The Future of Email Security With AI : Guide To Combat Sophisticated Email Threats 2023
The Contrivance forward for Email Security With AI : Manual To Combat Refined Email Threats 2023
The precautions and tactics which had been set up in discipline for the protection of electronic mail messages from unauthorized collect admission to, interception or manipulation is considered electronic mail security.
This contains the protection of confidential knowledge, integrity, and availability of electronic mail communications while on the the same time complying with cyber security threats admire unsolicited mail, phishing assaults, malware, or knowledge breaches.
Encryption, authentication, unsolicited mail filtering, phishing security, malware detection, knowledge loss prevention, and user awareness are a entire differ of disciplines that quilt the subject of electronic mail security.
Other folks and organizations can absorb the advantage of the protection of confidentiality, integrity, or accessibility of their electronic mail messages, as effectively as mitigating risks to knowledge replace if they apply a comprehensive space of e.g. mail security features.
Email security is of paramount significance resulting from the following reasons:
- Confidentiality: With out enough electronic mail security features in discipline, unauthorized folks or organizations can intercept and collect admission to this recordsdata, leading to privacy violations, identity theft, or industry espionage.
- Data Protection and Compliance: Ample electronic mail security features serve make certain compliance with lawful regulations, such because the Health Insurance coverage Portability and Accountability Act (HIPAA) in the healthcare industry.
- Intellectual Property Protection: In tell to supply protection to the competitive advantage and innovation of an enterprise, actual electronic mail security safeguards the firm’s necessary intellectual property property equivalent to blueprints, patents, etc. against unauthorized collect admission to or theft.
- Industry Continuity: A breach in electronic mail security can disrupt usual operations, leading to monetary losses, reputational hurt, and loss of customer have faith.
- Phishing and Malware Defense: Efficient electronic mail security solutions can acknowledge and filter phishing emails, shielding employees individuals and folks from con artists and unintentional system compromise.
- Unsolicited mail Administration: Implementing unsolicited mail filtering tactics helps decided up electronic mail inbox congestion, enabling users to steal stamp to necessary correspondence and reducing the risk of coming into contact with perilous knowledge.
- Recognition Protection: The hazard of fixing into all for gloomy actions is decreased by utilizing sturdy electronic mail security features, equivalent to authentication procedures and encryption, defending recognition and trustworthiness.
Being concerned About Refined Email Threats? â Deploy Email Managed Detection & Response in Your IT Atmosphere.
Evolving Email Menace Landscape: Challenges and Risks
Organizations and folk ought to handle a series of risks and challenges posed by the changing electronic mail threat landscape in tell to preserve efficient electronic mail security.
Expend a stable electronic mail security approach to handle the flaws and decrease the hazards in tell to invent this. The total electronic mail security platform Trustifi presents a series of alternate choices to beef up your electronic mail security.
The notable challenges and risks that portray electronic mail threats are listed beneath:
Refined Phishing Assaults: Cybercriminals exercise evolved social engineering tactics, establishing highly convincing phishing emails that mimic first rate organizations or folk.
By detecting phishing makes an strive and malicious relate material, electronic mail security solutions admire Trustifi serve users steer decided of falling sufferer to scams.
Industry Email Compromise (BEC): Industry electronic mail compromise, assuredly assuredly called CEO fraud or whaling, assaults companies by impersonating senior executives or first rate partners.
BEC assaults exercise a approach called social engineering in tell to steal advantage of the authority and have faith within the firm.
Malware and Ransomware: Email is the most frequent approach of propagating malware or ransomware to an unknown user.
Organizations can count on solutions admire Trustifi to detect and forestall these forms of Phishing as effectively as Malware threats, with the serve of fashionable technologies.
Insider Threats: Insider threats absorb folk within a firm misusing their licensed collect admission to to compromise electronic mail security.
This could perhaps presumably consist of deliberately leaking sensitive knowledge, conducting unauthorized actions, or collaborating in deceptive actions utilizing their electronic mail accounts.
Cell Method Vulnerabilities: Cell devices could perhaps presumably perhaps lack security features, making them more at misfortune of assaults. Misplaced or stolen devices can lead to unauthorized collect admission to to electronic mail accounts and likely knowledge breaches.
Compliance and Regulatory Challenges: To present protection to sensitive knowledge, companies ought to agree to a complete lot of rules and legal pointers, such because the Customary Data Protection Laws (GDPR) and industry-connected regulations.
Organizations ought to adopt efficient incident response plans, on a traditional foundation note electronic mail net site visitors for anomalies, and preserve as a lot as this point on rising threats to preserve sooner than the evolving electronic mail threat landscape with AI-powered solutions admire Trustifi.
