting.

Cyber Activities in the Caribbean
Similarly, in December 2023, Intelligent Dragon focused a Caribbean nation the usage of a lure linked to a Caribbean Commonwealth assembly.
By January 2024, compromised electronic mail infrastructure in the Caribbean changed into once at risk of launch a broad-scale phishing advertising campaign focusing on more than one regional governments.

Technical Diagnosis
Intelligent Dragon’s an infection chain has developed since May perhaps perhaps well 2023, reflecting a more careful target choice and increased operational security (OPSEC) consciousness.
The group’s 5.t downloader now conducts thorough reconnaissance heading in the true route methods, inspecting task lists and enumerating folders to determine out doable victims more discerningly.
Cobalt Strike Payload
Intelligent Dragon’s predominant payload is now Cobalt Strike Beacon, which offers backdoor functionalities resembling C2 dialog and express execution.
This shift to publicly on hand instruments fancy Cobalt Strike indicates a refined technique to minimizing publicity.
{
"config_type": "static",
"spawnto_x64": "%windir%\sysnative\Locator.exe",
"spawnto_x86": "%windir%\syswow64\Locator.exe",
"uses_cookies": "True",
"bstagecleanup": "True",
"crypto_scheme": 0,
"proxy_behavior": "Use IE settings",
"server,get-uri": "103.146.78.152,/ajax/libs/json2/20160511/json_parse_state.js",
"http_get_header": [
"Const_header Accept: application/*, image/*, text/html",
"Const_header Accept-Language: es",
"Const_header Accept-Encoding: compress, br",
"Build Metadata",
"XOR mask w/ random key",
"Base64 URL-safe decode",
"Prepend JV6_IB4QESMW4TOIQLJRX69Q7LPGNXW594C5=",
"Build End",
"Header Cookie"
]
}
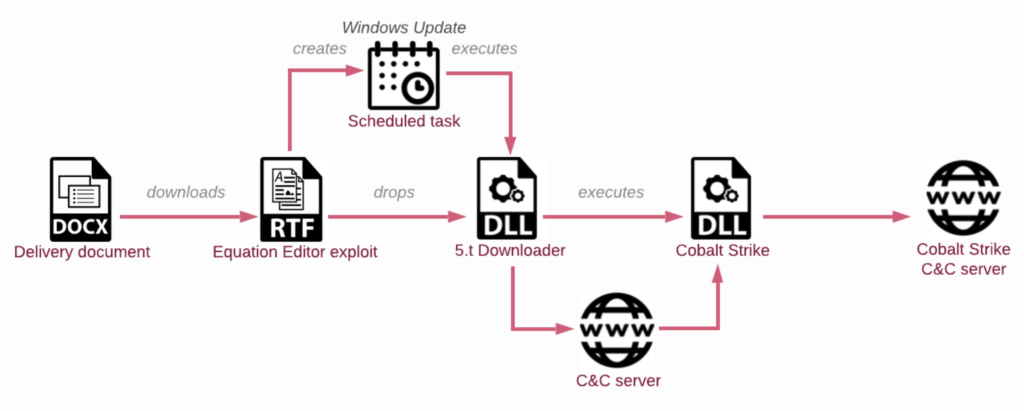
Intelligent Dragon has additionally equipped EXE-essentially essentially based 5.t loader samples, deviating from the recurring DLL-essentially essentially based loaders. This swap underscores the dynamic nature of their evolving programs.
The sleek an infection chain entails executables disguised as paperwork, which write and make the 5.t DLL loader, creating a scheduled task for persistence.
Compromised Infrastructure
Intelligent Dragon has shifted from the usage of devoted servers to compromised servers as C&C servers.
During a advertising campaign in May perhaps perhaps well 2023, the group exploited the CVE-2023-0669 vulnerability in the GoAnywhere platform, making an allowance for pre-authentication express injection.
The guidelines still from affected machines changed into once sent to addresses masquerading as belonging to the GoAnywhere carrier.
Intelligent Dragon’s strategic shift towards Africa and the Caribbean suggests a broader effort by Chinese language cyber actors to spice up their presence and affect in these areas.
This transfer, coupled with refined tactics and publicly on hand instruments, highlights the evolving nature of Chinese language risk actors.
The findings underscore the significance of sturdy cybersecurity measures to provide protection to excessive-profile organizations from such refined threats.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
Source credit : cybersecuritynews.com


