What is Digital Forensics? Tools, Types, Phases & History
What is Digital Forensics? Tools, Kinds, Phases & History
A subfield of forensic science called digital forensics specializes to find, obtaining, processing, inspecting, and documenting electronically saved files.
Digital forensics abet is important for regulations enforcement investigations because digital proof is a segment of with regards to all criminal actions.
The term digital forensics became morning time to talk over with the investigation of computer forensics, nonetheless it has since attain to talk over with all gadgets that can perhaps perhaps retailer digital files.
Laptop systems, smartphones, far-off storage, unmanned aerial systems, shipborne tools, and diverse gadgets are examples of where digital proof shall be gathered.
The current forensic route of contains the seizure, forensic imaging (acquisition), and analysis of digital media.
Here’s followed by the introduction of a memoir outlining the proof that has been gathered.
Table of Contents
- What is Digital Forensics?
- History of Digital Forensics
- What are the categories of Digital Forensics?
- Challenges of a Digital Forensics Investigator
- Phases of Digital Forensics
- Main Digital Forensic Tools
- Plan of Digital Forensics
What is Digital Forensics?
In the realm of forensic science is known as “digital forensics,” enviornment cloth found on digital gadgets is recovered, investigated, examined, and analyzed, most incessantly in reference to computer and cell gadget crimes.
The incident response route of for companies contains digital forensics as a severe disclose.
Legislation enforcement can use the guidelines forensic investigators gain and memoir about a criminal incident.
There are loads of uses for digital forensics research, nonetheless essentially the most overall is to express or disprove a conception in court docket, whether for a criminal or civil case.
A computer, cell phone, server, or community are examples of digital media, and the science on the again of it’s to obtain proof there.Â
Primarily the most straight forward systems and tools are given to the forensic group to handle now not easy digital-associated cases.
It covers analytical themes admire hardware, working system, community, capabilities, and storage media.
History of Digital Forensics
| 365 days | Development |
|---|---|
| 1978 | The Florida Laptop Act |
| Eighties | Hasty enhance in Digital Forensics Subject |
| Nineteen Nineties | Adaptive Development, utilized in a form of sectors |
| 1970 & 1980 | Federal Legislation Enforcement |
| 1984 | Operation started by FBI Laptop Diagnosis and Response Crew (CART) |
| 1994 and 1995 | Accepted British digital forensic methodology developed. |
| 1998 | Right put collectively manual for Digital Evidence created within the UK by the Association of Chief Police Officers (ACPO) |
The key principles that put collectively to all digital forensics for regulations enforcement within the UK are described within the ACPO pointers.
These ideas and most efficient practices earn step by step change into requirements because the science of digital forensics has evolved, and the UK’s Forensic Science Regulator now governs the discipline.
What are the categories of Digital Forensics?
The route of of discovering, safeguarding, inspecting, and documenting digital proof is is known as “digital forensics.” It’s done in yelp that, if important, it goes to be gentle as proof in court docket.

The scientific enviornment of digital forensics is persistently growing and has many subdisciplines. Various of these sub-disciplines consist of:
Media Forensics-
- It affords with retrieving files from storage media by attempting thru birth, changed, or removed recordsdata.
Community Forensics:
- The commentary, recording, gathering, storing, and analysis of community actions or events to title the origin of security assaults, intrusions, or assorted problematic incidents, equivalent to assaults by worms, viruses, or malware, abnormal community site traffic, and security breaches.
Wi-fi Forensics:
- Wi-fi forensics’ predominant goal is to present the tools to gain and analyze the guidelines from wireless community site traffic.
Database Forensics:
- It’s a subset of digital forensics that specializes in inspecting and investigating databases and the metadata surrounding them.
Utility Forensics:
- In an investigation precise into against the law nice looking most efficient tool, the branch of digital forensics affords with the identification, gathering, analysis, and presentation of digital proof.
Email Forensics
- Specializes in improving and inspecting emails, including deleted emails, calendars, and contacts.
Reminiscence Forensics:
- It’s additionally called stay acquisition when proof is recovered from the RAM of an active computer.
Cell Phone Forensics:
- It’s a subfield of digital forensics that affords with discovering, gathering, inspecting, and presenting digital proof of against the law committed the utilization of a cell gadget (equivalent to a phone, GPS, tablet, or pc) all over an investigation.
Challenges for a Digital Forensics Investigator
This day, folks basically use social media websites and online social networks to carry many gains of their lives into our on-line world.
Sadly, when cloud computing is intelligent, gathering files to reconstruct and discover an assault can severely violate customers’ privacy and is linked to assorted challenges.
Customarily, criminals use system instructions and capabilities to conceal files chunks in invisible earn within the storage medium.
Utilizing a covert channel, an attacker can evade intrusion detection systems and veil files on a community.
It served the attacker’s cause of disguising his relationship with the compromised system.
