USB Malware Chained with Text Strings on Legitimate Websites Attacks Users

Despite the evolution of several tools and ways, threat actors serene toddle along with the worn system to attack victims for malicious functions. One such threat actor is UNC4990, which makes use of USB devices to milk victims. UNC4990 is a financially motivated threat actor and has been conducting campaigns since 2020.
There used to be a valid evolution of this threat actor’s actions. With that being said, doubtlessly the most unusual ways fervent the usage of normal and legit internet sites such as GitHub, GitLab, Ars Technica and Vimeo.

As well to, the threat actor has been utilizing EMPTYSPACE downloader and QUIETBOARD backdoor. EMPTYSPACE is in a position to executing any payload served from the negate and regulate servers, and QUIETBOARD is additionally delivered utilizing EMPTYSPACE.
AI-Powered Security for Enterprise Email Security
Trustifi’s Evolved threat protection prevents the widest spectrum of refined attacks before they reach a person’s mailbox. Strive Trustifi Free Possibility Scan with Refined AI-Powered Email Security .
USB Malware Chained with Text Strings
Initial Vector
Consistent with the experiences shared with Cyber Security News, the threat actor begins the infection chain by delivering the USB drives to the victims whatsoever of social engineering. Once the sufferer connects the USB to their utility, the USB removable utility is shown with a shortcut (.LNK extension) under the provider establish.
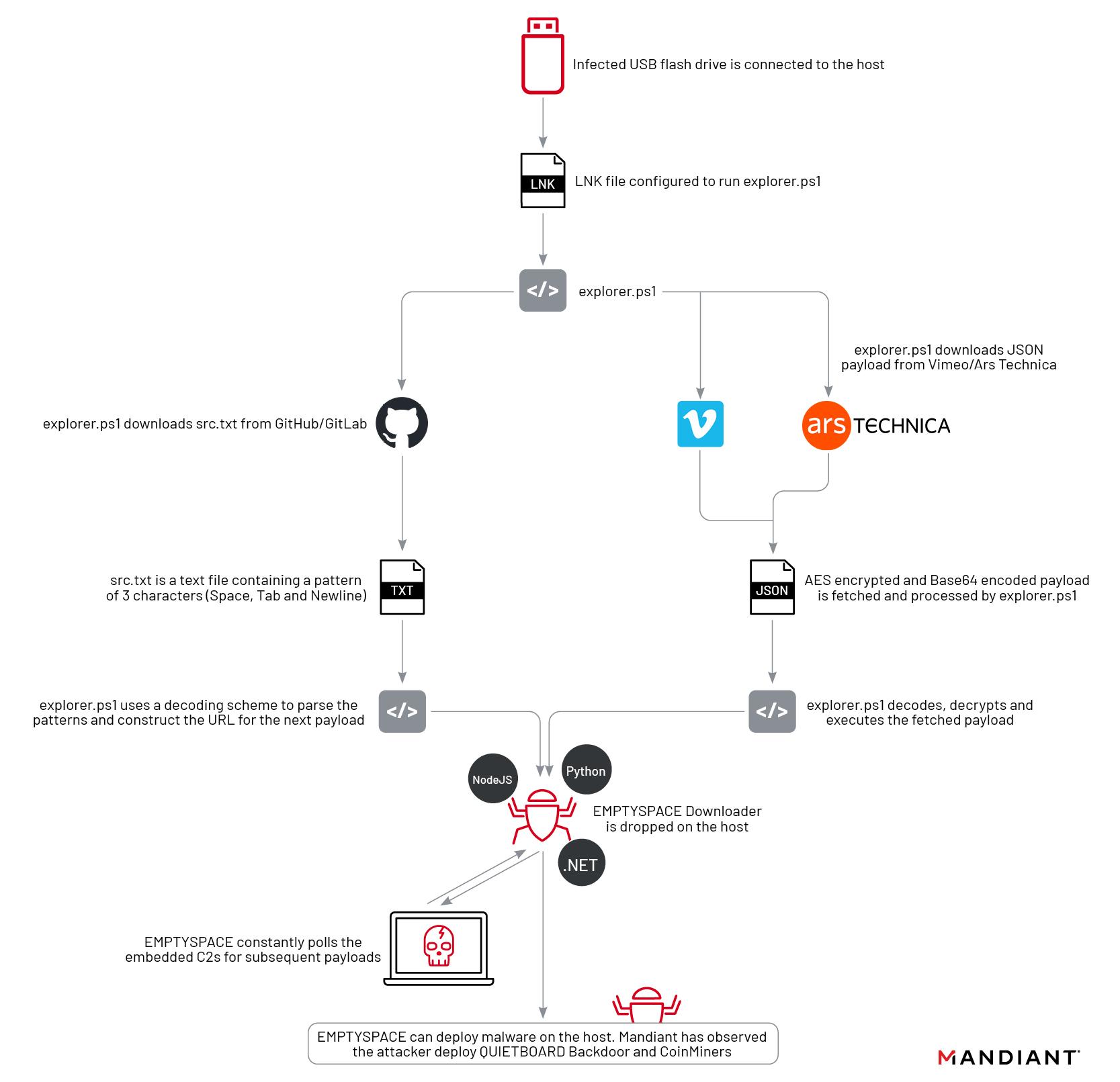
When the victims originate this malicious LNK shortcut file, it executes a PowerShell script (explorer.ps1), which comprises the next negate.
