SugarGh0st RAT Attacking Organizations & Individuals in AI Research
.webp)
The cybersecurity company Proofpoint has chanced on a recent operation the use of the SugarGh0st Distant Secure admission to Trojan (RAT) that’s going after AI evaluate organizations in the United States.
The operation, linked to a possibility cluster identified as UNK_SweetSpecter, went after companies, universities, and authorities agencies.

Attack Potential: Emails with AI-themed bait
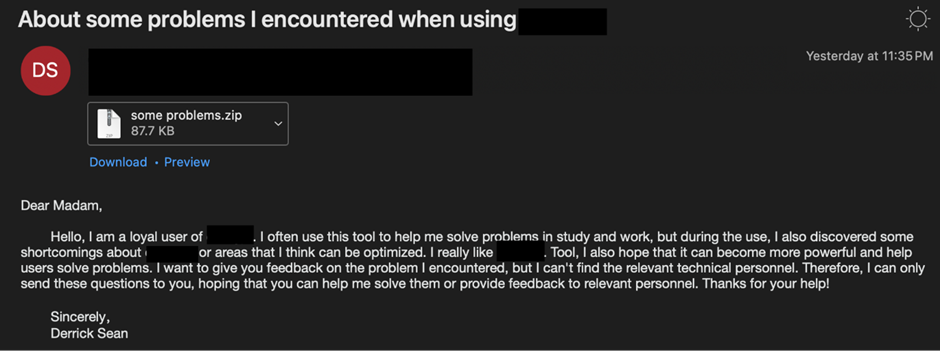
UNK_SweetSpecter’s campaign in Could perchance 2024 outdated a free electronic mail myth to ship emails with AI-themed traps to of us that would very well be victims. These emails had a zipper archive file to fetch people to commence it.
The zip file dropped an LNK shortcut file that outdated a JavaScript dropper as quickly as it became launched.
This dropper is then set apart in the SugarGh0st RAT code.
The assault chain became very equal to a approach that Cisco Talos had already reported.
It integrated a faux doc, an ActiveX utility for sideloading, and a base64-encrypted binary file.
The JavaScript dropper became set apart in a library that later let JavaScript bustle a multi-stage shellcode, which became what released the SugarGh0st payload.
This payload became intended for records exfiltration, expose and private an eye fixed on (C2) heartbeat protocol, and keylogging.
Analysis of Networks and Attribution
Proofpoint’s take into myth of the network confirmed that UNK_SweetSpecter had moved its C2 communications to recent domains, akin to accounts. gommask[.]on-line, which shared internet internet hosting with domains that had already been reported.
It looks care for AS142032 is the set apart the infrastructure for these activities is found.
Cisco Talos’s first take into myth at SugarGh0st RAT instructed that it became outdated by possibility actors who spoke Chinese language.
Proofpoint’s take into myth of earlier UNK_SweetSpecter campaigns proved these errors in the language.
Proofpoint isn’t obvious the campaigns had been directed at a explicit narrate purpose.
Silent, the truth that they had been very explicit and centered on AI consultants suggests that the authorities could well had been making an strive to fetch private records about generative AI.
A latest Reuters memoir mentioned that the U.S. authorities is stepping up its efforts to forestall China from the use of generative AI.
This campaign goes on simultaneously, which makes it more likely that cybercriminals with ties to China will target of us which have access to AI technologies to assist them attain their snort targets.
Why it’s fundamental
Enterprise defenders must music explicit possibility actors, which is sophisticated but valuable.
This campaign reveals how fundamental it’s to space baselines to detect malicious behavior, even if the possibility isn’t at the moment share of an organization’s possibility model.
The truth that regular instruments are outdated as the 1st step in highly centered spearphishing campaigns reveals how fundamental it’s to be cautious and have solid cybersecurity map in situation.
The Yahoo! Paranoids Superior Cyber Threats Personnel and Proofpoint’s collaboration became very vital in finding this operation.
As cyber threats swap, partnerships care for these and thorough possibility evaluate will continue to be valuable for safeguarding in opposition to complex attacks.
Indicators of compromise
| Indicator | Description | First Noticed |
| da749785033087ca5d47ee65aef2818d4ed81ef217bfd4bc07be2d0bf105b1bf | SHA256 some complications.zip |
2024-05-08 |
| 71f5ce42714289658200739ce0bbe439f6ef6fe77a5f6757b1cf21200fc59af7 | SHA256 some complications.lnk |
2024-05-08 |
| fc779f02a40948568321d7f11b5432676e2be65f037acfed344b36cc3dac16fc | SHA2256 ~235232302.js |
2024-05-08 |
| 4ef3a6703abc6b2b8e2cac3031c1e5b86fe8b377fde92737349ee52bd2604379 | SHA256 libeay32.dll |
2022-02-18 |
| feae7b2b79c533a522343ac9e1aa7f8a2cdf38691fbd333537cb15dd2ee9397e | SHA256 some_problems.docx |
2024-05-08 |
| myth.gommask[.]on-line | SugarGh0st RAT C2 Area | 2024-05-08 |
| 43.242.203[.]115 | SugarGh0st RAT C2 IP | 2024-05-08 |
Source credit : cybersecuritynews.com