There are no acceptable guidelines for gathering and acquiring digital proof in India.
Forensic labs and investigating businesses are growing their gain requirements. Which skill that, the value of digital proof has been diminished.
Because the crime price rises, so does the quantity of files, and the burden on a digital forensic expert to analyze such broad portions of files rises as effectively, because digital proof is extra sensitive than bodily proof and can without disaster vanish.
The emergence of Platform as a Carrier (PaaS) and Utility as a Carrier (SaaS), which earn precipitated a assortment of changes to the computing structure, is the pause consequence of recent technological advancements and changes in gathering forensic proof.
There are several challenges associated to the utilization of novel tool and know-how.
More than one sources presenting conflicting timestamp interpretations, time zone references, and clock skew/drifts manufacture a unified time-lining effort.
To synchronize timelines from assorted files sources, sophisticated analytical tools are wished.
Phases of Digital Forensics
Theft or disclosure of files, misuse of the accumulate, hacking of networks or systems, espionage, and financial fraud are upright about a of the wrongdoings that can perhaps perhaps be found and proven thru a digital forensic investigation.
To be trail the accuracy of the guidelines and its admissibility in court docket, it’s far important to behavior a structured and map-driven digital forensics investigation in both civil and criminal cases.Â
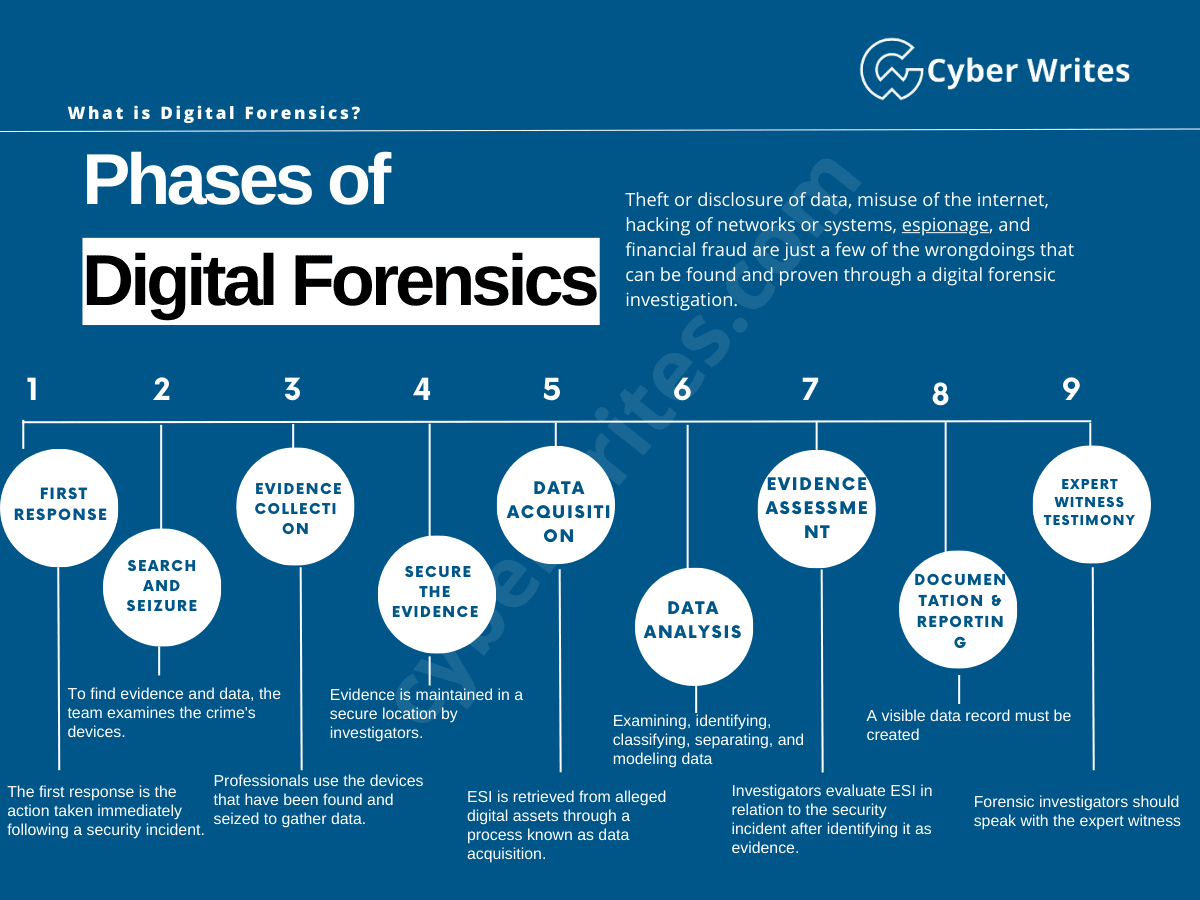
These are one of the most most same outdated phases of a digital forensics investigation:
Piece 1 – First Response
- The first response is the action taken straight following a security incident. The form of incident will earn a tall impact on it.
