What is Email Spoofing? – Email Threat Prevention Checklist 2024
What’s E-mail Spoofing? – E-mail Threat Prevention Checklist 2024
A fraudulent manner weak by malicious other folks to send emails with fictitious sender files is email spoofing.
The attacker creates the affect that the email is coming from a decent provide, equivalent to a decent industry or particular person, by changing the email’s header files, especially the “From” field.
By convincing recipients that the email is authentic, this tactic hopes to acquire users to give deepest files, topple for phishing scams, or unintentionally download malware.
E-mail spoofing specializes in taking wait on of the built-in flaws in the email protocol in favor to hacking the sender’s email legend.
It can perhaps well be most well-known to be responsive to extraordinary emails, thoroughly take a look at sender addresses, chorus from clicking on suspicious hyperlinks or attachments, and build email authentication mechanisms into place in scream to guard in opposition to email spoofing.
E-mail Spoofing Statistics
- Growing Prevalence: For quite loads of years, email spoofing has been a odd plan for hackers. Due of its success in misleading recipients and getting over aged email safety measures, it is aloof a most current plan.
- Phishing Attacks: E-mail spoofing is normally linked to phishing attempts, wherein attackers strive to convince victims to give a proof for deepest files like passwords, financial files, or deepest files. Hundreds and thousands of phishing emails are sent out on every day foundation, making phishing attacks an ongoing excessive effort.
- Centered Industries: Campaigns the employ of email spoofing customarily arrangement a vary of sectors, alongside with financial establishments, healthcare companies, governmental entities, and e-commerce web pages. Distinct industries are chosen by cybercriminals as elegant targets because they take care of sensitive files or have a huge particular person irascible.
- Financial Affect: For every other folks and corporations, email spoofing can lead to most well-known financial losses. Agencies at some point of the enviornment have lost billions of bucks due to the Industry E-mail Compromise (BEC) frauds, which usually employ email spoofing. These frauds normally prey on workers in ticket of financial operations and deceive them into sending money that’s not theirs.
- Impersonation Tactics: Making an strive to govern respected entities, like eminent brands, provider companies, or coworkers within an enterprise, is a odd plan weak in email spoofing. Attackers construct their communications with care and continuously employ social engineering options to win over their arrangement’s belief.
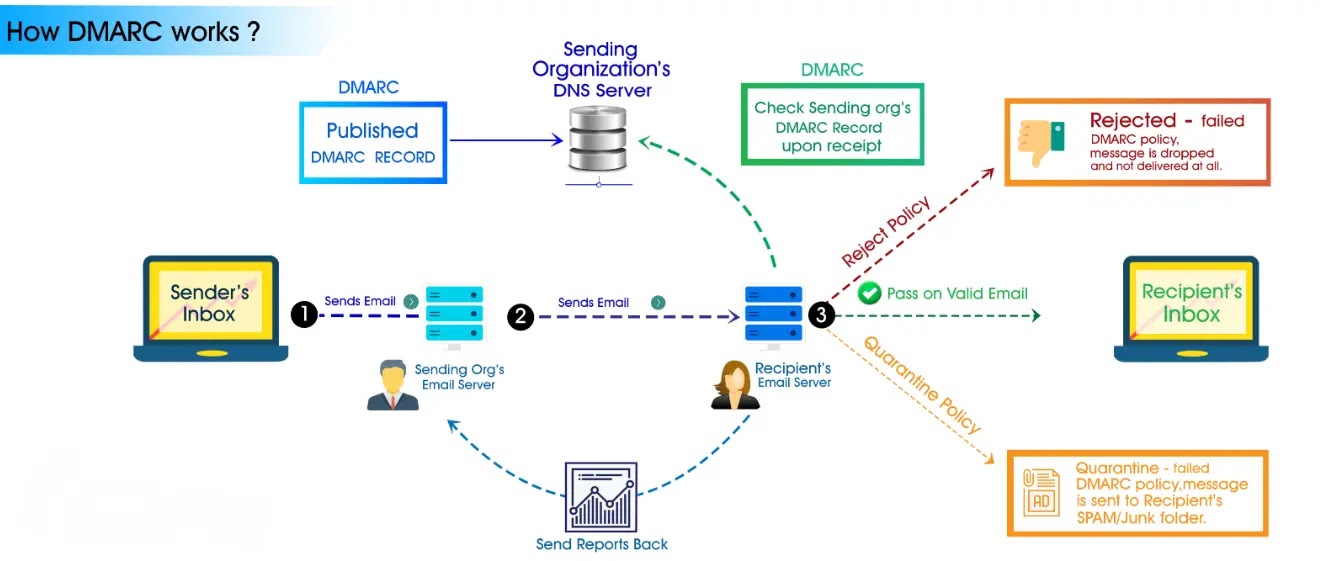
- Mitigation Measures: Organizations and other folks have deployed a resolution of email authentication programs, alongside with SPF (Sender Coverage Framework), DKIM (DomainKeys Known Mail), and DMARC, to forestall email spoofing (Domain-basically basically based Message Authentication, Reporting, and Conformance). These procedures work to make certain that the legitimacy of emails and wait on quit spoofing from getting by strategy of to recipients’ inboxes.
