Top 12 Best Open Source Intelligence Tools (OSINT Tools) for Penetration Testing 2024

Introduction :
Everybody knows completely that getting or gathering any info by the utilize of fairly masses of instruments becomes with out a doubt straightforward.
Listed right here, we comprise now talked about fairly masses of OSINT instruments, as if we search over the salvage, then there could be many change pages to come out.

But potentially the most problematic thing is to gain fairly masses of info from more than one pages for an acceptable purpose throughout the mission.
Hence, we comprise now accrued each and each and each and each detail about these instruments and place all of them together on this publish, and in consequence, we can insist you the ten greatest OSINT instruments.
Basically, OSINT instruments are utilized by pen testers to search out likely weaknesses and data in a firm’s protection system that’s working.
Then again, instruments play a indispensable feature, nonetheless with out radiant the usage of instruments, it could per chance be nugatory for the customers to make utilize of it.
Hence, before shifting toward the instruments, let’s manufacture some knowledge about OSINT and why will we desire OSINT instruments.
Incessantly Requested questions?
As we comprise now talked about above that OSINT stands for start-source intelligence, and it refers to a assortment of info or info from public sources like firms, organizations, or about participants.
Basically, OSINT ways were constituted of brazenly on hand info for the public that’s accrued, utilized, and distributed at a lawful time to a lawful viewers for steering a explicit intelligence search info from.
The salvage is a broad differ of sources of info which has colossal advantages and downsides as well to.
Hence if we talk about advantages, then we can explain that the salvage is free to salvage entry to, and all people can salvage pleasure from or put it to use till and except it has been restricted by the group or by the law.
On the fairly masses of hand, if we talk in regards to the disadvantages, then let me elaborate that someone with a flawed design can with out concerns misuse the data which is on hand on the salvage.
Web info can vary once rapidly, like audio, video, textual voice material, net situation info, article or info, and lots of others.
After radiant what’s OSINT instruments, now the place a query to arises why will we desire OSINT instruments? Train there’s a command the place you wish search out moral info linked to a explicit topic on the salvage.
And for this, you wish execute it in two techniques, first, you wish analyze and gain the total info in regards to the sphere; its form of laboring and time taking too.
Now, on the fairly masses of hand, you should merely utilize the start-source intelligence instruments, as the instruments are in an instant linked to the fairly masses of websites, and overview the sphere if it’s contemporary or no longer factual in just a few seconds.
Hence, now we hope that for you it’s decided that it saves masses of time, and the customers salvage moral info with out remembering the data.
And no longer greatest that even we could per chance utilize fairly masses of instruments to get dangle of all explicit info in regards to the sphere that we’re in search of.
Desk of Contents
Incessantly Requested questions?
Top 10 Ideal OSINT Instruments 2024
1.Social Hyperlinks
2.Google Dorks
3.NexVision
4.TheHarvester
5.Shodan
6.Hudson Rock
7.Maltego
8.Metagoofil
9.Recon-Ng
10.Examine Usernames
11.TinEye
12.SpiderFoot
13.Creepy
Top 10 Ideal OSINT Instruments 2024 Parts
Conclusion
Also Read
Top 10 Ideal OSINT Instruments 2024
- Social Hyperlinks
- Google Dorks
- NexVision
- TheHarvester
- Shodan
- Hudson Rock
- Maltego
- Metagoofil
- Recon-Ng
- Examine Usernames
- TinEye
- SpiderFoot
- Creepy
Top 10 Ideal OSINT Instruments 2024 Parts
| Top 10 Ideal OSINT Instruments 2024 | Parts |
|---|---|
| 1.Social Hyperlinks | Connects platforms with out any concerns. Makes sharing field materials more uncomplicated. Makes it more uncomplicated to secret agent and have interaction with. Takes you to definite participants. Boosts the reach of networking. |
| 2.Google Dorks | Extra evolved search instruments. Web non-public info. Procure outcomes more explicit. Stare for vulnerable spots. Web definite kinds of recordsdata. |
| 3.NexVision | Programs for processing photography. Object identification and object detection. Finding faces and analyzing them. Segmenting an image. Laser character recognition (OCR). |