“C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle has hidden -NoProfile -nologo -ExecutionPolicy ByPass -File explorer.ps1”
The explorer.ps1 is an encoded PowerShell script that tests for explicit conditions and fetches the Runtime Broker.exe, which is the EMPTY SPACE downloader.
Timeline
From the muse of 2023, the threat actor changed GitHub with Vimeo, a video-sharing websites. A video used to be added to Vimeo wherein the description had the laborious-coded payload. Alternatively, this video used to be removed now. Additionally, the Vimeo URL used to be additionally embedded throughout the explorer.ps1 script.
In mid of December 2023, it used to be realized that the threat actor had been utilizing Ars Technica by utilizing a image embedded with the payload. As a backup, the threat actor had additionally updated the EMPTY SPACE serving URL, which had an extra string.
Furthermore, there were several variations of EMPTYSPACE loader feeble by the threat actor, such because the Node JS version, .NET version, and Python version alongside QUIETBOARD.
This Python-based completely backdoor can reach arbitrary code, cryptocurrency theft, USB pressure infection, screenshotting, knowledge gathering, and C2 communications.
Indicators of Compromise
Host-based completely IOCs
| IOC | SHA-256 | Associated Malware Household |
| explorer.ps1 | 72f1ba6309c98cd52ffc99dd15c45698dfca2d6ce1ef0bf262433b5dfff084be | PowerShell Script |
| 98594dfae6031c9bdf62a4fe2e2d2821730115d46fca61da9a6cc225c6c4a750 | ||
| d09d1a299c000de6b7986078518fa0defa3278e318c7f69449c02f177d3228f0 | ||
| 7c793cc33721bae13e200f24e8d9f51251dd017eb799d0172fd647acab039027 | ||
| 6fb4945bb73ac3f447fb7af6bd2937395a067a6e0c0900886095436114a17443 | ||
| %TEMP%Runtime Broker.exe | a4f20b60a50345ddf3ac71b6e8c5ebcb9d069721b0b0edc822ed2e7569a0bb40 | EMPTYSPACE Downloader (Node.JS Variant) |
| Runtime Broker.exe | 8a492973b12f84f49c52216d8c29755597f0b92a02311286b1f75ef5c265c30d | EMPTYSPACE Downloader (.NET Variant) |
| C:Program Files (x86)WinSoft Update Carrierbootstrap.pyc | V1: 060882f97ace7cb6238e714fd48b3448939699e9f085418af351c42b401a1227 | EMPTYSPACE Downloader (Python Variant) |
| V2: 8c25b73245ada24d2002936ea0f3bcc296fdcc9071770d81800a2e76bfca3617 | ||
| V3: b9ffba378d4165f003f41a619692a8898aed2e819347b25994f7a5e771045217 | ||
| V4: 84674ae8db63036d1178bb42fa5d1b506c96b3b22ce22a261054ef4d021d2c69 | ||
| C:Program Files (x86)WinSoft Update Carrierprogram.pyz | 15d977dae1726c2944b0b4965980a92d8e8616da20e4d47d74120073cbc701b3 | QUIETBOARD Backdoor |
| 26d93501cb9d85b34f2e14d7d2f3c94501f0aaa518fed97ce2e8d9347990decf | ||
| 26e943db620c024b5e87462c147514c990f380a4861d3025cf8fc1d80a74059a | ||
| C:dwelling windowsruntimebroker .exe | 71c9ce52da89c32ee018722683c3ffbc90e4a44c5fba2bd674d28b573fba1fdc | QUIETBOARD associated file |
| C:Program Files (x86)pyt37python37.zip | 539a79f716cf359dceaa290398bc629010b6e02e47eaed2356074bffa072052f | QUIETBOARD associated file |
Network-Primarily based completely IOCs
URL
- hxxps://bobsmith.apiworld[.]cf/license.php
- hxxps://arstechnica[.]com/civis/contributors/frncbf22.1062014/about/
- hxxps://evinfeoptasw.dedyn[.]io/updater.php
- hxxps://wjecpujpanmwm[.]tk/updater.php?from=USB1
- hxxps://eldi8.github[.]io/src.txt
- hxxps://evh001.gitlab[.]io/src.txt
- hxxps://vimeo[.]com/api/v2/video/804838895.json
- hxxps[://]huge[.]ga/wp-admin[.]php
- hxxp[://]studiofotografico35mm[.]altervista[.]org/updater[.]php
- hxxp[://]ncnskjhrbefwifjhww[.]tk/updater[.]php
- hxxp[://]geraldonsboutique[.]altervista[.]org/updater[.]php
- hxxps[://]wjecpujpanmwm[.]tk/updater[.]php
- hxxps[://]captcha[.]grouphelp[.]high/updater[.]php
- hxxps[://]captcha[.]tgbot[.]it/updater[.]php
- hxxps://luke.compeyson.eu[.]org/runservice/api/public.php
- hxxps[://]luke[.]compeyson[.]eu[.]org/wp-admin[.]php
- hxxps://luke.compeyson.eu[.]org/runservice/api/public_result.php
- hxxps://eu1.microtunnel[.]it/c0s1ta/index.php
- hxxps[://]davebeerblog[.]eu[.]org/wp-admin[.]php
- hxxps://lucaespo.altervista[.]org/updater.php
- hxxps://lucaesposito.herokuapp[.]com/c0s1ta/index.php
- hxxps://euserv3.herokuapp[.]com/c0s1ta/index.php
Source credit : cybersecuritynews.com


