Virustotal Shares New Ideas to Track Threat Actors
%20(1).webp)
In a most novel presentation at the FIRST CTI in Berlin and Botconf in Good, VirusTotal unveiled revolutionary tips on how to discover adversary activity by focusing on pictures and artifacts dilapidated right via the preliminary stages of the murder chain.
This methodology targets to toughen threat making an are attempting and detection engineering by inspecting samples built within the weaponization and provide phases.
Traditionally, threat making an are attempting and detection engineering hang focused on the latter stages of the murder chain, from execution to actions on dreams.
Right here’s on account of the abundance of files on hand in these phases, making it more straightforward to gape for clues the usage of endpoint detection and response (EDR), security knowledge and occasion management (SIEM), and various alternate choices.
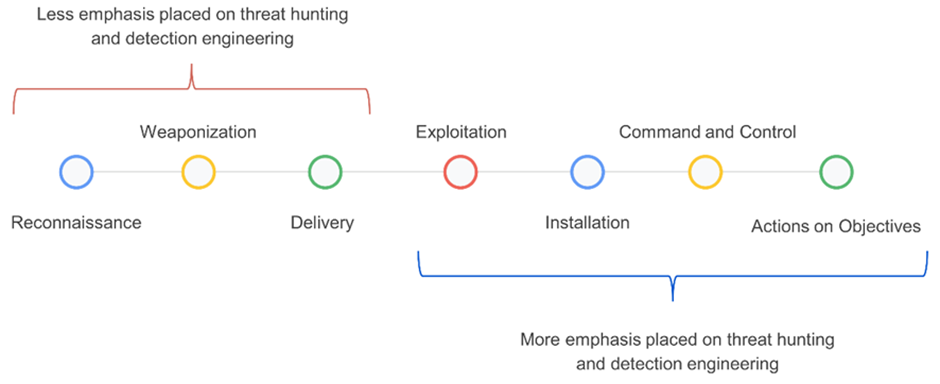
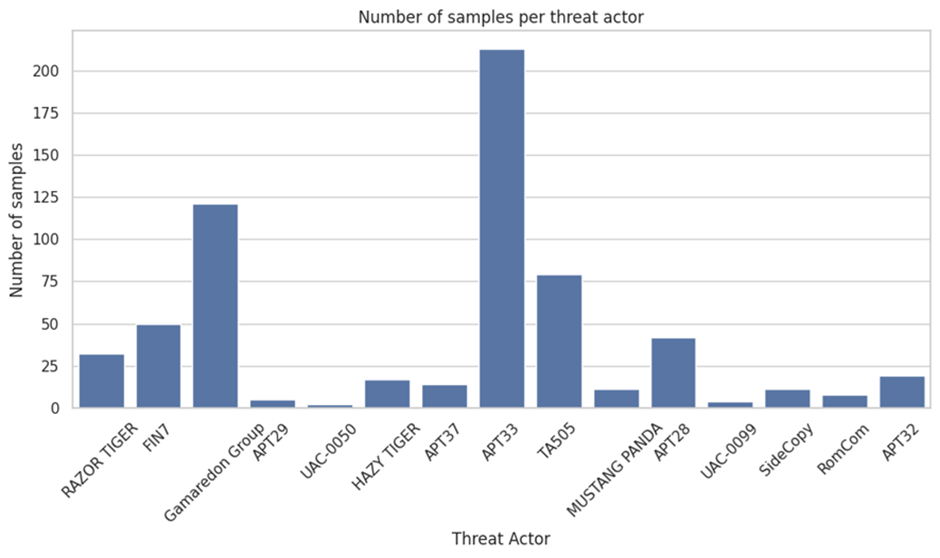
VirusTotal’s original methodology makes a speciality of detecting suspicious Microsoft Bother of business paperwork (Observe, Excel, and PowerPoint), PDF files, and emails.
Analysts can immediate name doable threats by leveraging colours in most cases dilapidated in threat intelligence platforms—inexperienced for benign and red for malicious.
Exploring Embedded Details in Bother of business Paperwork
When a Microsoft Bother of business file is created, it generates a series of embedded XML files containing knowledge about the file.
