UAC Bypass: 3 Methods Used Malware In Windows 11 in 2024
UAC Bypass: 3 Solutions Common Malware In House windows 11 in 2024
User Legend Preserve an eye fixed on (UAC) is one in every of the protection measures provided by Microsoft to prevent malicious utility from executing without the person’s files. On the different hand, contemporary malware has found effective systems to bypass this barrier and kind sure restful deployment on the host machine. Listed below are three systems commonly found in malware samples uploaded to ANY.RUN’s public submissions database.
What is User Legend Preserve an eye fixed on?
User Legend Preserve an eye fixed on (UAC) works by prompting the person for permission sooner than performing sure tasks that require administrative-stage gain entry to. This kind, even supposing a person is logged in with an administrator memoir, they’re notified about the functionality dangers of the task they’re about to assign. The suggested on the entire involves a message describing the action that will be taken, the title of the program or person inquiring for gain entry to, and alternatives to allow or cancel the action.
How Malware Dodges UAC
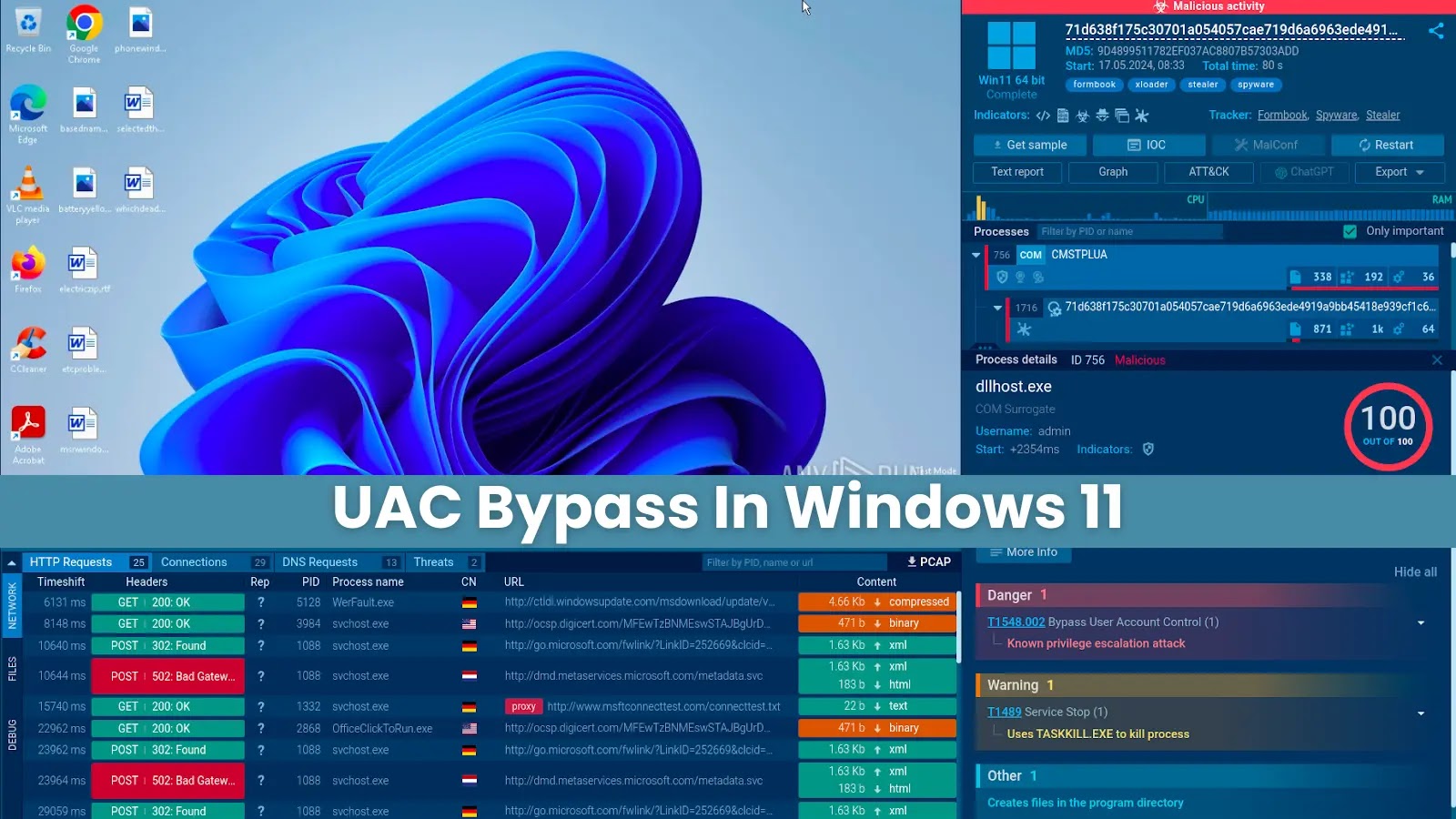
COM Interface Exploitation
The Ingredient Object Model (COM) is a binary interface popular for utility parts and a significant section of House windows operating systems, as a lot of their capabilities are constructed on it. COM provides a fixed manner for purposes to communicate with every assorted and with the OS.
Malware can exploit COM by taking profit of sure objects which fill the “Elevation â Allow â 1” entry within the House windows registry. This entry permits the article to flee with administrator privileges, bypassing the UAC suggested. This would possibly per chance also be a predominant safety vulnerability, because it permits malicious utility to assign actions that can per chance per chance on the entire require the person’s explicit permission.
Some of the most inclined COM objects include:
- cmstplua.dll
- colorui.dll
- wscui.cpl
Instance:
Thanks to Threat Intelligence Lookup, we’re going to have the power to easily get malware samples that circumvent UAC. Letâs detect threats the expend of cmstplua.dll.
To total this, we simply fill to submit the next expect, which involves the map’s ID connected to cmstplua.dll.

The service responds with a hundred assorted malware analysis classes launched in the ANY.RUN sandbox, every declaring the merchandise we laid out in our expect.Â

We can click on any of those classes to survey them in-depth.
As an instance, right here is a session that encompasses a sample of the Formbook malware that utilized cmstplua.dll to sidestep UAC.
After opening the sandbox session, we’re going to have the power to stumble on additional crucial points of the assault, akin to the Ways, Ways, and Procedures (TTPs) popular by the malware and its indicators of compromise.
Registry ModificationÂ
One other manner for bypassing UAC depends on modifying the House windows registry’s ms-settings keys. Some packages on House windows flee with elevated privileges by default. Thought to be one of them is fodhelper that, when executing, before the entire thing attempts to gain entry to a non-existent registry entry, HKCUClassesms-settingsshellopenuncover, sooner than passing on to the next one, HKCRshellopenuncover that does exist.
Attackers would possibly per chance also fair leverage this by creating and modifying the principle registry entry, which does no longer require administrative privileges. Thus, they will hijack the registry and kind sure that the malware initiates with out a UAC suggested being shown to the person.
Instance:

Here is a sandbox analysis session of the BlankGrabber malware that employs one of these averting exhibiting the UAC suggested.Â
Countless UAC Commended Loop
On this kind, the person is shown the UAC suggested once extra every time they’re trying and shut it. The diagram right here is to power the functionality sufferer into agreeing to flee the applying to cast off the window. But, as soon as they agree, the malware starts executing on their machine.
Instance:

Take a look at out this analysis session that comprises the Dcrat malware that depends on the suggested loop to assign its foothold on the machine.
Source credit : cybersecuritynews.com