Turla APT Group Attacking European Ministry of Foreign Affairs
.webp)
The infamous developed continual chance (APT) community Turla, basically basically based in Russia, is speculated to be going after the European Ministry of Foreign Affairs.
This new cyber espionage strive presentations how progressive and continual Turla is.

The community has been active since 2004 and is known for its excessive-profile assaults on authorities companies and key firms worldwide.
The Attack Vector: Microsoft Outlook Exploited
Per Trendmicro reviews, the operation, which became as soon as due in August 2018, centered Microsoft Outlook and The Bat!, an Jap European favourite email consumer.
Turla desired to rep entry to deepest facts by hacking these net sites and sending all outgoing emails to attackers.
This contrivance now not handiest let the community snoop on conversations nonetheless additionally old email to ship facts to its voice and regulate (C&C) servers.
LunarWeb and LunarMail were old to compromise a European MFA and its diplomatic missions.
A gargantuan share of Turla’s arrangement in this operation became as soon as the utilization of particularly made PDF facts, which were potentially additionally old to attain the most valuable breach.
After they got into the systems, the community old their advanced toolkit, which incorporates backdoors and personalized malware, to stay to it high of them and retain energy over them.
Lunar toolset
Regardless of now not shiny your total preliminary compromise, researchers detected an set up-connected part in one in every of the server compromises: a compiled ASP.NET net page from these provide facts:
- aspnet_clientsystem_web.aspx
- aspnet_clientsystem_web.cs
System_web.aspx is a known IoC of China-aligned APT Hafnium, which exploits Microsoft Substitute Server vulnerabilities. We deem here’s a accident or unfounded flag.
The system_web.aspx page returns a harmless-making an strive Zabbix agent log. The SMSKey cookie secretly requires a password. The utilization of the password and salt Microsoft.SCCM.Change.Manager, an AES-256 key, and IV are generated to decode two embedded blobs, that are dropped to two short-term facts in a directory restricted from scanning.
Analyzers don’t know the password, nonetheless the file sizes match the Stage 1 loader and Stage 2 blob with the LunarWeb backdoor.
After the installers within the closing share, ogle on the loaders, and dwell by their payloads, researchers didn’t be taught about two backdoors sooner than.
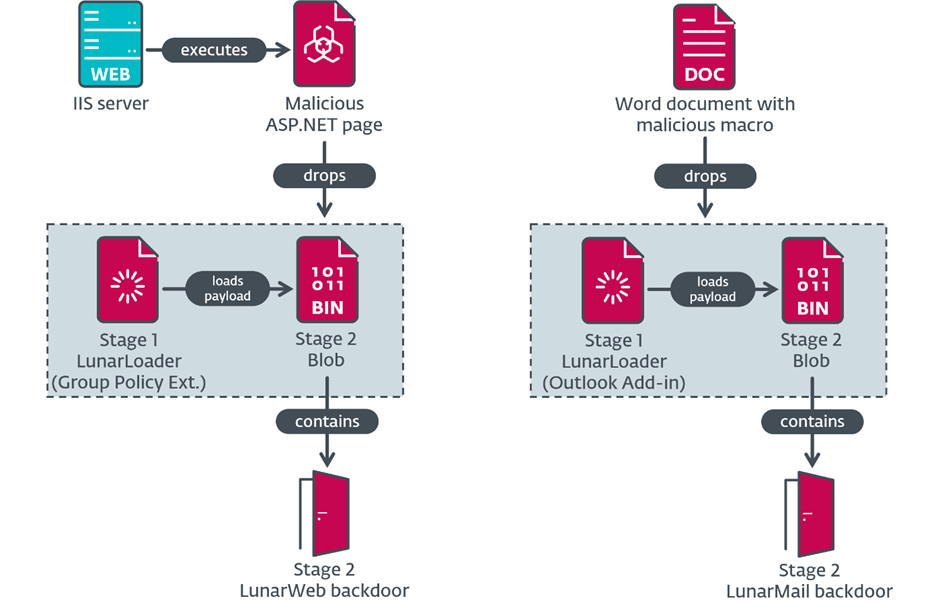
LunarLoader starts the execution sequence.
It decrypts the Stage 2 blob route and reads an encrypted payload the utilization of RC4, a symmetric key cipher.
As a change of a mutex or tournament, it opens and creates a mailslot with a particular title to make determined handiest one loader occasion is active.