VirusTotal has identified three styles of embedded files inside Bother of business paperwork that would possibly also be in particular important for threat making an are attempting:
- Photos: Normally dilapidated by threat actors to originate paperwork appear legitimate.
- [Content_Types].xml: Specifies the relate material kinds and relationships right via the Bother of business Birth XML (OOXML) file.
- Kinds.xml: Stores stylistic definitions for the file, providing constant formatting directions.
VirusTotal hypothesizes that if malicious Microsoft Observe paperwork are copied and pasted right via the weaponization course of, the hashes of the [Content_Types].xml and styles.xml files will likely remain the same.
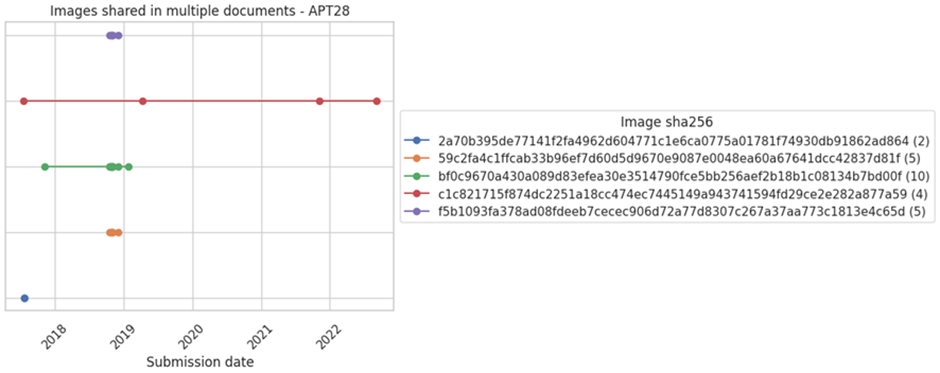
APT28 – Photos
APT28 has been found to reuse pictures across assorted provide samples.
As an illustration, an describe of a hand dilapidated in false Observe paperwork for resort reservations used to be identified in a pair of paperwork over quite loads of years.
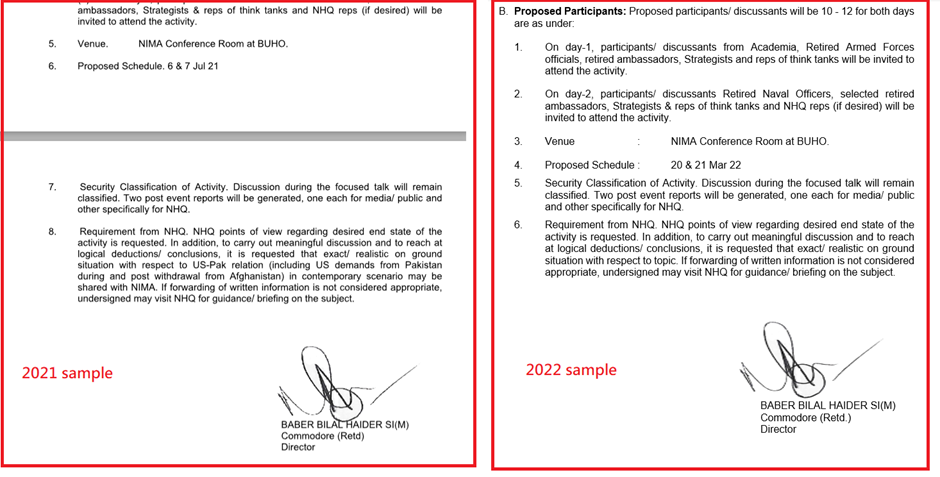
SideWinder – Photos
SideWinder, incessantly referred to as RAZER TIGER, has reused pictures of their operations against militia targets in Pakistan.
One indispensable instance is the signature of Baber Bilal Haider, dilapidated in a pair of paperwork.
Gamaredon – [Content_Types].xml and styles.xm
Gamaredon has reused styles.xml and [Content_Types].xml files in assorted paperwork, revealing original samples.
VirusTotal’s retrohunt identified patterns in these files, leading to the discovery of additional malicious paperwork.
