Threat Actors Using Mimikatz Hacking Tool to Deploy Trigona Ransomware

The Unit42 be taught crew at Palo Alto Networks has lately found Trigona ransomware that assaults Dwelling windows with new tactics and uses the Mimikatz exploitation instrument for Credential Loading, Dumping, Manipulation, and injection earlier than making an are attempting to encrypt the recordsdata.
Trigona ransomware was as soon as first found in October 2022, and it was as soon as very energetic in December 2022. In some unspecified time in the future of its closing discovery, it has affected nearly 15 organizations in Manufacturing, Finance, Constructing, advertising and marketing, and excessive abilities industries.
As of January and February of this year, four ransom notes of Trigona have been found, with two every month.
Unlike other ransomware notes, Trigona notes have been not easy-textual grunt recordsdata. As an different, it’s a long way an HTML application with JS embedded. It also includes CIDs (Computer IDs) and VIDs (Sufferer IDs).
Trigona Ransomware Overview
A safety researcher tweeted that the creators do preliminary rep admission to to a victim’s atmosphere, conducting an brisk reconnaissance, malware switch through a long way flung monitoring and administration (RMM), and person account creation and deployment.
As per reports, this ransomware has a list of recount traces and is supported by TDCP_rijndael ( a Delphi AES library) for encrypting recordsdata.
The extension of the affected recordsdata is with ._locked. On the opposite hand, the ransom ticket would perchance have a filename and extension as how_to_decrypt.hta .
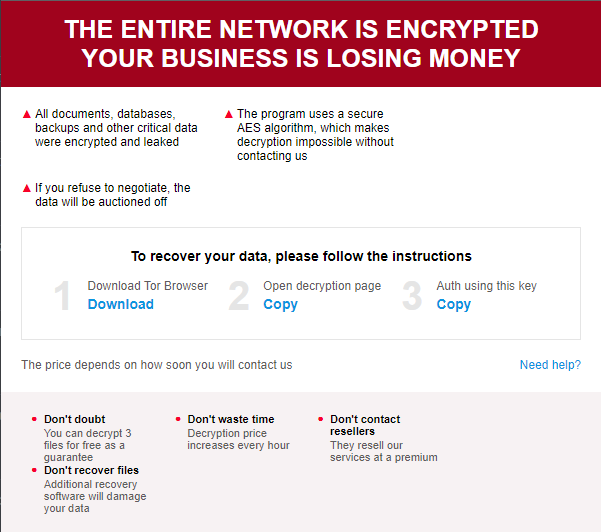
As acknowledged, the ransom ticket is an HTML file with JS embedded. Additional observation of the file showed some parameters containing the following recordsdata.
- CID and VID
- Email Address (Attacker)
- TOR URL for negotiation.
The describe also talked about that an online field was as soon as associated with the ransomware leaking the stolen recordsdata. There was as soon as also an likelihood to recount this recordsdata through an email tackle.
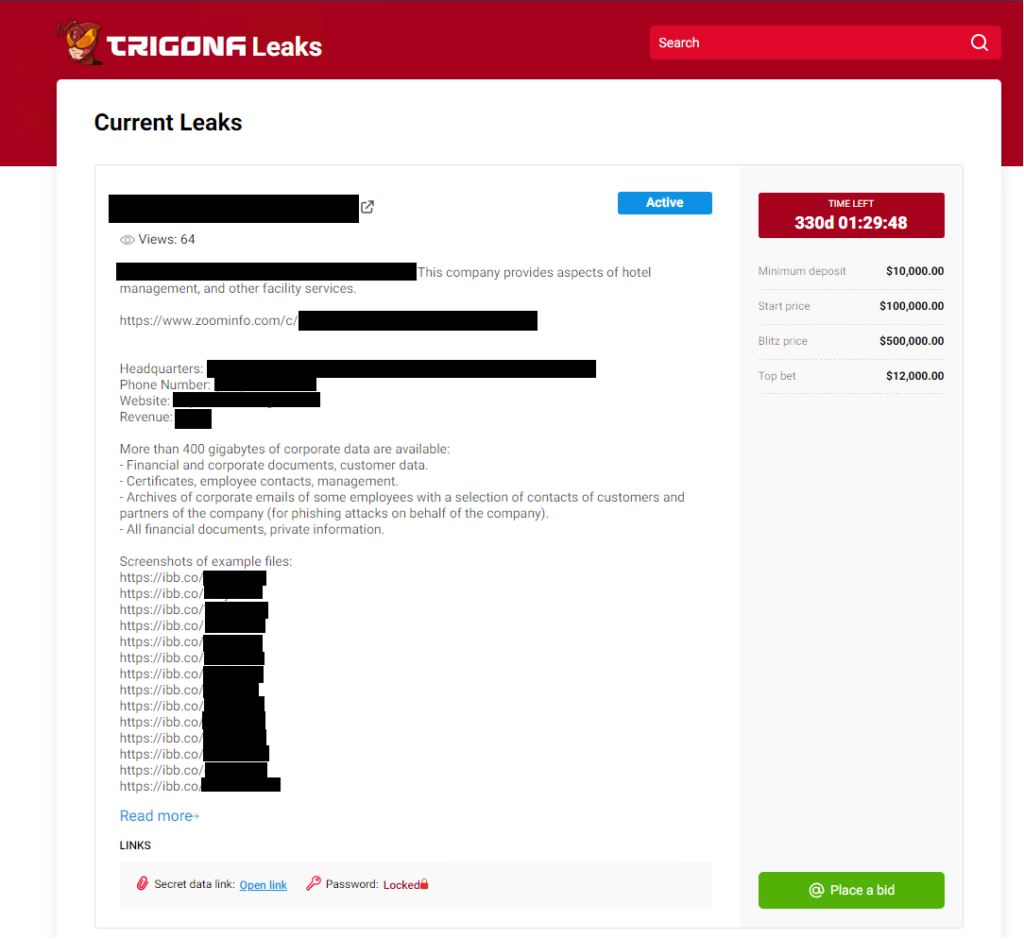
Binaries supported by Trigona
| Argument | Description |
| /fleshy | Performs all capabilities of the ransomware. Encrypts each local and community recordsdata. Creates two registry keys for persistence, one for the ransomware binary and one other for the ransom ticket. |
| /!autorun | Skips creation of registry keys for persistence |
| /test_cid “take a look at” | Overwrites default victim generated CID and substitute with “take a look at” cost |
