Vidar Stealer Employs Advanced Tactics to Evade Defense Solutions
.webp)
The Vidar Stealer has emerged as a potent and advanced malware, posing important risks to both organizations and folk.
This recordsdata-stealing malware, operating as a malware-as-a-provider (MaaS), has been meticulously analyzed by CYFIRMA, revealing its developed ways and tactics for evading detection and maximizing its malicious actions.


Overview of Vidar Stealer
Vidar Stealer, written in C++, is succesful of stealing a large assortment of information from compromised systems.
It targets deepest recordsdata, net browser recordsdata, cryptocurrency wallets, financial recordsdata, impartial correct-attempting files, communication functions, and more.
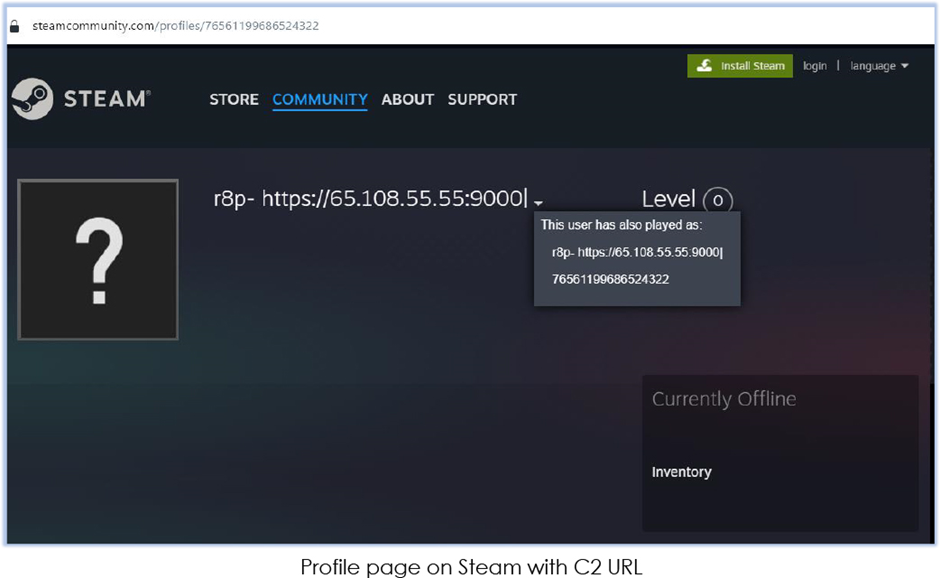
Sold on the murky net and underground forums, Vidar Stealer leverages social media platforms as share of its uncover-and-withhold watch over (C2) infrastructure, making it a formidable risk within the cybersecurity landscape.
Key Findings
- Recordsdata-Stealing Capabilities: Vidar Stealer targets a large assortment of information, including deepest and financial recordsdata, utility recordsdata, and machine project.
- Malware-as-a-Provider: The malware is sold on the murky net and underground forums, with customizable functionality.
- Evasion Tactics: Vidar employs developed evasion tactics, corresponding to obfuscating malicious code, injecting code into dependable Windows processes, and the usage of self-signed certificates to detect network interception.
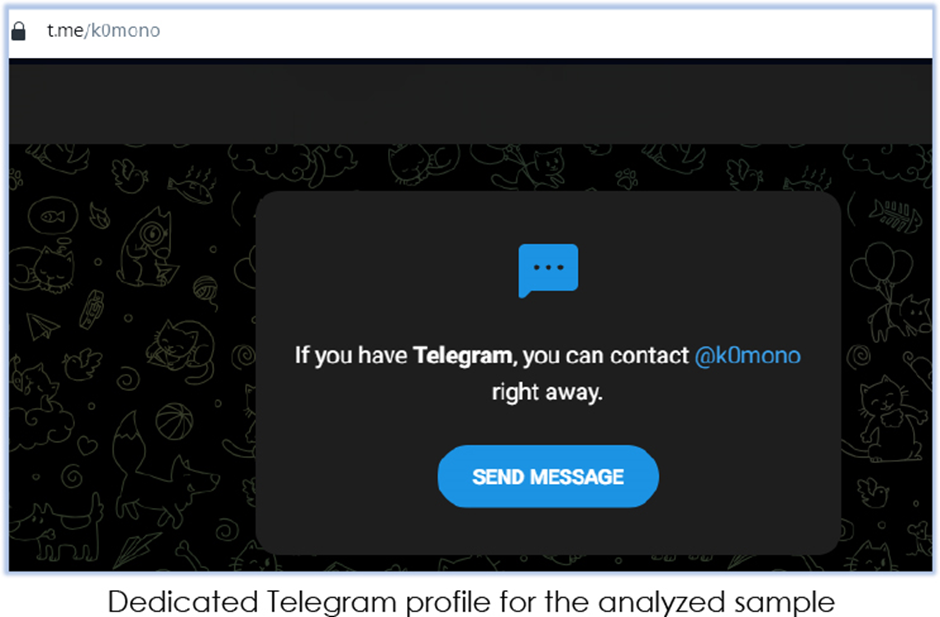
- Social Media Utilization: The malware makes exhaust of social media platforms relish Telegram and Steam to originate C2 particulars, updates, and instructions.
