TransparentTribe Hackers Weaponize Websites & Documents to Attack Indian Orgs
.webp)
The hacker community identified as TransparentTribe, veritably identified as APT-36, has intensified its cyber espionage actions.
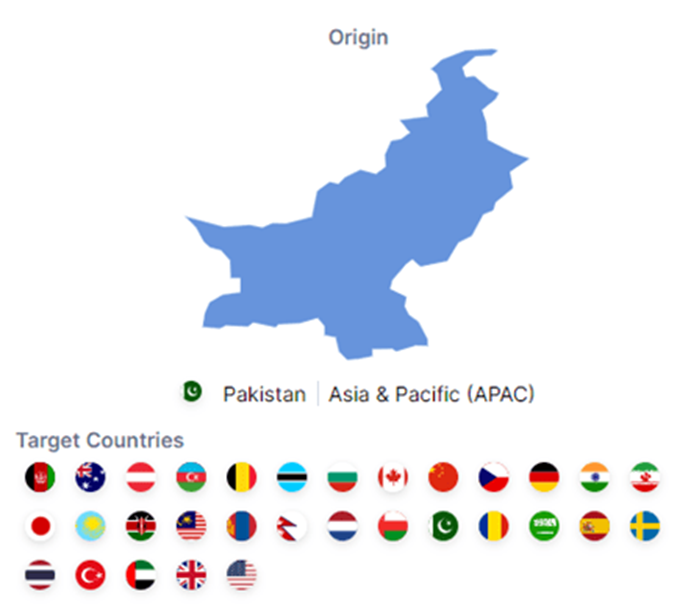
This community, originating from Pakistan, has been actively focusing on Indian authorities organizations, militia personnel, and defense contractors with refined cyberattacks aimed at compromising security and gathering sensitive data.

TransparentTribe mostly goes after India and Afghanistan, nonetheless it absolutely has moreover been seen going after Australia, Austria, Azerbaijan, Belgium, Botswana, Bulgaria, Canada, China, Czech, Germany, Iran, Japan, Kazakhstan, Kenya, Malaysia, Nepal, the Netherlands, Oman, Pakistan, Romania, Saudi Arabia, Spain, Sweden, Thailand, Turkey, the UAE, the UK, and the US.
Overview of TransparentTribe’s Operations
TransparentTribe is notorious for its well-orchestrated attacks on somewhat just a few platforms, including Windows, Android, and Linux.
The community employs somewhat just a few ways, just like growing fraudulent websites and paperwork that mimic genuine authorities entities. This deceives focused customers into disclosing their credentials or downloading malware.

One of many key solutions TransparentTribe makes exhaust of entails exploiting vulnerabilities inner methods to deploy malware and behavior surveillance.
The community has been documented the exhaust of several essential vulnerabilities outlined below.
CVE-2012-0158
This vulnerability lies in the MSCOMCTL.OCX ingredient of Microsoft methods, allowing some distance off code execution.
TransparentTribe has crafted malicious data that exploit this vulnerability to originate arbitrary code on the sufferer’s machine, ensuing in unauthorized opt up admission to and indulge in an eye on.
CVE-2010-3333
One other most distinguished vulnerability focused by TransparentTribe is CVE-2010-3333, a stack-based buffer overflow topic in Microsoft Place of enterprise.
This flaw may maybe well well moreover be exploited thru particularly crafted paperwork, enabling attackers to originate code under the guise of the logged-in particular person.
Malicious Instruments and Ways
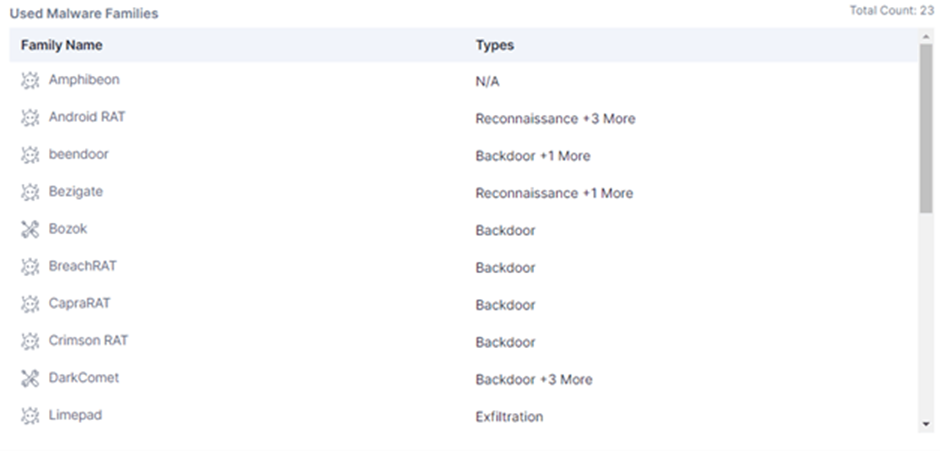
TransparentTribe makes use of a various arsenal of instruments to infiltrate and persist inner the focused methods.