The MD5 hash of the pc’s DNS enviornment title generates and verifies a decryption key.
The payload is decrypted with AES-256 to acquire a PE file. LunarLoader allocates PE image memory and decrypts an exported PE goal title to escape in a brand new thread. The goal has a reflective loader.
Payload decryption the utilization of DNS is an execution barrier. The loader handiest works within the supposed organization, which might also honest hinder diagnosis with out the enviornment title.
LunarLoader can escape by myself or in trojanized originate-provide tool.
The latter occurred with a trojanized AdmPwd, a Windows Native Administrator Password Resolution part.
| Persistence contrivance | Loader route(s) | Host direction of | Demonstrate |
| Community coverage extension | C:WindowsSystem32en-USwinnet.dll.mui C:Program FilesLAPSCSEAdmPwd.dll* | svchost.exe -okay GPSvcGroup | The AdmPwd dll is a known respectable file route of Microsoft LAPS. |
| Machine DLL replacement | C:WindowsSystem32tapiperf.dll | wmiprvse.exe | Changing a true Windows DLL. |
| Outlook add‑in | %USERPROFILE%Gpg4wingpgol.dll | outlook.exe | N/A |
It has been a truly long time since Turla modified its techniques and tools, which makes it one in every of the most developed and tricky APT teams.
The community is known for the utilization of both long-established and abnormal malware households, love Carbon and Kazuar, and for having voice and regulate systems that are in conserving with satellites.
Over time, Turla has on an everyday basis centered authorities companies, the militia, colleges, analysis labs, and drug firms.
Since this advertising and marketing campaign against the European Ministry of Foreign Affairs grew to alter into public, there had been requires extra cooperation between worldwide locations in hacking.
Sharing facts and the most productive ways to attain things is viewed as foremost for worldwide locations and teams to fight the threats that advance from divulge-sponsored gamers love Turla.
Regardless of sharing a loader, code overlaps, and directions, the backdoors use assorted C&C communication ways. LunarWeb, the most valuable backdoor, employs HTTP(S) to impersonate Windows Change net page visitors.
LunarMail, the 2nd backdoor, uses PNG or PDF facts to take data from Outlook by contrivance of email.
MITRE ATT&CK ways
This desk became as soon as constructed the utilization of version 15 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Reconnaissance | T1591 | Safe Victim Org Info | LunarMail’s communication contrivance indicates prior data about compromised institutions. |
| Resource Building | T1583.002 | Own Infrastructure: DNS Server | Stage 0 macro pings a net page from free DNS cyber net net hosting supplied by ClouDNS. |
| T1583.003 | Own Infrastructure: Digital Non-public Server | Turla has old VPS cyber net net hosting suppliers for C&C servers. | |
| T1584.003 | Compromise Infrastructure: Digital Non-public Server | Turla has old compromised VPSes for C&C functions. | |
| T1586.002 | Compromise Accounts: Email Accounts | Turla has old likely compromised email accounts for communication with the LunarMail backdoor. | |
| T1587.001 | Own Capabilities: Malware | Turla has developed personalized malware, including loaders and backdoors. | |
| Execution | T1047 | Windows Management Instrumentation | LunarWeb obtains system facts by the utilization of WMI queries. |
| T1059 | Present and Scripting Interpreter | LunarWeb and LunarMail can attain Lua scripts. | |
| T1059.001 | Present and Scripting Interpreter: PowerShell | LunarWeb can attain PowerShell commands. | |
| T1059.003 | Present and Scripting Interpreter: Windows Present Shell | LunarWeb can attain shell commands by contrivance of cmd.exe. | |
| T1059.005 | Present and Scripting Interpreter: Visible Fundamental | Stage 0 Discover sage contains a VBA macro. | |
| T1106 | Native API | LunarWeb and LunarMail use varied Windows APIs. | |
| T1204.002 | Particular person Execution: Malicious File | Info from the Native Machine | |
| Persistence | T1137.006 | Residence of job Utility Startup: Add-ins | LunarMail loader is persevered as an Outlook add-in. |
| T1547 | Boot or Logon Autostart Execution | A LunarWeb loader is persevered as a Community Coverage extension. | |
| T1574 | Hijack Execution Circulate | A LunarWeb loader is persevered by changing the system DLL tapiperf.dll. | |
