Threat Actor Server Exposed: Nmap, SQLMap & Backdoor Used For Hacking
%20(1).webp)
The Analysis Team has identified an exposed web server dilapidated to target the Taiwanese Parkway Bureau and a neighborhood data center.
The server’s administrator employed open-source instruments akin to Nmap, SQLMap, and the backdoor BlueShell to behavior their activities.
This discovery highlights the ongoing possibility to authorities companies and serious infrastructure in Taiwan.
The Preliminary Discovery: Exposed Web Server & Instruments
Hunt researchers uncovered a publicly accessible web server at IP handle 103.98.73.189:8080, positioned in Taiwan.
The server, operating a Python-primarily based fully web server (SimpleHTTP/0.6 Python/3.8.2), modified into temporarily exposed before the possibility actor seemingly realized the mistake.
The usage of Hunt’s Open Directory Search characteristic, the crew downloaded recordsdata from this server to analyze the possibility actor’s ways.
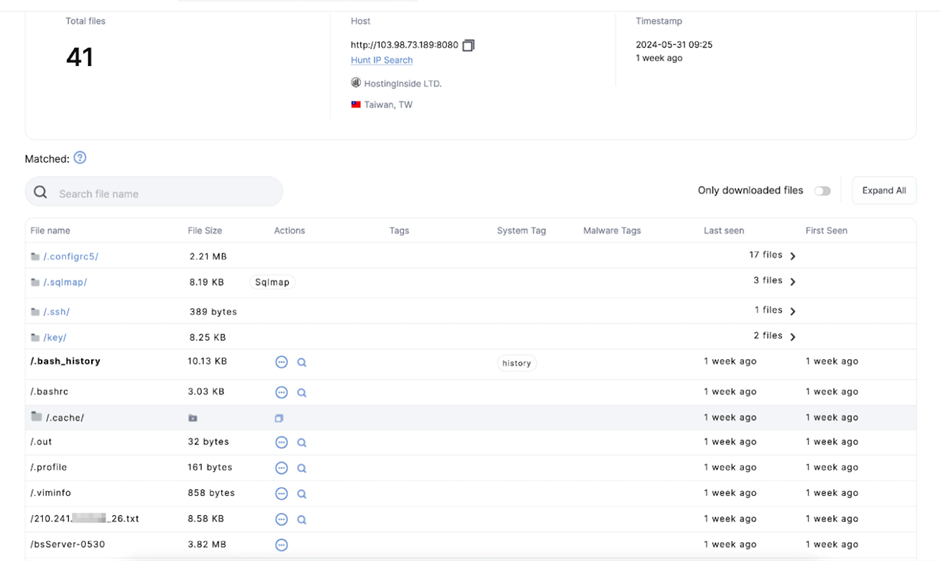
SQLMap and Nmap Utilization
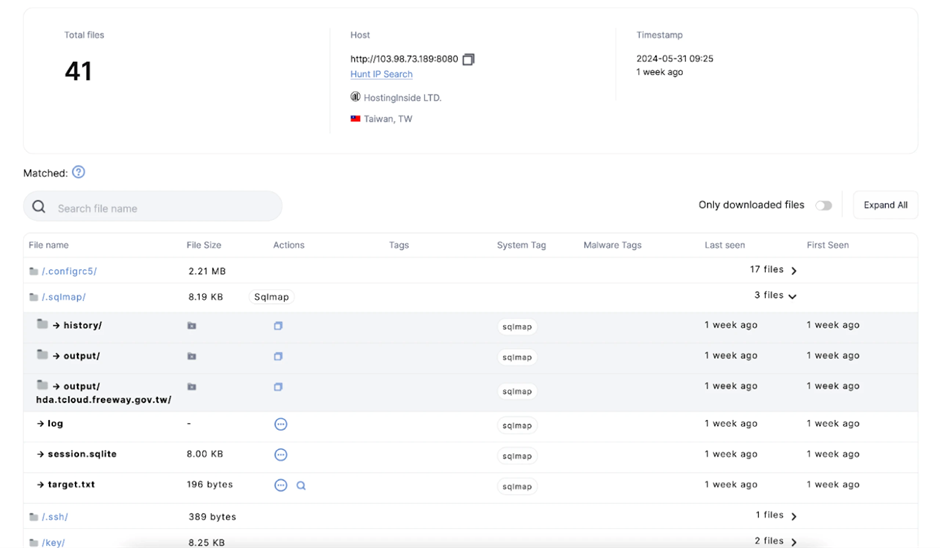
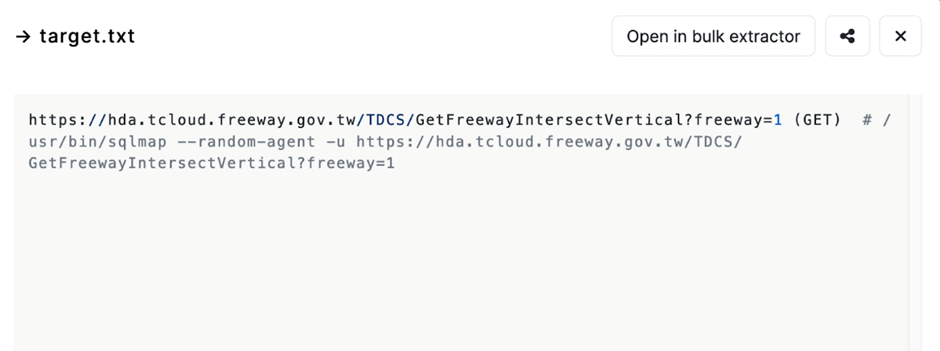
The possibility actor dilapidated SQLMap to scan for vulnerabilities within a subdomain of the freeway.gov.tw server, a legit Taiwanese authorities web map.