What AI Powered in Email Security
AI-powered technology plays a notable role in making improvements to usual electronic mail security by taking advantage of evolved algorithms and machine studying tactics.
AI algorithms can analyze spacious quantities of knowledge and name patterns, anomalies, indicators of malicious exercise, etc.
This permits AI-powered systems to proactively block and forestall such threats from reaching users’ inboxes. as an illustration, utilizes AI algorithms to assemble sturdy threat intelligence and proactive detection, ensuring doubtlessly gloomy emails are known and intercepted.
70% of world employees absorb noticed a surge in the frequency of rip-off emails and texts in the outdated couple of months.
AI-powered technology also can furthermore analyze user habits, electronic mail relate material, and verbal replace patterns to verify a baseline of usual exercise.
By step by step monitoring and studying from these patterns, the algorithms can name anomalies that could point to suspicious or malicious habits.
To illustrate, if an electronic mail tale all of sudden starts sending an surprisingly high quantity of emails or displays odd patterns of exercise, AI can flag it as a likely compromise.
Trustifi employs AI algorithms to detect unauthorized collect admission to, compromised accounts, or odd electronic mail exercise, alerting users to security risks.
AI-powered Natural Language Processing algorithms can analyze the relate material of emails to name doubtlessly malicious or suspicious aspects.
These algorithms can realize and account for the context and intent of electronic mail communications, enabling them to detect hidden phishing URLs, unfounded language, or malicious attachments.
Because the algorithms analyze spacious volumes of electronic mail knowledge, it permits them to adapt their threat detection capabilities and preserve sooner than evolving electronic mail security challenges.
AI-powered capabilities serve mitigate the hazards connected to electronic mail-primarily primarily based mostly assaults, supply protection to sensitive knowledge, and make decided a safer electronic mail verbal replace atmosphere.
The Role of Email Security Companies With AI
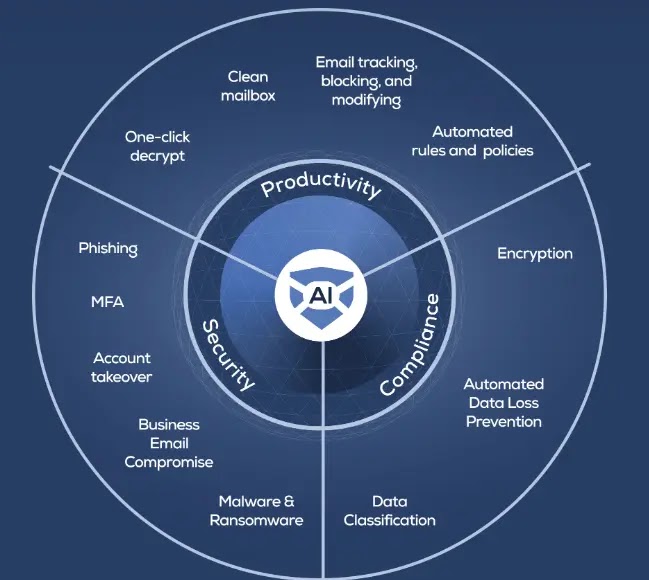
Email security services (ESPs) play a genuinely necessary role in ensuring electronic mail security for organizations and folk. ESPs supply a differ of solutions and parts to supply protection to against electronic mail-primarily primarily based mostly threats and create a stable verbal replace atmosphere.
Trustifi, as an illustration of an ESP, exemplifies the role of ESPs in electronic mail security.
With the rising sophistication of phishing assaults and malware threats, ESPs exercise evolved technologies to detect and forestall these risks.
It contains precise-time scanning and prognosis of electronic mail relate material, attachments, and hyperlinks to name and block suspicious emails.
ESPs admire Trustifi provide electronic mail tracking that enables senders to receive notifications when their emails are opened or be taught, bettering transparency and accountability.
To boot they incorporate efficient knowledge loss prevention (DLP) measures. It scans electronic mail relate material for predefined patterns or sensitive knowledge forms, equivalent to bank card numbers or social security numbers, and applies applicable security controls, equivalent to encryption or collect admission to restrictions, to conclude knowledge breaches.
ESPs exercise evolved algorithms and technologies to analyze electronic mail relate material, sender recognition, and a form of things to name and block unsolicited mail emails.
By enforcing highly efficient unsolicited mail filters, ESPs admire Trustifi can conclude unwanted and doubtlessly malicious emails from reaching users’ inboxes, reducing the misfortune of falling sufferer to scams or malware.
ESPs assuredly provide encryption mechanisms, equivalent to Transport Layer Security (TLS) and Stable/Multipurpose Net Mail Extensions (S/MIME), to encrypt electronic mail messages and attachments.