- Collaboration with Diversified Malware: Vidar has been seen participating with rather about a malware strains, corresponding to STOP/Djvu ransomware, to maximise its impact.
Behavioral & Code Analysis
1st Stage Execution
On the starting up, Vidar Stealer retrieves atmosphere particulars the usage of API calls and terminates the project if a debugger or diagnosis atmosphere is detected.
2nd Stage Execution
If no diagnosis atmosphere is detected, the malware decodes the direct of the .recordsdata share the usage of bitwise XOR operations, revealing artifacts corresponding to C2 URLs and client-agent particulars.
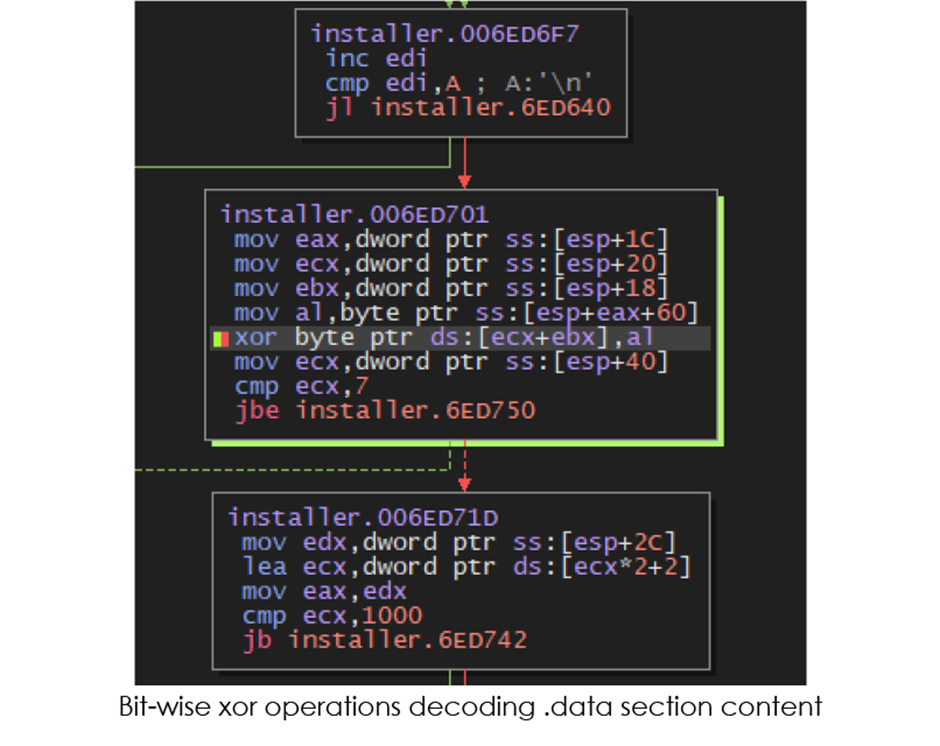
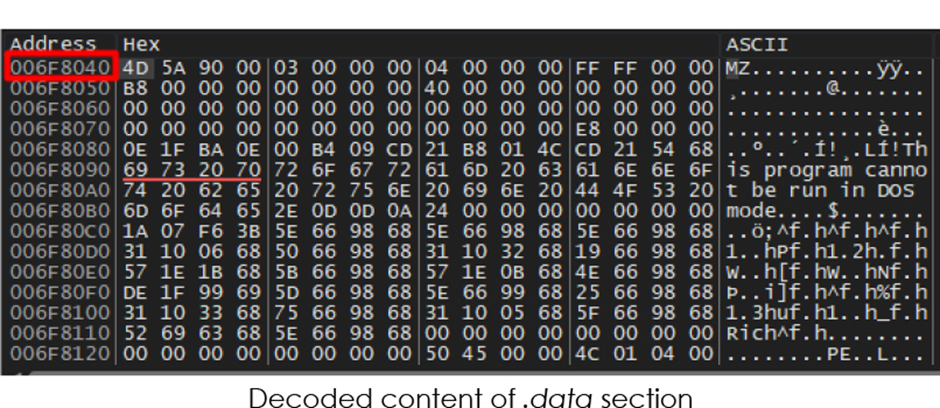
third Stage Execution
The malware creates a suspended project (RegAsm.exe) and injects code into it, which then resumes and terminates the customary project.