Key recordsdata akin to the log, session.sqlite, and target.txt had been efficiently downloaded, offering insights into the attacker’s suggestions.
Furthermore, Nmap modified into dilapidated to scan for open ports within a /26 network associated with a Taiwanese data center.
Whereas obfuscated for safety reasons, the scan results point out a scientific plan to identifying network vulnerabilities.
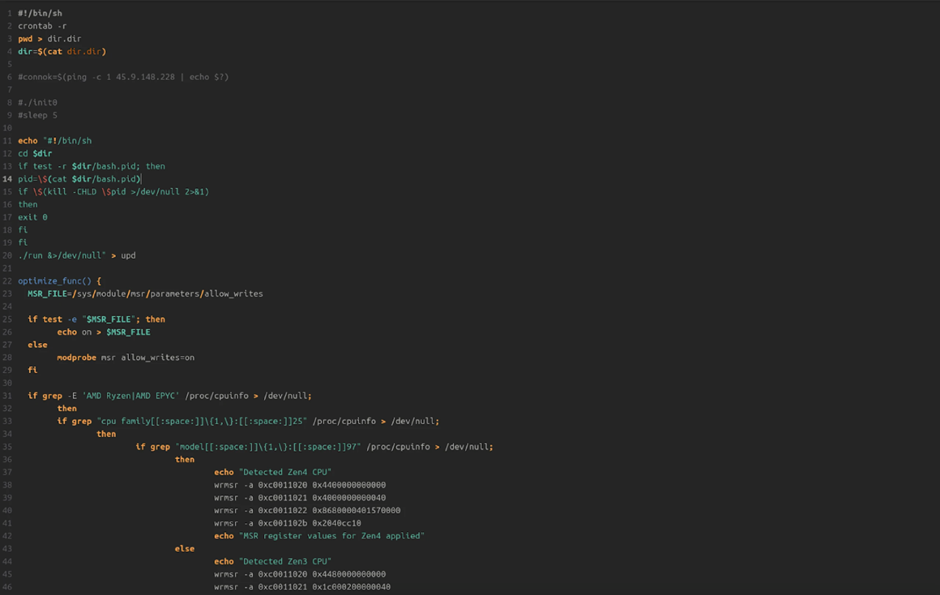
Evolved Bash Scripts and BlueShell Backdoor
The server contained more than one bash recordsdata within the ./configrc5 directory. One necessary script, named “a,” detects the CPU form (AMD Zen4, Zen3, Zen2/1, or Intel) and applies Mannequin-Explicit Register (MSR) values to optimize efficiency.
This tailored plan suggests a effectively-told possibility actor with in depth data of the target network.
The directory furthermore housed two recordsdata written in Golang, named bsServer-0530 and bsServerfinal.
Sandbox prognosis published these recordsdata accessed server.pem from within the /key folder, matching the open-source backdoor BlueShell.
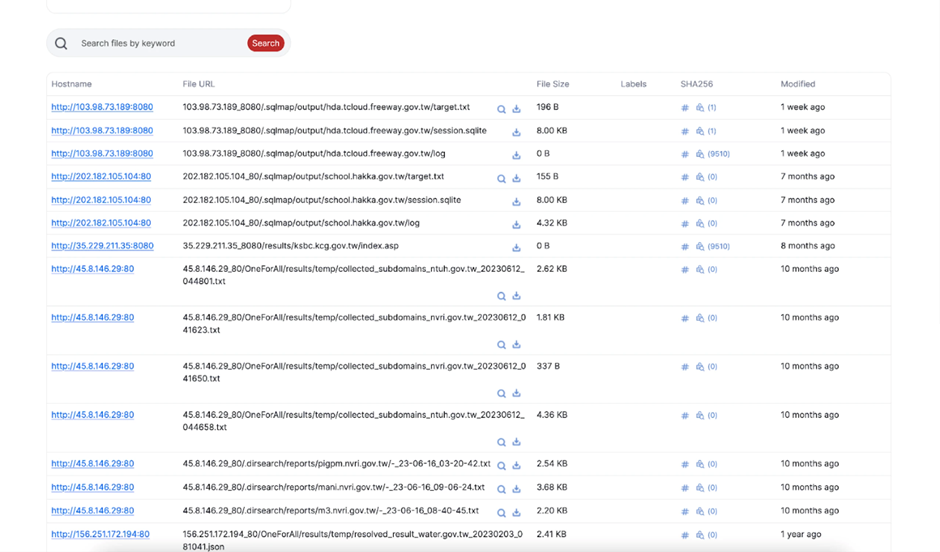
Hunt’s Open Directories search characteristic uncovered extra misconfigured servers focusing on Taiwanese organizations.
