TLS-based SparkCockpit & SparkTar Malware Ivanti's Pulse Secure VPN

A most stylish investigation has uncovered a flaw in net-connected doorbell cameras, particularly affecting Ivanti’s Pulse Stable appliances.
The NVISO Incident Response crew realized the discovery, which identified two covert TLS-basically based backdoors, SparkCockpit and SparkTar, allowing attackers to hijack these devices and catch unauthorized catch entry to to interior networks.

The investigation used to be caused by a critical-sector group that noticed a compromise of their Ivanti equipment, resulting within the discovery of those subtle backdoors.
Sophisticated Assault Programs
Both SparkCockpit and SparkTar employ selective interception of TLS conversation in direction of reputable Ivanti server applications, which helps them defend a ways flung from detection.
SparkTar is in particular superior and in a position to surviving manufacturing facility resets and equipment upgrades.
It additionally allows for file uploads, explain execution, and establishing SOCKS proxies to relay attacker traffic straight into the group’s community.
The NVISO crew realized that these backdoors may per chance well evade detection by most community-basically based safety alternatives, offering attackers persistence and distant catch entry to capabilities, including traffic tunneling via SOCKS proxies.
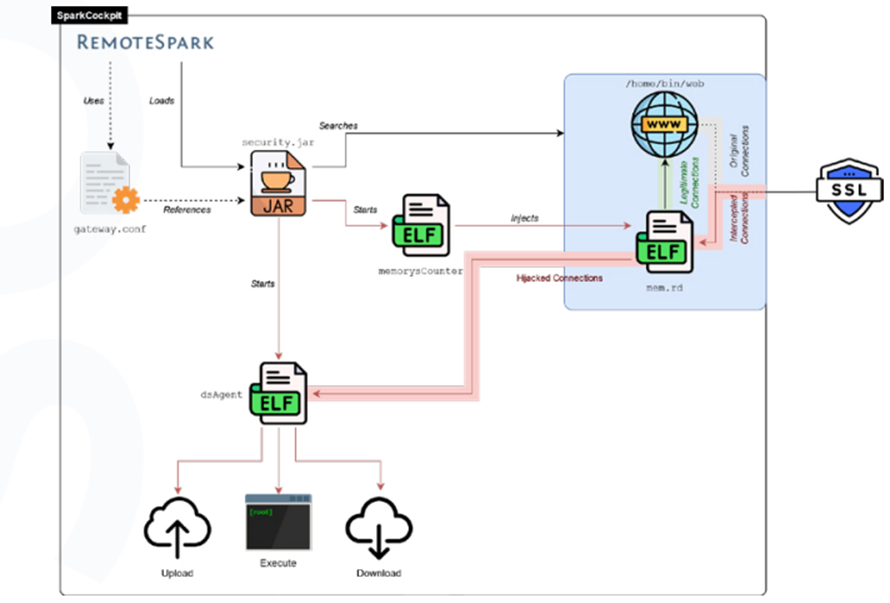
SparkCockpit: A Nearer Peek
SparkCockpit used to be deployed via an evolution of the Pulse Stable BUSHWALK web shell and gives total upload/download capabilities alongside explain execution.
It achieves boot persistence by patching the configuration of the RemoteSpark’s server ingredient, SparkGateway, to load a malicious safety.jar plugin.
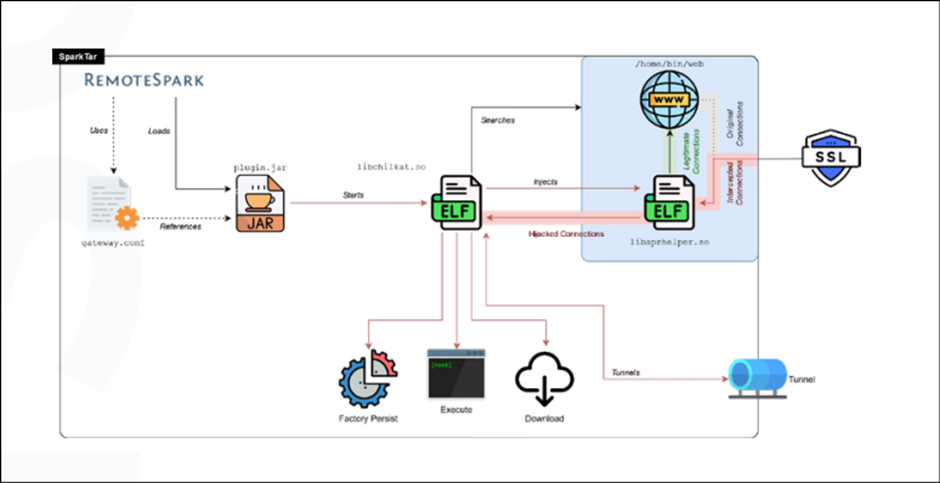
SparkTar: A Extra Complicated Threat
SparkTar, on utterly different hand, is extra advanced and gives a extra flexible toolset for attackers. It contains input/output streaming for instructions and deeper persistence mechanisms.
The backdoor controller libchilkat, which is unrelated to reputable Chilkat business instruments, is to blame for launching the backdoor and guaranteeing its persistence.
NVISO’s Response and Crew Toughen
NVISO has created detection guidelines to help organizations resolve if these backdoors obtain impacted them.
The firm, a European cybersecurity chief, is committed to sharing knowledge and supporting organizations in preserving against superior and evolving cyber threats.
NVISO’s findings obtain been corroborated by research from Mandiant and in part noticed by Fortinet.
A most stylish tweet from NVISO Labs launched an Incident response about covert TLS n-day backdoors: SparkCockpit & SparkTar
Implications for Security
The presence of those backdoors in Ivanti’s Pulse Stable appliances highlights the need for elevated vigilance and improved safety measures for net-connected devices.
Organizations the exercise of Ivanti devices are advised to study NVISO’s portray and apply the supplied detection guidelines to safeguard against doable compromises.
In conclusion, the discovery of SparkCockpit and SparkTar backdoors serves as a critical reminder of the persistent and advanced nature of cyber threats. Organizations should continuously toughen their safety posture and resilience to defend against such superior tactics.
You may per chance well presumably block malware, including Trojans, ransomware, spyware and adware, rootkits, worms, and nil-day exploits, with Perimeter81 malware safety. All are extremely wicked, can wreak havoc, and hurt your community.
Set updated on Cybersecurity recordsdata, Whitepapers, and Infographics. Practice us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


