Tainted Password-Cracking Software Used to Deliver Sality Malware

Researchers from Dragos chanced on a smaller in-scale methodology focused on industrial engineers and operators right thru their standard vulnerability evaluation.
Specialists articulate risk actors frail multiple accounts across several social media platforms to advertise password-cracking application for Programmable Good judgment Controller (PLC), Human-Machine Interface (HMI), and finishing up recordsdata.
Specialists from Dragos behold the distress affecting DirectLogic PLCs from Automation Instruct and chanced on that the ‘cracking application’ used to be exploiting a known vulnerability within the instrument to extract the password.
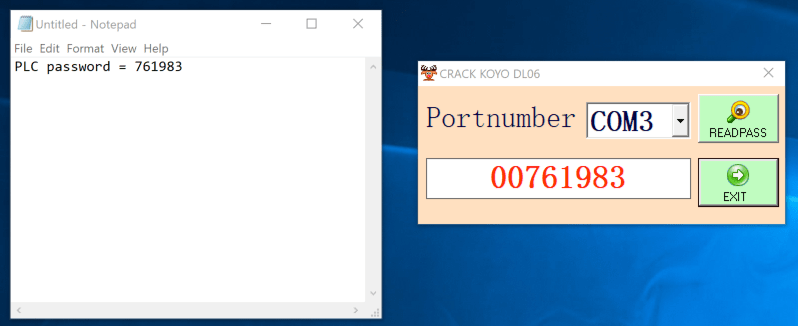
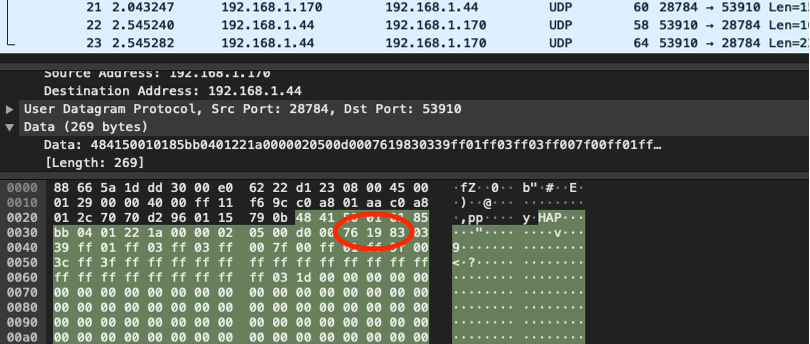
“It is chanced on that this exploit would no longer crack a scrambled model of the password as traditionally considered in popular exploitation frameworks. As a substitute, a particular byte sequence is shipped by the malware dropper to a COM port”, says Dragos.
The malware holds serial-completely model of the exploit that requires the user to non-public a bid serial connection from an Engineering Workstation (EWS) to the PLC. This vulnerability is tracked as (CVE-2022-2003) and used to be responsibly disclosed to Automation Instruct.
Sality Malware
Sality refers to an frail, remarkable household of viruses that infect executable recordsdata. Trendy Sality variants can, among numerous issues, act as a backdoor and join contaminated machines to a botnet.
Sality is a eye-to-eye botnet for disbursed computing tasks comparable to password cracking and cryptocurrency mining. A Sality infection may perhaps well risk a long way off catch correct of entry to to a EWS by an unknown adversary.
It employs route of injection and recordsdata infection to maintain persistence on the host. It abuses Window’s autorun efficiency to spread copies of itself over Universal Serial Bus (USB), network shares, and external storage drives.
Dragos experts articulate it is an atmosphere pleasant scheme to take cryptocurrency from customers looking out for to transfer funds and can increase our self belief that the adversary is financially motivated. The Sality malware uses a kernel driver to maintain away from detection, it furthermore begins a carrier to call processes associated with seemingly security products, and extinguish them.
Therefore, “Dragos completely tested the DirectLogic-focused on malware. Nevertheless, an initial dynamic diagnosis of a pair of numerous samples signifies they furthermore possess malware. Several internet sites and multiple social media accounts exist all touting their password “crackers”.
That you may perhaps note us on Linkedin, Twitter, Fb for every day Cybersecurity updates.
Source credit : cybersecuritynews.com