| 4.TheHarvester | Getting emails from search instruments. Domain perceive from a assortment of fairly masses of angles. Inserting together subdomains which could be linked to a purpose. Using public sources to gain info. Making a list of virtual sites and IPs. |
| 5.Shodan | Stare for definite companies or objects. Stare into techniques which could be vulnerable or start. Explore tool info and banners in precise time. Web the companies and ports which could be start. Stare at puny print from IoT gadgets. |
| 6.Hudson Rock | maintaining an peep out for and finding info breaches. Monitoring and data on the unlit net. Prognosis of threat info. Overview and protect watch over of vulnerabilities. Responding to and reducing incidents. |
| 7.Maltego | Combining info from fairly masses of sources. A portray of how partnerships work. Link evaluation is a technique to search out relationships. Getting puny print about organizations and their connections. Using more than one info source together. |
| 8.Metagoofil | Getting metadata out of papers. A community of papers from definite domains. Procure support usernames, tracks, and pretty masses of issues. Reinforce for many kinds of documents. Helps with mapping networks. |
| 9.Recon-Ng | Reconnaissance framework with modular parts. Automatic gathering of info. Moderately a number of API increase for info sources. GUIs that stride on the salvage and on terminals. Works with a assortment of info-gathering instruments. |
| 10.Examine Usernames | Usernames that work on fairly masses of platforms. Making definite that usernames appear on websites or social media sites. Stare for accounts or names which could be linked. Prognosis of how constant usernames are all over techniques. Record of usernames that can additionally be used for ticket original accounts. |
| 11.TinEye | Ability to stay conscious for photography backwards. Finds the place photos on the salvage approach from. Finds versions which were modified or as much as this level. Finds photos which could be identical or linked. Uses uploaded or URL-based fully fully photos for searches. |
| 12.SpiderFoot | Automatic gathering of OSINT info. Looks at many sources of info. Discovers how issues are linked. Gets info about names, IP addresses, and pretty masses of issues. Looks for likely safety holes. |
| 13.Creepy | Gets status info from social media sites. Gets metadata from photos which could be shared with the public. Presentations info in accordance with your status. Maps the positions of photography on a display veil veil. Using photos, it retains note of the place customers crawl. |
1. Social Hyperlinks

Social Hyperlinks is an AI-powered instrument trend company that builds solutions to mine public info sources at the side of social media, messengers, blockchains, and the Dusky Web for insights.
The firm’s fundamental product, SL Decent, helps investigators and data safety experts salvage more done in much less time.
With SL Decent, you salvage salvage entry to to a voice of search techniques which were particularly developed to quilt over 500 start sources.
Customers can practice masses of advanced filters to the data being accrued the utilize of the product’s evolved search queries, many of which are in accordance with machine finding out.
Social Hyperlinks OSINT solutions, on the fairly masses of hand, execute more than merely get dangle of info; as well they present subtle evaluation capabilities that could be used to refine info as investigations proceed, yielding more real outcomes and painting a clearer portray of the command.
Product Parts
- A first rate voice of over 1,000 search techniques for over 500 start info sources, at the side of the Dusky Web, social networks, messaging applications, and all fundamental info source sites.
- Superior robotic capabilities that at present and successfully dangle masses of info the utilize of machine finding out
- Details could per chance additionally be personalized and expanded with personalized overview instruments.
- Without anxiousness built-in into any IT system
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Connectivity and Communique | Privacy Concerns |
| Details Sharing | On-line Harassment and Bullying |
| Networking and Decent Opportunities | Details Overload and False News |
| Creativity and Expression |
2. Google Dorks
.webp)
Google is the most favorite search engine on this planet, which shouldn’t approach as a shock to someone. We all utilize Google to search out the data we need, even though the salvage giant isn’t an start-source instrument.
We depend on serps since they no longer greatest memoir indispensable info nonetheless also supply us with indispensable info.