Piece 2 – Search and Seizure
- To search out proof and files, the group examines the crime’s gadgets. Investigators rob the tools to make certain the offenders can’t commit further crimes.
Piece 3 – Evidence Series
- Mavens use the gadgets which had been found and seized to gain files. They use forensic procedures for dealing with proof that is clearly outlined.
Piece 4 – Procure the Evidence
- Evidence is maintained in a stable put by investigators. Recordsdata shall be verified to be accessible, correct, and authenticated in a stable environment.
Piece 5 – Recordsdata Acquisition
- Electronically Stored Recordsdata (ESI) is retrieved from alleged digital property thru a route of is known as files acquisition.
- Finding out extra about the incident is helpful, nonetheless if the system is flawed, the guidelines may perchance perhaps even very effectively be changed, compromising the validity of the proof.
Piece 6 – Recordsdata Diagnosis
- Examining, figuring out, classifying, isolating, and modeling files are all steps on this segment that turn it from raw files into usable files.
Piece 7 – Evidence Review
- Investigators maintain in tips ESI in terms of the safety incident after figuring out it as proof.
- This stage specializes in straight connecting the guidelines gathered to the case.
Piece 8 – Documentation and Reporting
- In this route of, a seen files memoir needs to be created. It helps in recreating the crime scene and reviewing it.
- It contains proper crime scene documentation, photographing, sketching, and crime-scene mapping.
Piece 9 – Expert Query Testimony
- Forensic investigators ought to talk with the expert watch to verify the proof’s accuracy.
- A legit who looks precise into against the law to obtain proof is known as an expert watch.
Main Digital Forensics Tools
It’s that you would also deem of to protect, title, extract, and doc digital proof to be gentle as proof in court docket.
Many tools are on hand to you to make it more uncomplicated to simplify and ease this route of, including:
The Sleuth KitÂ
- With the again of the Sleuth Equipment, you can gaze disk photography and extract recordsdata from them the utilization of a location of portray-line tools and a C library.Â
- In Put up-mortem and loads of alternative birth-provide and for-profit forensics tools it’s gentle within the background.
FTK Imager
- FTK Imager is a forensic toolkit created by Discover admission to Recordsdata that shall be gentle to gain proof. Without altering the fashioned proof, it goes to attach copies of files.Â
- This tool can clear out unnecessary files by specifying criteria admire file dimension, pixel dimension, and files sort.
XplicoÂ
- Xplico’s goal is to extract the capabilities’ files from online page traffic and seize it.
- Let’s advise, Xplico extracts every email (POP, IMAP, and SMTP protocols), every HTTP page, every VoIP call (SIP), every FTP file, every TFTP file, and further from a pcap file. Â
Community Forensic Diagnosis Utility (NFAT) Xplico is an birth-provide alternative to community protocol analyzers.
Paladin
- A assortment of forensic tasks shall be made extra effective the utilization of the Ubuntu-basically based entirely mostly tool PALADIN.
- Bigger than 100 purposeful tools are on hand on this digital forensics tool to gaze malicious boom material.Â
- Utilizing this tool, you would also effectively and like a flash simplify your forensic task.
Prodiscover Forensic
- You can obtain every files on a computer disk the utilization of ProDiscover Forensic, a computer security program.Â
- It ought to be gentle in upright complaints to safeguard proof and manufacture excessive-quality reports.
- This tool can extract EXIF (Exchangeable Image File Format) files from JPEG recordsdata.
Objectives of Digital Forensics
It’s helpful for the investigation company to make use of the computers and associated supplies as proof in court docket to enhance, analyze, and protect them.
Retort to an incident to extinguish further lack of property, cash, and a particular person’s title all over an assault.
Acknowledge and overcome the tactics and strategies gentle by attackers to steer particular of prosecution.
Creating protocols at a suspected crime scene that make it more uncomplicated to make certain the digital proof you attach is now not tampered with.
Knowledge of the licensed pointers of loads of regions and areas, equivalent to digital crimes, is frequent and much-reaching.
Assembling a computer forensic memoir that comprises thorough important gains on the investigation.
The targets of the analysis segment within the digital forensics route of fluctuate reckoning on the cases of every and each case.
It ought to additionally be gentle to ogle into files security incidents within the neighborhood on the system or over a community and to abet or disprove assumptions made about particular folks or organizations.
In a criminal or civil court docket, digital forensics is most most incessantly gentle to express or disprove a conception.
By merely copying your proof pressure, acquiring files lets you behavior an investigation the utilization of the reproduction of the proof pressure other than the fashioned.
Source credit : cybersecuritynews.com