![Virustotal Shares New Ideas to Track Threat Actors 17 [Content_Types].xml shared in a pair of paperwork by Gamaredon Group](https://cybersecuritynews.com/wp-content/uploads/2024/05/image-70.png)
AI to the Rescue
VirusTotal utilized the VirusTotal API to get and unzip a diagram of Bother of business paperwork dilapidated for provide, obtaining all embedded pictures.
They then dilapidated Gemini to automatically checklist these pictures, helping within the identification of suspicious paperwork.
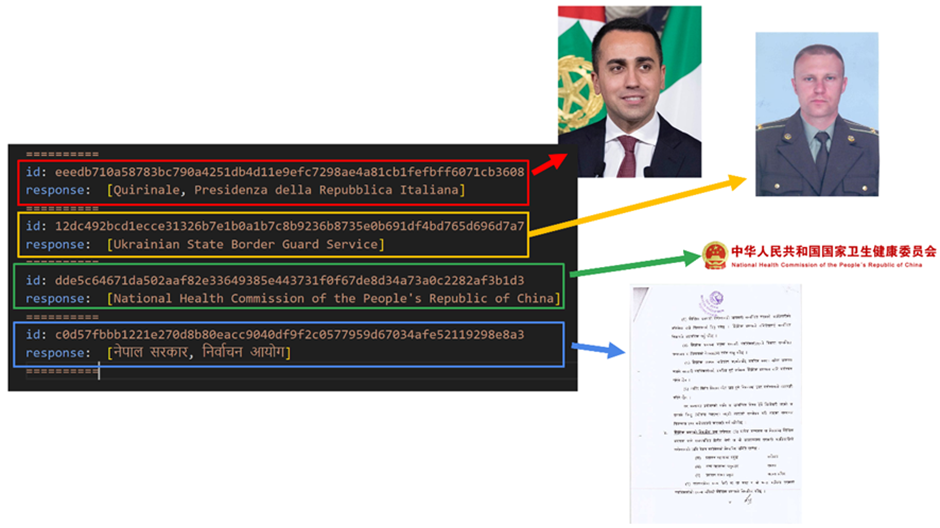
PDF Paperwork and Email Details
Unlike Bother of business paperwork, PDF files make not have embedded XML files or pictures. However, Adobe Acrobat Reader generates a thumbnail of the first web page in BMP format, which is able to be dilapidated for pivoting.
VirusTotal demonstrated this with examples from the Blind Eagle threat actor and phishing activities focused on Tinkoff Financial institution.
PDF BMP FilesEmail files in most cases encompass company logos to deceive victims.
VirusTotal identified quite loads of mailing campaigns by leveraging these pictures, at the side of campaigns impersonating universities and companies.
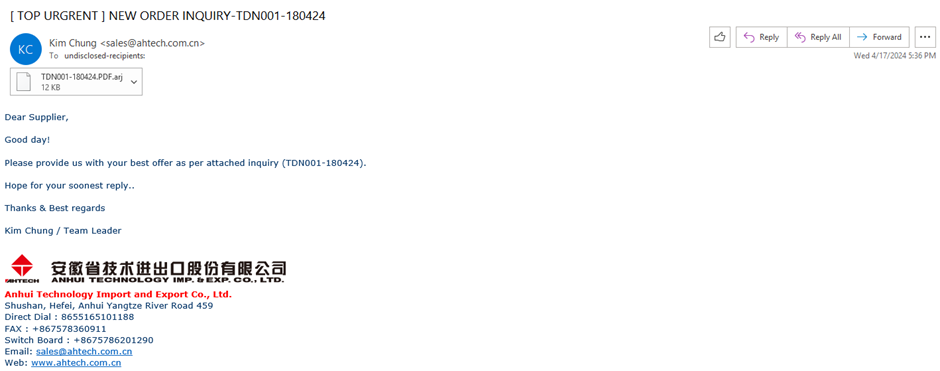
VirusTotal’s revolutionary methodology to monitoring threat actors by inspecting artifacts linked to preliminary spreading paperwork provides a treasured addition to dilapidated making an are attempting ways.
By incorporating AI and focusing on embedded files and pictures, analysts can toughen their capability to observe and name doable threats.
Source credit : cybersecuritynews.com