Additionally, Google Dorks (also called Google Hacking) affords a user-pleasant and adaptable approach of making an strive to salvage info with the utility of definite operators.
All the pieces from social media posts and commercials to websites and photography are share of the quest engine’s output. It could per chance most likely per chance be straightforward for the quest engine suppliers to toughen and make more accessible the data on info safety.
OSINT Instruments Parts
As we all know that Google uses operators to search out info, and listed below are some operators that we comprise now talked about below:-
- Extra most incessantly than no longer, this feature is used to stay conscious for the title.
- While you utilize this operator, you should stay conscious for a definite file name.
- Inurl: It factual helps us salvage definite phrases which could be within the URL.
- While you utilize this feature, “filetype,” you should make definite that this could occasionally insist you the formula to scrutinize the file.
- Intext: This characteristic helps us salvage a definite fragment of textual voice material on a definite page.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Superior Search Capabilities | Privacy and Security Dangers |
| Details Gathering | Ethical Concerns |
| Websites Vulnerability Overview | Lawful Implications |
| Aggressive Intelligence | Wrong or Out of date Results |
3. NexVision
.webp)
One OSINT utility that uses AI to automate info accumulating and processing is NexVision.
Its reason is to pressure resolution-making.
Amongst the starting up source intelligence (OSINT) instruments utilized by researchers, governments, and companies, it is perhaps the most thorough.
In difference to fairly masses of start source intelligence (OSINT) instruments, NexVision affords the greatest OSINT info pool (surface and unlit net, social media info lake) and employs synthetic intelligence (AI) to do away with fraudulent positives, ensuring that customers gain potentially the most lawful intelligence.
Aim
Enable teams all over the enterprise, at the side of those liable for safety operations, compliance, incident response, fraud prevention, risk evaluation, and threat monitoring, to make sooner and more lawful judgments by providing them with lawful, timely, and actionable intelligence.
OSINT Instruments Parts
- AI/ML-powered engine that continuously gathers, analyzes, and sorts noteworthy amounts of info from public sources and the deep net
- Give participants precise-time salvage entry to to the total net, at the side of the “unlit net” (the place crimes happen) and the “decided net,” all with out having to make utilize of a browser like Tor to conceal their identification.
