VASTFLUX – Hackers Exploiting Restricted in-app Environments to Run Malicious Ads

VASTFLUX, a wide-scale neat, and refined ad fraud operation had been now not too prolonged within the past taken down by cybersecurity researchers at HUMAN Security Inc.
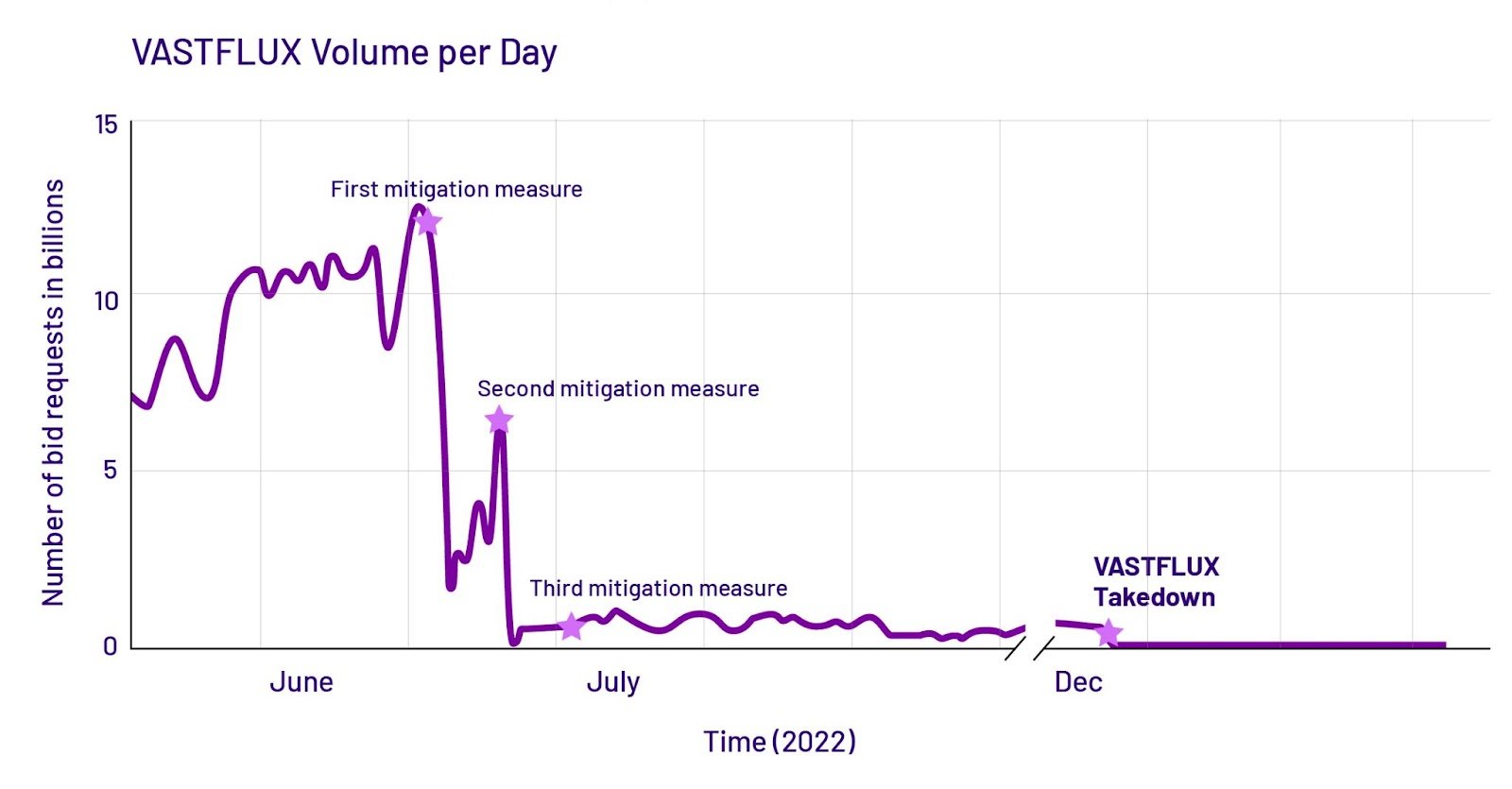
On a each day foundation, 12 billion classified ads are requested by VASTFLUX, which turned into as soon as spoofing 1,700 apps on 11 million devices, focusing on 120 publishers. Quite quite a bit of key components of collective safety are highlighted by VASTFLUX’s sophistication.
VASTFLUX is a malvertising operation by which the attackers manipulated ad creatives by injecting JavaScript and stacking extra than one video players on top of each diversified, getting paid for the total classified ads even supposing none of them had been considered to the user.
In picture to lead particular of ad verification tags, VASTFLUX deployed a code that prevented the plan from being detected.
Discovery of VASTFLUX Marketing and marketing campaign
When it comes to its feature, VASTFLUX combines two terms. All the device via this operation, the VAST template turned into as soon as exploited to affirm digital video classified ads. ‘Flux’ refers back to the knowing that of Mercurial Flux, a technique susceptible by cybercriminals as a vogue to evade detection and evade detection systems.
The operation turned into as soon as realized by the Satori physique of workers from HUMAN while investigating the spoofing assault against an iOS utility.
This watch realized that cybercriminals had been exploiting the shrimp signal that made itself available to verification partners in a centered atmosphere which turned into as soon as exploited to fabricate a highly refined plan. It’s miles important to picture that this entails in-app promoting essentially on iOS.
Sooner or later, the ad fraud stepped forward into spoofing bids on one platform to appear on yet another, ensuing within the looks of classified ads on each platforms. This made it not seemingly for wrong-platform attacks to be deterred from taking express.
To be ready to gain extra insight into the fraud’s website online visitors volumes and the verification tags at possibility of verify the classified ads had been proper, Human partnered with its partners within the HUMAN Collective to assemble extra recordsdata.
VASTFLUX Operation
As a outcomes of the assault, malicious JavaScript code turned into as soon as injected into digital adverts. Fraudsters took revenue of this exploit by stacking up hundreds of video classified ads on top of one yet another so that they’d perchance also register views for classified ads that had been now not considered by the user.
Nonetheless, essentially it entails four steps, and here below we’ve got mentioned them:-
- Step One: JavaScript Injection
- Step Two: C2 Directions
- Step Three: A Playlist of Classified ads
- Step Four: Fraud Monitoring Evasion
By imposing a non-public takedown effort, Human Security turned into as soon as ready to affirm an end to this operation. Nonetheless, it’s light being actively monitored by the firm, as this may perchance occasionally be particular extra security.
Ideas
Right here below we’ve got mentioned the total solutions equipped by the specialists that users can apply to preserve alert and mitigate:-
- In a rapid time period, the battery lifetime of the tool deteriorates considerably.
- Within the center of the evening, the tool’s veil activates unexpectedly.
- The efficiency of the tool impulsively decreases.
- Reckoning on the day of the week, the volume of recordsdata being susceptible jumps dramatically.
- Frequent and unexpected crash occurs.
It’s magnificent that VASTFLUX is down right now, but it doesn’t indicate that the story is over. As the investigation continues, security analysts will be making an are attempting out for added clues as to who the perpetrators are as well as any future adaptations.
Source credit : cybersecuritynews.com