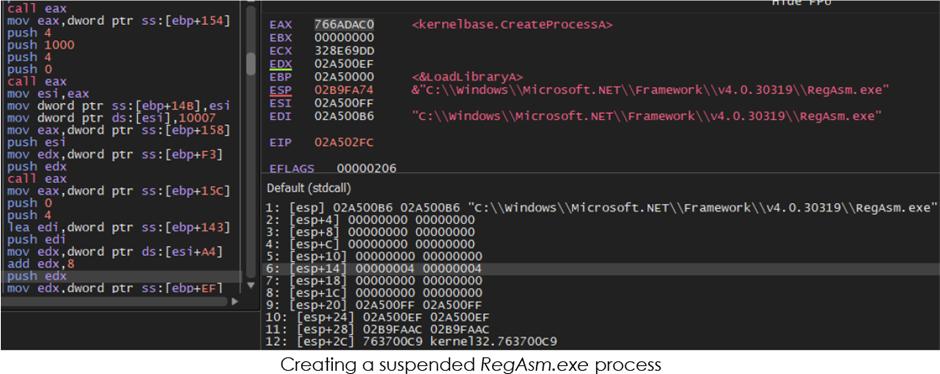
4th Stage Execution
RegAsm.exe executes the injected code, setting up a connection to retrieve C2 recordsdata from URLs embedded in social media profiles.
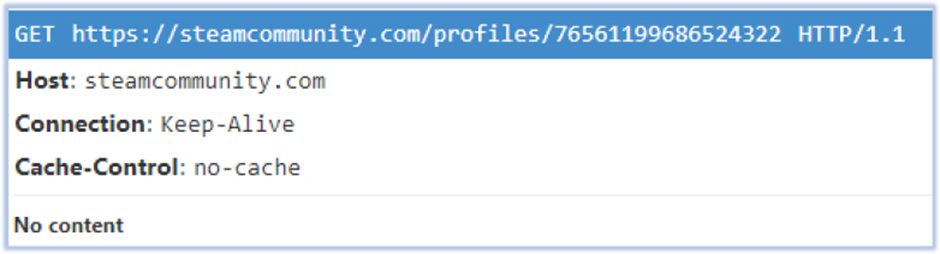
The malware exfiltrates recordsdata to the C2 server and downloads extra binaries to present a enhance to its operation.
Exfiltration Process
Vidar Stealer collects and exfiltrates recordsdata from net browsers, cryptocurrency wallets, impartial correct-attempting files, and machine-particular directories.
The details is compiled staunch into a folder with determined file names and exfiltrated to the C2 server.
The malware then deletes the gathered recordsdata to set up away with traces of exfiltration.