- Including lots more info whereas removing fraudulent positives
- Reinforce for more than one languages
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Superior image processing. | Moral findings require excessive-quality info. |
| That you just should imagine utilize in healthcare, automobile, and surveillance. | Compatibility concerns with particular hardware and applications. |
| Modern object detection, portray evaluation, and machine vision algorithms. | |
| Customized substitute solutions. |
4. TheHarvester
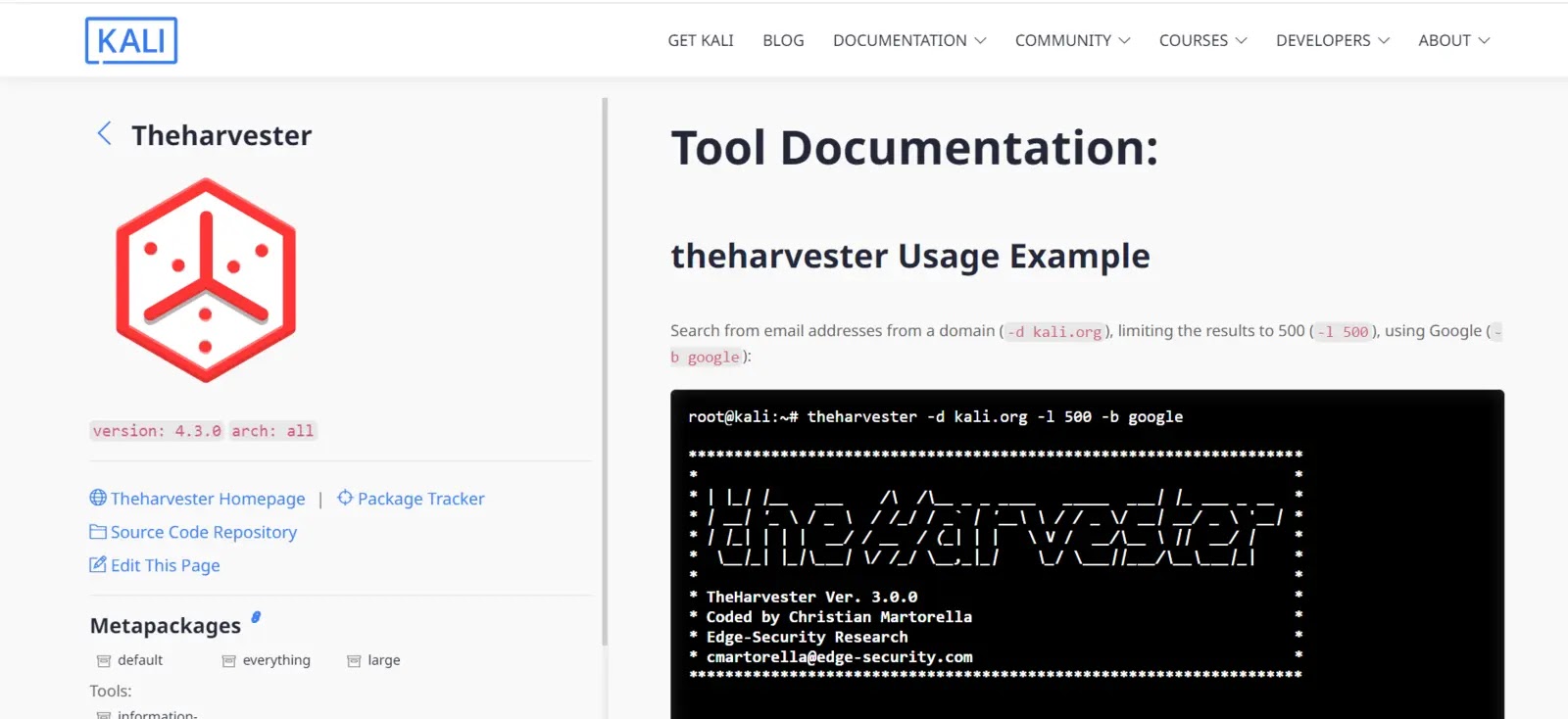
Amongst the masses of public serps and PGP key servers, the Harvester stands out as a amazing instrument for locating emails, user names, hostnames, and enviornment-linked info.
This instrument, which is share of the larger Kali Linux Instruments, is mountainous for gathering info utilized within the first stages of a penetration test.
Designed with the evolved penetration tester in mind, this instrument is easy to make utilize of, manages its sources successfully, and produces first rate outcomes.
Google for email addresses and subdomains, PGP server for user accounts and hostnames, and a plethora of fairly masses of sources are all accessible thru it.
Parts
- Search engines, PGP key servers, and noteworthy social networking sites can aid the Harvester salvage purpose enviornment email addresses.
- The instrument finds purpose contend with-linked subdomains.
- Google, Bing, and Baidu can aid the Harvester name linked info.
- Shodan searches for cyber net-linked gadgets.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Details Gathering | Reliance on Publicly Accessible Details |
| Customizable Sources | Incomplete or Out of date Details |
| E mail Take care of Discovery | Lawful and Ethical Concerns |
| Subdomain Enumeratio | Lack of Superior Prognosis |
5. Shodan

In the event you are going to favor to grab what sources are accessible, hackers most incessantly utilize Shodan, a sturdy search engine.
In the event you search info from safety experts, this could occasionally give you solutions that make more sense.
Accessible from masses of Web of Things (IoT) gadgets, at the side of computer techniques, laptops, online page online page visitors indicators, webcams, and more, it largely stores info linked to sources which could be being linked to the community.
With this program, a safety analyst could per chance with out concerns name the purpose and overview it for a broad differ of vulnerabilities, companies, passwords, ports, and more.