| /test_vid “take a look at” | Overwrites default VID and substitute with “take a look at” cost |
| /p, /course “course” | Encrypts handiest recordsdata contained within specified course |
| /!local | Doesn’t encrypt local machine recordsdata, handiest encrypts recordsdata on local community |
| /!lan | Doesn’t encrypt local community recordsdata, handiest encrypts recordsdata on local machine |
| /autorun_only “course” | Creates registry key for persistence handiest. Enables for non-necessary “course” to be supplied to override default course, would not encrypt recordsdata |
DC2.exe – DC4.exe – DC6.exe
Trigona’s within the intervening time developing leak field, the operator and/or friends unhurried the ransomware seemingly will continue (and most certainly even ramp up) its malicious job.
A password-safe version of Mimikatz, a program for extracting sensitive recordsdata from a Dwelling windows running machine, corresponding to passwords and authentication credentials.
- Loading Credentials – Mimikatz retrieves credentials from pretty a pair of areas, at the side of Dwelling windows memory, the Native Safety Authority Subsystem Carrier (LSASS) direction of, and the Dwelling windows registry.
- Dumping of Credentials – The utility then extracts and dumps the credentials to the mask or a file, at the side of usernames and passwords, hashes, and Kerberos tickets.
- Manipulation of Credentials – Mimikatz enables customers to change passwords, label new person accounts, and add people to groups using the leaked credentials.
- Injection of Credentials – The altered credentials will also be injected into other processes, permitting the person to impersonate one other person and rep admission to restricted sources.
DC4.exe is a tiny, UPX-packed password-safe binary that generates and executes an embedded batch file. Like DC2.exe, the password to enable the binary to bustle is boris.
DC6.exe is an installer for the publicly available instrument Developed Port Scanner, wrapped up in an Inno Setup installer package.
“Trigona’s within the intervening time developing leak field, the operator and/or friends unhurried the ransomware seemingly will continue (and most certainly even ramp up) its malicious job.” Palo Alto Concluded.
This ransomware is similar to CryLock ransomware which also involves the Ways, Programs, and Procedures (TTPs); Unit 42 Palo Alto revealed a Entire describe.
Constructing Your Malware Defense Technique – Download Free E-E book
Additionally Read:
- First-Ever Ransomware Found to be Attacking macOS
- Hackers Exploited Dwelling windows Zero-day For Ransomware Assaults
Source credit : cybersecuritynews.com


