TA450 Hackers Uses Embedded Links in PDF Attachments to Attack Windows

In a concerning mumble in cyber battle, the Iran-aligned threat actor identified as TA450, additionally known by aliases equivalent to MuddyWater, Mango Sandstorm, and Static Kitten, has been reported to use a brand fresh procedure in its phishing campaigns.
Proofpoint researchers have identified a shift within the neighborhood’s tactics, which now possess embedding malicious hyperlinks internal PDF attachments sent to workers of world manufacturing, technology, and data security companies, with a particular take care of Israeli targets.

The Evolution of TA450’s Methods
Traditionally, TA450 has been identified for its direct attain of along side malicious hyperlinks for the period of the physique of phishing emails.
Nonetheless, in a marketing campaign that began on March 7, 2024, and endured via the week of March 11, the neighborhood has added an additional layer to its assault chain by the use of PDF attachments as a vector for turning in these flawed hyperlinks.
Integrate ANY.RUN in Your Firm for Efficient Malware Analysis
Are you from SOC, Probability Examine, or DFIR departments? If that is the case, it’s likely you’ll maybe be in a space to be a part of an net community of 400,000 self sustaining security researchers:
- Exact-time Detection
- Interactive Malware Analysis
- Easy to Be taught by Recent Security Crew participants
- Derive detailed experiences with maximum data
- Residing Up Digital Machine in Linux & all Windows OS Variations
- Work along with Malware Safely
Whenever you wish to must take a look at all these parts now with entirely free earn admission to to the sandbox:
This marks the first time Proofpoint researchers have noticed the kind of procedure from TA450, indicating a vital pivot within the neighborhood’s modus operandi.
The Social Engineering Lure
Doubtlessly the most up-to-date phishing attempts have utilized a pay-linked social engineering trap, a tactic designed to use human psychology by promising financial incentives.
This kind has proven effective in focusing on Israeli workers, a demographic that TA450 has been actively pursuing since on the least October 2023, following the onset of the Israel-Hamas battle.
The marketing campaign’s success is partly attributable to the use of sender email accounts that match the trap’s disclose material, adding a layer of authenticity to the phishing emails.
The shift in TA450’s tactics is largely alarming given the neighborhood’s alignment with Iran’s Ministry of Intelligence and Security, as attributed by the United States Cyber Train in January 2022.
The utilization of PDF attachments to veil malicious URLs represents an escalation within the sophistication of TA450’s attacks, posing a heightened threat to organizations and their workers.
The Campaign’s Influence
The marketing campaign’s affect is to now not be underestimated. By sending extra than one phishing emails with PDF attachments to the identical targets, TA450 will increase the chance of a hit infiltration.
Once an unsuspecting employee clicks on the embedded link, they are ended in a ZIP archive via Onehub, which then ends within the download of remote administration application.

This application grants TA450 earn admission to to the victim’s machine, allowing for attainable data theft, espionage, or additional malicious activities.
Are you from SOC and DFIR Teams? – Analyse Malware Incidents & earn are dwelling Derive admission to with ANY.RUN -> Birth Now for Free.
Indicators of Compromise (IOCs)
| Indicator | Kind |
| salary |
Example of compromised email sender |
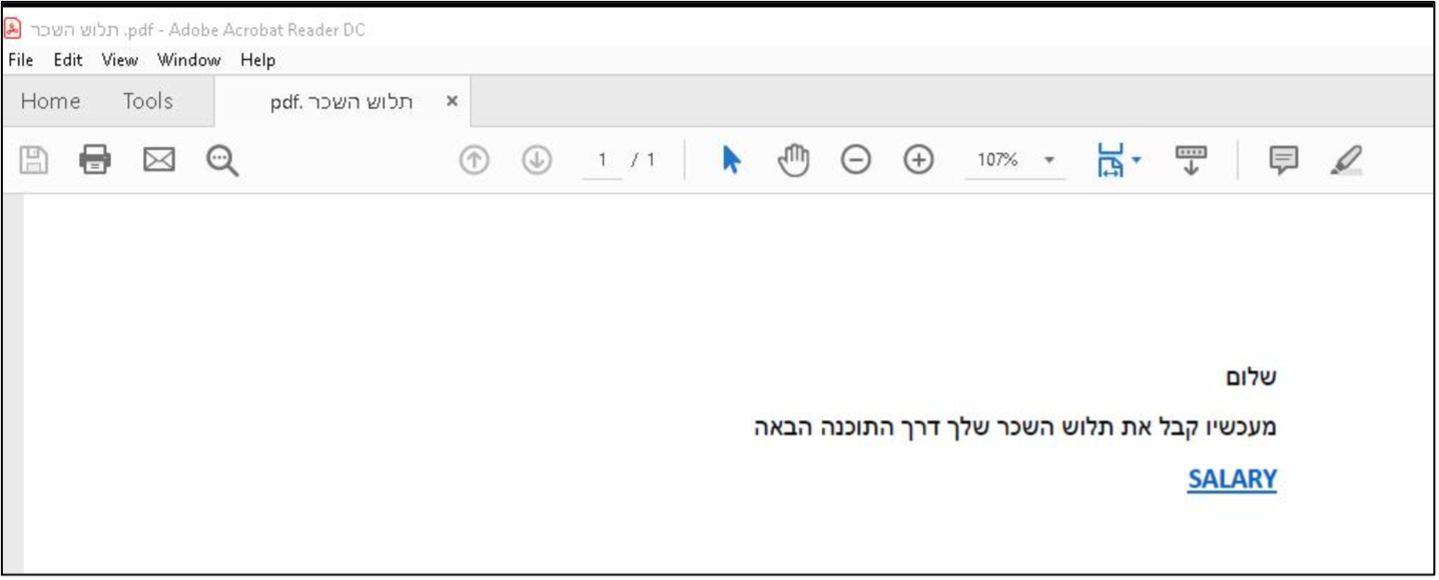
| תלושי השכר (Machine translation: Pay creep) | E-mail field |
| תלוש שכר לחודש 02/2024 (Machine translation: Pay creep for the month 02/2024) | E-mail field |
| סיסמה לתלוש שכר (Machine translation: Pay creep password) | E-mail field |
| תלוש השכר .pdf (Machine translation: Pay creep) | Doc title |
| dee6494e69c6e7289cf3f332e2867662958fa82f819615597e88c16c967a25a9 | SHA256 (PDF) |
| hxxp://ws.onehub[.]com/files/[alphanumericidentifier] | Example malicious URL |
| hxxps://salary.egnyte[.]com/[alphanumericidentifier] | Example malicious URL |
| hxxps://ln5.sync[.]com/[alphanumericidentifier] | Example malicious URL |
| hxxps://terabox[.]com/s/[alphanumericidentifier] | Example malicious URL |
| cc4cc20b558096855c5d492f7a79b160a809355798be2b824525c98964450492 | SHA256 (salary.zip) |
| e89f48a7351c01cbf2f8e31c65a67f76a5ead689bb11e9d4918090a165d4425f | SHA256 (salary.msi) |
Source credit : cybersecuritynews.com