Additionally, it affords versatility in community searches.
Parts
- Shodan scrapes and stores cyber net info to aid customers salvage gadgets and companies.
- It finds start ports and their companies by port hunting.
- This vulnerability detection scans cyber net-linked gadgets for safety flaws.
- It gathers advertising and marketing and data from companies and gadgets.
- Banners incessantly reward instrument model numbers and pretty masses of identifiers.
- This helps name machines running particular instrument.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Instrument Discovery | Privacy Concerns |
| Vulnerability Overview | Lawful and Ethical Concerns |
| Search Filters and Queries | Incomplete or Out of date Details |
| Exploit Detection | Restricted Visibility |
6. Hudson Rock
Hudson Rock’s courageous cybercrime threat intelligence movement, crafted the utilize of knowledge honed on the esteemed 8200 cyber unit of the IDF, affords priceless info for assessing supply chain risk, maintaining terminate-customers, and securing infrastructure.
Notifications are despatched to SOC teams referring to staff, customers, partners, and third parties whose techniques were infiltrated by worldwide malware spreading campaigns thru Cavalier, a platform and API developed by Hudson Rock for threat intelligence experts.
Cavalier empowers enterprises to battle ransomware and pretty masses of cyberattacks with extremely delicate and actionable intelligence gathered from threat actors in odd hacking circles.
Their database has info on millions of compromised gadgets.
‘Bayonet’ is any other implausible sales prospecting instrument that Hudson Rock affords to cybersecurity sales teams.
At HudsonRock, you should salvage a free trial of Cavalier & Bayonet and a model of their vital cybercrime API.
Parts
- Hudson Rock could comprise companies that video display the unlit net for stolen passwords, leaking info, and cyber threat talks.
- Hudson Rock could per chance video display and detect customer info breaches.
- Risk intelligence companies from Hudson Rock could per chance present companies with precise-time info on rising threats, hacking teams, safety flaws, and pretty masses of safety concerns.
- Hudson Rock could per chance analyze a substitute’s community, techniques, and apps for vulnerabilities.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Level of interest on user privacy and data safety the utilize of encryption and pretty masses of safeguards. | It could per chance most likely per chance lack evolved capabilities and integrations in contrast to favorite email suppliers. |
| Does no longer note user behavior or reward adverts, making email more non-public. | Being original, it could comprise fewer customers than established email suppliers. |
| Permits customers to administer and delete non-public info. | |
| E mail privacy is enhanced with terminate-to-terminate encryption. |
7. Maltego
.webp)
Kali Linux includes it, which Paterva developed.
With the aid of some built-in transforms, this start-source intelligence instrument basically conducts indispensable investigations towards diverse targets.
It be a ought to to be part of the Paterva situation before you should utilize Maltego. If you’re registered, you should execute any machine you desire or factual stride it to gain the purpose.
Java is the language of preference for many of Maltego’s applications, and Kali Linux has this language pre-packaged.
Besides to generating graphical outcomes of the purpose, Maltego has fairly masses of built-in processes that make it straightforward to gain info from fairly masses of sources in accordance with the end result.
Parts
- Maltego customers could per chance fabricate visible graphs of people, firms, websites, IP addresses, and more.
- Maltego can salvage entry to public databases, social media, DNS info, on-line companies, and more.
- Maltego lets you place connections and similarities by routinely linking info.
- Maltego permits participants collaborate by sharing graphs and data.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Complete Details Gathering | Helpful resource Necessities |
| Graphical Link Prognosis | Details Source Limitations |
| Intensive Change into and Integration Choices | Licensing and Pricing |
| Customization and Flexibility |
8. Metagoofil
.webp)
For potentially the most share, Metagoofil is employed to extract metadata from publicly on hand documents belonging to the centered firm or group.
Document hunting, metadata extraction, end result reporting, and native downloading are factual just among the masses of capabilities equipped by this program.
Upon completion, a portray is generated that capabilities login credentials, instrument versions, and the names of servers or particular person machines.