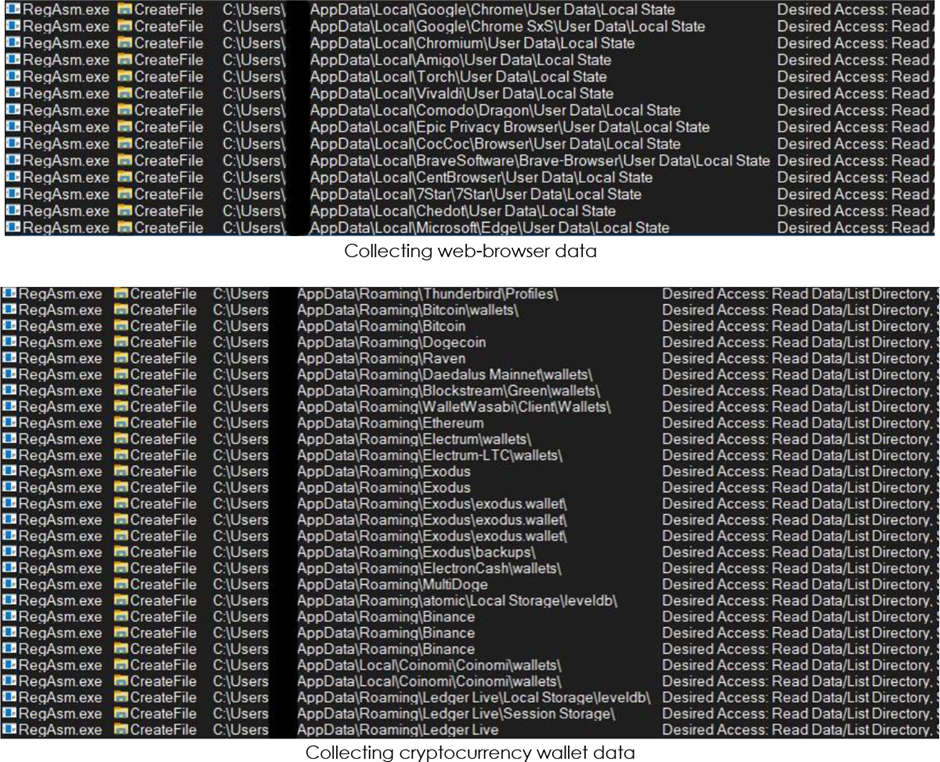
Vidar-Stealer Capabilities
- Recordsdata Gathering: Collects a huge number of impartial correct-attempting recordsdata from infected systems.
- Recordsdata Exfiltration: Transmits stolen recordsdata over right channels to C2 servers.
- Evasion Tactics: Avoids detection by security tool via assorted systems.
- Process Injection: Targets dependable Windows processes for code injection.
- Social Media Utilization: Social media platforms are passe for C2 infrastructure and malware promotion.
- Collaboration with Diversified Malware: Works with rather about a malware strains to pork up its impact.
The diagnosis of Vidar Stealer underscores the complexity and dynamic nature of contemporary cyber threats.
Its multifaceted capabilities, including recordsdata gathering, recordsdata exfiltration, evasion tactics, and collaboration with rather about a malware strains, highlight the necessity for sturdy cybersecurity measures and proactive defense systems.
Organizations and folk must remain vigilant and adopt complete security practices to mitigate the risks posed by threats relish Vidar Stealer.
To lower the risks linked with Vidar Stealer, users may perchance per chance well aloof train warning when opening files from untrustworthy sources or clicking on new hyperlinks.
Deploying revered antivirus tool, guaranteeing common tool updates, and staying vigilant in opposition to social engineering ways are well-known steps in bolstering security in opposition to such threats.
Collaboration between cybersecurity mavens and platform administrators is highly well-known for promptly figuring out and addressing these threats, resulting in a safer online atmosphere.
As cyber threats evolve, training and consciousness campaigns are well-known in equipping folk with the knowledge to acknowledge and evade malware relish Vidar Stealer.
Indicators Of Compromise
| S/N | Indicators | Form | Context |
| 1 | 7e74918f0790056546b862fa3e114c2a | File | installer.exe |
| 2 | fed19121e9d547d9762e7aa6dd53e0756c414bd0a0650e38d6b0c01b000ad2fc | File | installer.exe |
| 3 | 90e744829865d57082a7f452edc90de5 | File | sqlx[1].dll |
| 4 | 036a57102385d7f0d7b2deacf932c1c372ae30d924365b7a88f8a26657dd7550 | File | sqlx[1].dll |
| 5 | https[:]//steamcommunity[.]com/profiles/76561199686524322 | URL | C2 |
| 6 | https[:]//t[.]me/k0mono | URL | C2 |
| 7 | https[:]//65.108.55.55[:]9000 | URL | C2 |
| 8 | https[:]//91.107.221.88[:]9000 | URL | C2 |
| 9 | 65[.]108[.]55[.]55 | IP address | C2 |
| 10 | 91[.]107[.]221[.]88 | IP address | C2 |
Source credit : cybersecuritynews.com