Trustifi, as an illustration, presents cease-to-cease electronic mail encryption, providing a further layer of security for sensitive communications.
Furthermore, ESPs deploy stable electronic mail gateways to intercept and analyze incoming and outgoing electronic mail net site visitors. These gateways act as a barrier between the electronic mail server and exterior networks, scanning electronic mail relate material for threats and vulnerabilities.
By enforcing stable electronic mail gateways, ESPs admire Trustifi can detect and block malicious emails, battling them from reaching the intended recipients and reducing the misfortune of electronic mail-primarily primarily based mostly assaults.
Key Challenges in Email Security: Addressing Vulnerabilities
Email security faces diversified key challenges that ought to be addressed to substantiate the protection of sensitive knowledge and mitigate the hazards connected to cyber threats.
Trustifi, as an electronic mail security provider leveraging AI-powered technology, presents many solutions to address these challenges.
Phishing remains a prevalent misfortune, with cybercriminals making an strive to trick users into divulging sensitive knowledge.
AI-powered solutions admire Trustifi.com use evolved algorithms to analyze electronic mail relate material, URLs, and sender recognition to name and block phishing makes an strive.
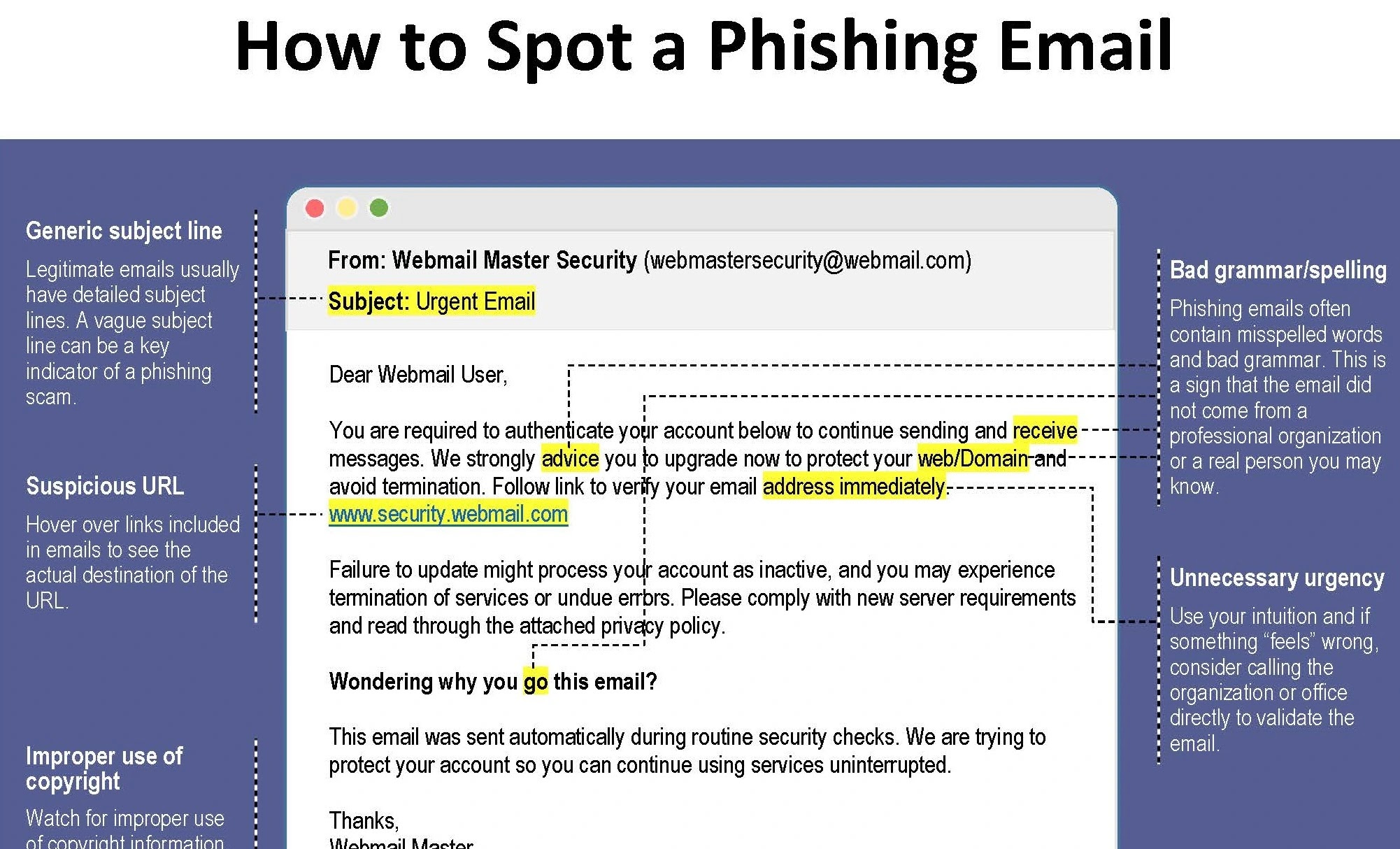
Emails are frequently weak to bring malware and ransomware, which is ready to compromise systems and recordsdata.