This info could be priceless for penetration testers throughout the data assortment share.
Parts
- Metagoofil can be taught PDFs, Microsoft Predicament of industrial recordsdata (Word, Excel, and PowerPoint), and pretty masses of codecs.
- It helps name articles’ origins.
- It learns about a person or community thru document metadata.
- It ought to salvage entry to on-line recordsdata on its PC.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Metadata Extraction | Restricted Document Forms |
| Bulk Processing | Dependency on Metadata |
| Customizable Output | Lack of Superior Prognosis |
| Document Source Prognosis | Lawful and Ethical Concerns |
9. Recon-Ng

Now not greatest is Recon-Ng one amongst the greatest OSINT Instruments on the list, however additionally it is pre-installed in Kali Linux, making it very splendid for purpose surveillance.
Now not greatest does Recon-ng’s approach connect with Metasploit, however it also affords more than one built-in modules, which is one amongst its most indispensable capabilities.
Customers conversant in Metasploit will imprint the corpulent capability of its modular instruments.
Workspaces are most incessantly created with the reveal reason of performing operations inner them; adding a enviornment to one is a prerequisite to the utilize of a modular instrument.
In the event you are going to favor to scrutinize more domains linked to your first purpose enviornment, you should utilize some implausible modules like bing-enviornment-net and google-situation-net.
Search engines will proceed to index these domains in consequence.
Parts
- Recon-ng can salvage entry to serps, social media, DNS info, net companies, APIs, and more.
- It affords a number of willing-made modules for diverse info assortment projects because it’s modular.
- It supports engaging reconnaissance, which probes purpose techniques for info.
- Customers can utilize reward instruments and companies in Recon-ng by connecting exterior instruments and data sources.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Modular Structure | Lawful and Ethical Concerns |
| Intensive Fluctuate of Modules | Details Source Limitations |
| API Reinforce | Technical Expertise Required |
| Highly effective Request Language |
10. Examine Usernames
How leisurely and time-drinking it’s to manually stay conscious for a username’s presence within the absence of an start-source intelligence instrument is something we covered earlier.
Accordingly, Examine Usernames is a top instrument for rapid retrieving any info relating to usernames.
It scans more than 150 websites for a single username at a time, and it also has a mountainous feature that lets you detect in case your purpose is on a explicit page, allowing you to counter or attack them correct away.
Parts
- See for and overview to secret agent if a username is on hand on fairly masses of techniques.
- Notification or alert when the username you desire becomes on hand.
- Thoughts on fairly masses of likely usernames.
- Making definite that your ticket or non-public identification is constant all over all channels.
- Some instruments could comprise additional safety capabilities, much like checking the capability of your passwords or maintaining an peep out for breaches that comprise usernames.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Tests username availability on social media and net platforms rapid. | Now not sufficient info in precise time. |
| Reduces platform checks by consolidating searches. | Platform privacy alternatives place limits on what could per chance additionally be done. |
| Presentations alternate usernames if the specified one is taken. | |
| Helps companies and participants ticket consistently all over platforms. |
11. TinEye
In the event you are going to favor to grab the place an image came from or what it has been used for, all you wish execute is upload the correct photo to TinEye, the first reverse image search engine.
To attain its needs, it doesn’t depend on key phrase matching nonetheless fairly on a assortment of change techniques, much like image matching, signature matching, watermark identification, and a assortment of databases.
As antagonistic to the utilize of key phrases or metadata, TinEye uses portray identification technology, neural networks, machine finding out, and sample recognition.
To sum up, it’s undeniably one amongst the greatest instruments on hand on-line for reverse image search for individuals who’re making an strive to salvage something identical.
Parts
- TinEye’s backward portray search is its finest characteristic.
- It searches its index for linked photography. Add or present an image URL.
- It compares photography in accordance with colours, shapes, textures, and patterns the utilize of evolved image recognition algorithms.
- This instrument works in fairly masses of languages, so customers could per chance salvage photos linked to definite languages or areas.
