SLP Protocol Vulnerability Lets Attackers Launch Powerful 2,200x DDoS Attack

The Provider Space Protocol (SLP) has been found to have a peculiar reflective Denial-of-Provider (DoS) amplification vulnerability.
Possibility actors can exploit this vulnerability to develop large DDoS attacks with a staggering amplification of 2,200X.
Researchers at BitSight and Curesec have tracked the vulnerability as “CVE-2023-29552,” which has exposed spherical 54,000 exploitable conditions of the SLP former by over 2,000 organizations.
Possibility actors can leverage these conditions for conducting DDoS amplification attacks. Organizations worldwide have unknowingly deployed inclined devices, and here they are mentioned below:-
- Konica Minolta printers
- VMWare ESXi Hypervisors
- Planex Routers
- IBM Integrated Management Modules
Inclined SLP Cases
Right here below, we’ve mentioned all the nations with the most inclined conditions:-
- The US
- Mountainous Britain
- Japan
- Germany
- Canada
- France
- Italy
- Brazil
- The Netherlands
- Spain
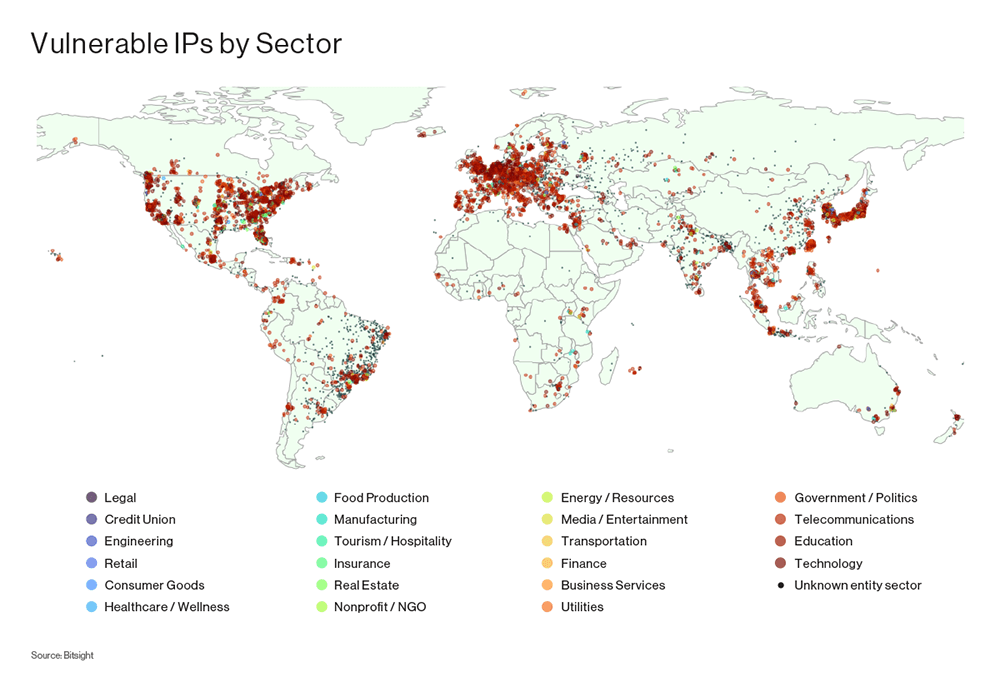
Right here the most fun component is that there are loads of Fortune 1000 companies or organizations using these inclined conditions within the following sectors:-
- Expertise
- Telecommunications
- Healthcare
- Insurance
- Finance
- Hospitality
- Transportation
Technical Diagnosis
SLP essentially facilitates the verbal change and connection between devices on LAN, an former net protocol equipped in 1997.
Whereas it does so by a provider availability system that operates on port 427 using UDP and TCP, organizations have exposed SLP on tens of thousands of devices by no contrivance designed to be exposed on the final public net over the years. Document says.
With a CVSS ranking of 8.6, CVE-2023-29552 is a vulnerability that has effects on all exploitable conditions.
Possibility actors can exploit all these inclined conditions to conduct reflective DoS amplification attacks in opposition to centered entities.
On the a hit exploitation of the vulnerability, unauthenticated attackers can manipulate the SLP server by registering arbitrary companies.
This allows them to change the pronounce and size of the server’s response and abolish a huge DoS amplification attack.
Moreover, CISA has reached out to divulge inclined vendors regarding the severity of the flaw. DoS attacks label SMBs an average of $120,000, and bigger companies face grand extra well-known financial losses as a result of elevated disruption charges.
Conventional and Reflective DoS Amplification Assault
Right here below, we’ve mentioned the important thing steps that involve in a Conventional reflective DoS amplification attack:-
- Step 1: The attacker finds an SLP server on UDP port 427.
- Step 2: The attacker spoofs a query to that provider with the victim’s IP as the beginning.
- Step 3: The attacker repeats step two as lengthy as the attack is ongoing.
Right here below, we’ve mentioned the steps that involve in a Reflective DoS amplification attack leveraging CVE-2023-29552:-
- Step 1: The attacker finds an SLP server on UDP port 427.
- Step 2: The attacker registers companies till SLP denies extra entries.
- Step 3: The attacker spoofs a query to that provider with the victim’s IP as the beginning.
- Step 4: The attacker repeats step three as lengthy as the attack is ongoing.
Possibility actors would possibly maybe utilize a couple of SLP conditions to coordinate an dependable attack; to abolish so; they would possibly maybe well well merely flood their targets with substantial site visitors.
Advice
The following suggestions desires to be adopted to guard the property of your organization from ability exploitation:-
- On the methods which will most definitely be exposed, be definite that that to disable the SLP.
- Be definite to successfully configure a firewall, as this will filter the site visitors on UDP and TCP port 427.
- Organizations must always have an incident response contrivance in place.
- Be definite one and all the sturdy security measures and obtain entry to controls are performed.
Constructing Your Malware Defense Approach – Fetch Free E-Book
Source credit : cybersecuritynews.com