| Protection Evasion | T1027 | Obfuscated Files or Info | LunarWeb and LunarMail are AES-256 encrypted on disk. |
| T1027.003 | Obfuscated Files or Info: Steganography | LunarMail levels exfiltration data into a PNG image or PDF sage. | |
| T1027.007 | Obfuscated Files or Info: Dynamic API Resolution | LunarMail dynamically resolves MAPI functions. | |
| T1027.009 | Obfuscated Files or Info: Embedded Payloads | LunarMail installer has payloads embedded in a DOCX structure sage. | |
| T1036.005 | Masquerading: Match Legitimate Name or Predicament | Filenames old by LunarWeb and LunarMail loading chains mimic respectable facts. | |
| T1070.004 | Indicator Elimination: File Deletion | LunarWeb and LunarMail can uninstall themselves by deleting their loading chain. | |
| T1070.008 | Indicator Elimination: Definite Mailbox Info | LunarMail deletes email messages old for C&C communications. | |
| T1140 | Deobfuscate/Decode Files or Info | LunarWeb and LunarMail decrypt their strings the utilization of RC4. | |
| T1480.001 | Execution Guardrails: Environmental Keying | LunarLoader decrypts its payload the utilization of a key derived from the DNS enviornment title. | |
| T1620 | Reflective Code Loading | LunarWeb and LunarMail are done the utilization of a reflective loader. | |
| Discovery | T1007 | Machine Service Discovery | LunarWeb retrieves a checklist of companies. |
| T1016 | Machine Community Configuration Discovery | LunarWeb retrieves community adapter facts. | |
| T1057 | Job Discovery | LunarWeb retrieves a checklist of working processes. | |
| T1082 | Machine Info Discovery | LunarWeb retrieves system facts comparable to OS version, BIOS version, enviornment title, and atmosphere variables. LunarMail retrieves atmosphere variables. | |
| T1518.001 | Tool Discovery: Security Tool Discovery | LunarWeb discovers place in security solutions by contrivance of the WMI inquire wmic /Namespace:\rootSecurityCenter2 Route AntiVirusProduct Gain *. | |
| Series | T1005 | LunarWeb and LunarMail use a statically linked Zlib library for compression of restful data. | LunarWeb and LunarMail can add facts from the compromised machine. |
| T1074.001 | Info Staged: Native Info Staging | LunarMail levels data in a directory in %TEMP%. | |
| T1113 | Cloak Capture | LunarMail can capture screenshots. | |
| T1114.001 | Email Series: Native Email Series | LunarMail collects recipients of sent email messages and might per chance per chance salvage email addresses of Outlook profiles. | |
| T1560.002 | Archive Accrued Info: Archive by contrivance of Library | LunarWeb and LunarMail use a statically linked Zlib library for the compression of restful data. | |
| Present and Preserve a watch on | T1001.002 | Info Obfuscation: Steganography | LunarWeb can acquire commands hidden in JPG or GIF photography. LunarMail receives commands hidden in PNG photography and exfiltrates data hidden in PNG photography or PDF documents. |
| T1001.003 | Info Obfuscation: Protocol Impersonation | LunarWeb impersonates respectable domains in C&C communications by the utilization of a spurious Host header and known URIs. | |
| T1071.001 | Utility Layer Protocol: Web Protocols | LunarWeb uses HTTP for C&C communications. | |
| T1071.003 | Utility Layer Protocol: Mail Protocols | LunarMail uses email messages for C&C communications. | |
| T1090.001 | Proxy: Internal Proxy | LunarWeb can use an HTTP proxy for C&C communications. | |
| T1095 | Non-Utility Layer Protocol | Stage 0 macro pings the C&C server, utilizing ICMP protocol. | |
| T1132.001 | Info Encoding: Typical Encoding | LunarWeb can also honest acquire base64-encoded data from the C&C server. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | LunarWeb and LunarMail encrypt C&C communications the utilization of AES-256. | |
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | LunarWeb and LunarMail encrypt the AES key old in C&C communications the utilization of RSA-4096. | |
| Exfiltration | T1020 | Computerized Exfiltration | LunarWeb and LunarMail robotically exfiltrate restful data to the C&C server. |
| T1030 | Info Switch Size Limits | LunarWeb splits exfiltrated data above 1.33 MB into multiple smaller chunks. LunarMail limits the scale of email attachments containing exfiltrated data. | |
| T1041 | Exfiltration Over C2 Channel | LunarWeb and LunarMail exfiltrate data over the C&C channel. |
Source credit : cybersecuritynews.com