- Chrome, Firefox, Safari, and more browsers comprise TinEye plugins.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Image Discovery | Restricted Image Protection |
| Intensive Image Index | Reliance on Metadata |
| Particular person-Pleasant Interface | Incapacity to Search Non-public or Restricted Exclaim |
| Extra Search Parameters | Language and Cultural Limitations |
12. SpiderFoot
.webp)
This start-source program is share of the OSINT Instruments assortment on GitHub and is successfully matched with each and each Windows and Linux, two of the most favorite working techniques.
It is successfully matched with any virtual platform and used to be developed in Python.
It has the capability to routinely salvage entry to info on emails, IP addresses, names, domains, and lots of others. by asking queries to more than a hundred OSINT professionals.
A sturdy bid-line interface is blended with a in point of fact easy-to-utilize and interactive graphical user interface.
A net-based server, netblocks, emails, and a plethora of fairly masses of purpose-linked info are amongst the masses of issues it receives and stores.
Spiderfoot factual gathers info by finding out how issues are linked, so you should tailor it to your needs and necessities.
Details breaches, vulnerabilities, and pretty masses of pertinent info on capability hacking threats are also clearly disclosed.
Thanks to this original determining, we could per chance make higher utilize of the penetration test and toughen our threat intelligence to alert us before an attack or theft occurs.
Parts
- SpiderFoot’s modular fabricate lets customers customise and add capabilities.
- SpiderFoot can salvage entry to serps, social media, DNS info, WHOIS info, IP monitoring databases, threat intelligence feeds, public databases, and more.
- SpiderFoot automates info retrieval by hunting APIs and data sources.
- SpiderFoot could per chance watch relationships between social media accounts, domains, IP addresses, and email addresses.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Complete Details Gathering | Lawful and Ethical Concerns |
| Automation and Effectivity | Unsuitable Positives and Unsuitable Negatives |
| Customization and Flexibility | Technical Expertise Required |
13. Creepy

It is an start-source geolocation intelligence program that collects geolocation info from fairly masses of social media sites and pretty masses of portray cyber net hosting companies that comprise already been released.
Two fundamental tabs, “Targets” and “Arrangement survey,” are most incessantly contemporary in Creepy.
In essence, it uses the original date and real status as search filters to reward the descriptions on the procedure.
Plus, you should salvage these experiences in CSV or KML format for individuals who pick out.
Additionally, it’s Python-based fully fully and features a binary kit for Windows, Linux (at the side of Ubuntu, Debian, and Again off), and pretty masses of working techniques.
Parts
- The predominant thing that creepy does is get dangle of geolocation info from social media sites.
- Creepy has a visual instrument that shows the geolocation info it has accrued on a procedure.
- Creepy lets customers protect an peep on definite customers all over more than one social media sites and detect the place they are the least bit cases.
- Creepy has a instrument called “timeline” that lets customers watch on the geolocation info it has accrued over time.
| What’s Dazzling ? | What Would possibly perhaps perhaps per chance perhaps additionally Be Higher ? |
|---|---|
| Geolocation Details | Privacy Concerns |
| Social Media Mapping | Accuracy and Reliability |
| Customizable Search Parameters | Restricted Protection |
| Extensibility |
Conclusion
Listed right here, we tried to quilt the total info on OSINT instruments, at the side of OSINT ways, and what they need, and we comprise now also talked about the terminate 10 greatest OSINT instruments of 2023 as successfully.
Even supposing the list can crawl on, in truth that it is counting on the option of the correct instrument and moral ways.
Hence the above instruments are free to make utilize of so as that customers can with out concerns utilize them and can overview which is more lawful for them.
So, what execute you watched about this? Merely fragment your entire views and thoughts within the relate share below.
And for individuals who cherished this publish, then execute no longer neglect to fragment this publish with your mates and for your social profiles too.
Also Read
10 Ideal Superior Endpoint Security Instruments
10 Ideal Delivery Source Firewalls to Supply protection to Your Endeavor Network
Source credit : cybersecuritynews.com