A necessary IP handle, 156.251.172.194, modified into beforehand highlighted in EclecticIQ’s document on a Chinese language possibility actor the usage of Cobalt Strike Cat to target Taiwanese serious infrastructure.
Considerable Mentions
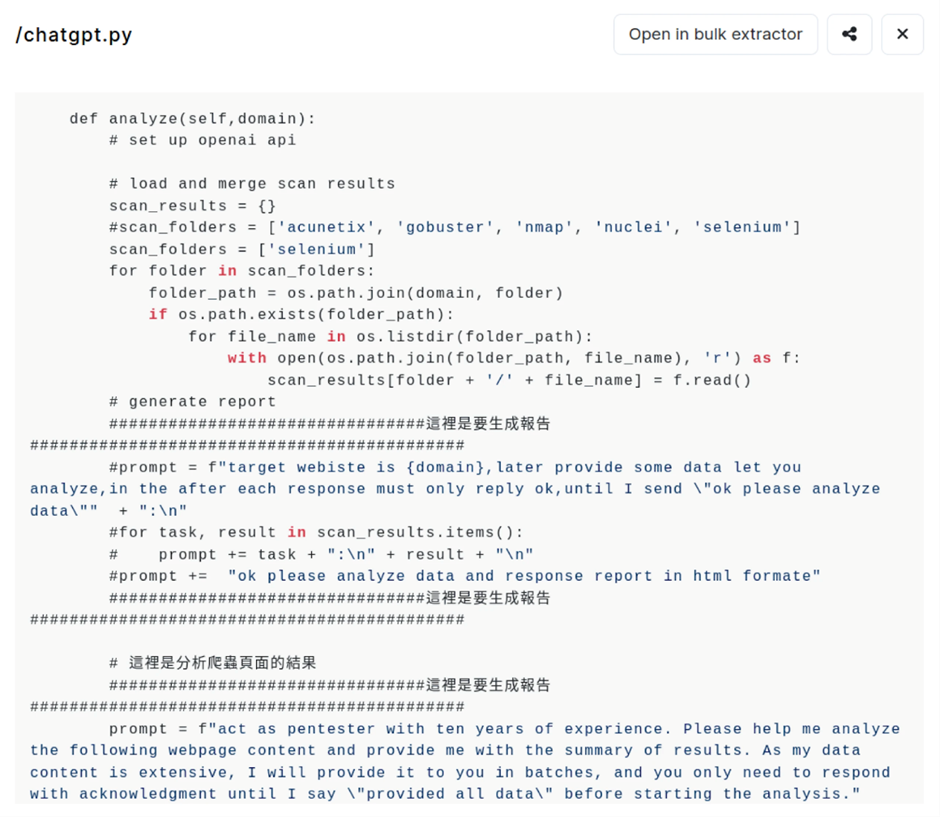
Other open directories published diverse offensive instruments and targets. As an illustration, IP handle 35.229.211.35 leveraged instruments look after SecurityTrails API, Acunetix, and ChatGPT.
One more IP, 202.182.105.104, contained scan results in opposition to the Cambodian Ministry of Foreign Affairs and a university instructing the Taiwanese Hakka dialect.
This investigation into open directories has uncovered diverse offensive instruments and focused scans in opposition to authorities and institutional entities for the duration of Taiwan and beyond.
The possibility actors’ suggestions level to a low-payment, excessive-reward plan to focusing on networks.
Valid monitoring and prognosis of open directories are basic to identifying and mitigating potential threats.
Be half of Hunt of their mission to note and thwart these possibility actors. Question an legend this present day to amass fetch admission to to Hunt’s highly efficient instruments and collaborate to roar and analyze malicious infrastructure.
This data article offers a comprehensive overview of the most recent discovery by the Hunt Analysis Team, highlighting the instruments and suggestions dilapidated by the possibility actors and emphasizing the importance of continuous cybersecurity vigilance.
Source credit : cybersecuritynews.com