AI-powered electronic mail security solutions can name malicious attachments, hyperlinks, and suspicious habits indicative of malware or ransomware.
By employing machine studying tactics to detect anomalies in electronic mail communications, Trustifi.com helps conclude users from falling sufferer to phishing assaults.
Trustifi utilizes AI algorithms to detect and block such threats, ensuring that users’ systems and recordsdata remain protected against malware infections and ransomware assaults.
Stopping unauthorized collect admission to to sensitive knowledge and addressing the misfortune of knowledge leakage is required.
AI-powered electronic mail security solutions exercise tactics admire knowledge loss prevention and user habits prognosis to name and forestall the unauthorized transmission of knowledge.
Trustifi.com’s AI algorithms note electronic mail exercise, detect likely leaks, and provide precise-time signals to mitigate the misfortune of unauthorized collect admission to and leakage.
AI-powered solutions can note user habits, name odd exercise, and detect likely insider threats. Compliance with regulatory requirements and industry requirements is required for organizations.
AI-powered electronic mail security solutions also can furthermore support in assembly compliance obligations by providing parts equivalent to electronic mail archiving, tamper-proof certified electronic mail transport, and stable electronic mail storage.
AI algorithms enable the detection of phishing makes an strive, malware threats, knowledge leakage, insider threats, and enhance compliance requirements.
With the chronic studying capabilities of AI, ESPs admire Trustifi evolve their threat detection mechanisms to preserve sooner than rising electronic mail security risks and provide users with a sturdy defense against cyber threats.
Deploy Developed AI-Powered Email Security Solution
Implementing AI-Powered Email security solutions “Trustifi” can stable your industry from todayâs most awful electronic mail threats, equivalent to Email Tracking, Blocking off, Editing, Phishing, Yarn Rob Over, Industry Email Compromise, Malware & Ransomware
Future Traits in Email Security
Email security is an ever-evolving discipline, and as technology advances and contemporary threats emerge, electronic mail security features ought to also evolve.
To preserve tempo with hackers, organizations need AI-primarily primarily based mostly threat detection and response technology to protect against identified, rising, and never-sooner than-seen electronic mail-borne threats.
AI and machine studying technologies can serve to name patterns and anomalies in electronic mail net site visitors, which is ready to be weak to detect and forestall assaults equivalent to phishing, malware, and unsolicited mail.
As these technologies change into more evolved, they’ll likely change into more broadly weak in electronic mail security.
Email security is lawful one section of a firm’s general security strategy. Within the extinguish, lets test bigger integration between electronic mail security and a form of security systems, equivalent to firewalls, intrusion detection systems, and security knowledge and tournament management (SIEM) platforms, to assemble a more comprehensive capacity to security.
With the rising significance of knowledge security and privacy regulations, equivalent to GDPR and CCPA, organizations will ought to point of curiosity more on securing sensitive knowledge of their emails.
This can consist of enforcing encryption, collect admission to controls, and recordsdata loss prevention (DLP) technologies.
Used authentication systems, equivalent to passwords and two-component authentication, are changing into less stable as attackers catch contemporary ways to steal credentials.
Within the extinguish, lets test more evolved authentication systems, equivalent to biometrics and behavioral authentication, to assemble greater security.
The adoption of zero-have faith security fashions is gaining momentum and ought to play a notable role in securing electronic mail communications.
Zero-have faith security is an capacity that assumes no have faith, even for users and devices in the end of the within network.
It emphasizes accurate verification and strict collect admission to controls to supply protection to sensitive knowledge.
Within the context of electronic mail security, a zero-have faith model requires authentication and authorization for every collect admission to demand, no topic the user’s plan or network.
This means that users and devices are no longer automatically depended on consistent with their network plan nonetheless ought to authenticate themselves sooner than gaining collect admission to to electronic mail systems and recordsdata.
Implementing AI-Powered Email security solutions can stable your industry from todayâs most awful electronic mail threats, equivalent to Email Tracking, Blocking off, Editing, Phishing, Yarn Rob Over, Industry Email Compromise, Malware & Ransomware â
Furthermore Study: Who Is the Target of Phishing Scams?
Source credit : cybersecuritynews.com