These consist of somewhat just a few A ways-off Bag entry to Trojans (RATs), just like Crimson RAT, DarkComet, and ObliqueRAT, which allow some distance off indulge in an eye on of compromised methods.
The community’s strategy veritably entails preliminary infection thru phishing emails, malicious classified ads (malvertising), and social engineering ways.
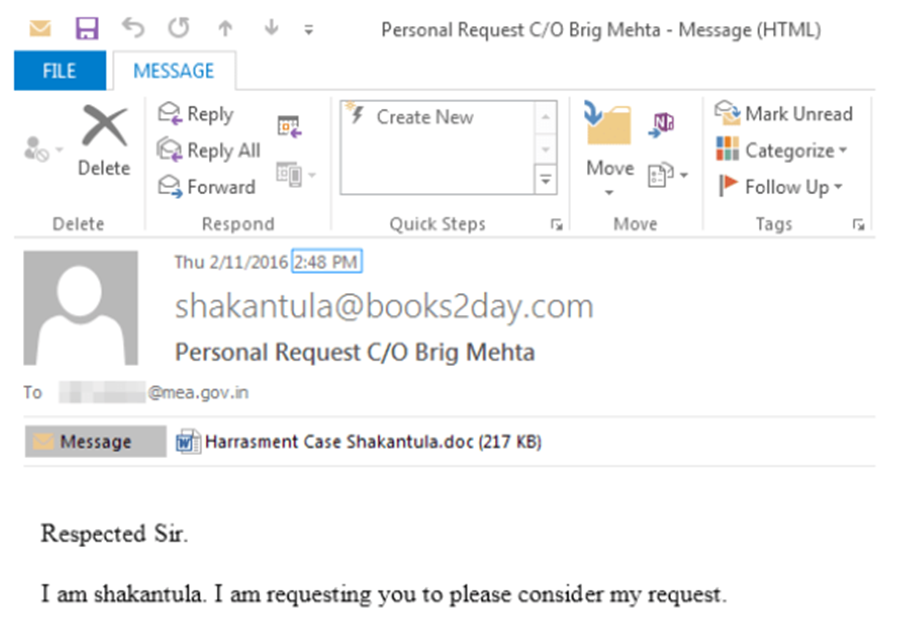
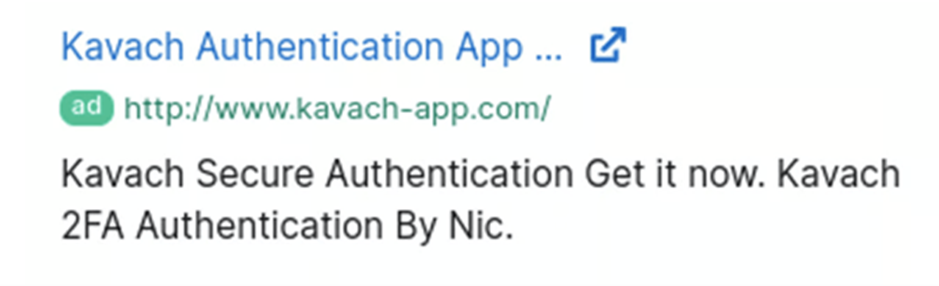
The community has been noticed the exhaust of domains with typo-squatted names to mimic legit websites, that are then ragged to host malicious data.
Furthermore, TransparentTribe leverages social engineering, seriously thru platforms esteem YouTube, where they originate fraudulent profiles to trap folk into downloading malicious purposes.
The actions of TransparentTribe spotlight a serious threat to national security for India and varied focused nations.
The community’s genuine evolution of how and complex instruments necessitates a sturdy cybersecurity posture and consciousness amongst skill targets.
Organizations are urged to put into effect stringent safety features, traditional updates, and employee coaching to mitigate the dangers of such evolved persistent threats.
Source credit : cybersecuritynews.com