Examples of E-mail Spoofing
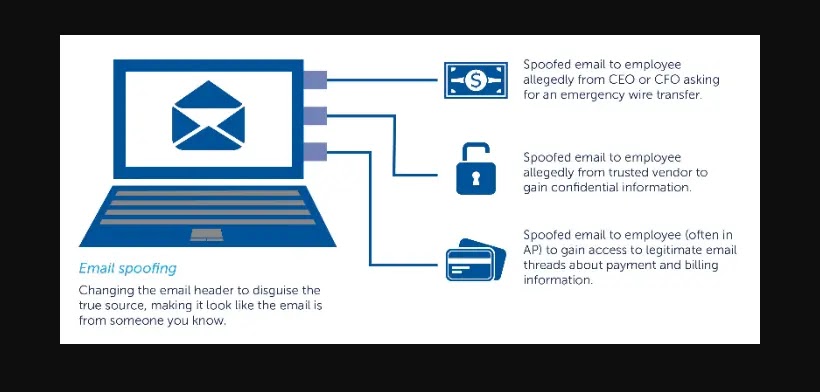
Listed here are about a examples of extraordinary email spoofing scenarios:
- Pretend CEO or Executive Emails: Attackers also can merely send emails to crew members, shoppers, or industry companions while posing as senior leaders within a company. These fraudulent emails customarily demand urgent acts, equivalent to money transfers, the unveiling of deepest files, or the starting of unlawful transactions.
- Keep Impersonation: Spoof emails are weak by cybercriminals to replicate eminent corporations or effectively-most current web companies. So as to deceive other folks into disclosing sensitive files, these emails also can merely utter recipients of a safety breach, legend suspension, or an urgent seek files from for deepest files.
- Financial Institution Scams: In phishing attempts, cast emails that appear to be from banks or other financial organizations are continuously employed. The emails can point to that the recipient’s legend has been compromised or that they must validate their login facts by clicking on a unhealthy link and entering deepest files.
- Authorities Agency or Tax Authority Impersonation: Attackers also can merely send spoof emails to other folks or corporations while posing as tax authorities or authorities entities. In scream to amass sensitive financial or deepest files, these emails customarily embody threats of magnificent motion, tax fines, or demands for quick cost.
- Password Reset or Story Verification Requests: The aim of spoof emails is to trick shoppers into changing their passwords or verifying their accounts by making them appear to be from respected web companies, social media sites, or email companies. On the total, these emails salvage horrible hyperlinks that snatch guests to phony web pages supposed to rob login files.
- Phony Job Offers: Job searchers can be the arrangement of spoof emails that advertise tempting occupation prospects. Emails that seek files from deepest files, bank legend files, or money for background tests or processing prices also can merely appear to be from honest corporations.
Organizations must adopt efficient incident response plans, on a frequent foundation be conscious email online page online traffic for anomalies, and halt updated on emerging threats to halt sooner than the evolving email possibility landscape with AI-powered alternatives like Trustifi.
What desires to be Averted in E-mail Spoofing
- Feeble E-mail Protocols: With out solid authentication measures, email protocols like Easy Mail Transmission Protocol (SMTP) were created, making it more straightforward for attackers to change the “From” field and send emails with faked sender addresses.
- Lack of E-mail Authentication: Sturdy email authentication tactics like SPF (Sender Coverage Framework), DKIM (DomainKeys Known Mail), and DMARC must not continually weak by email servers and shoppers (Domain-basically basically based Message Authentication, Reporting, and Conformance). These procedures reduce the likelihood of email spoofing and wait on in confirming the legitimacy of the sender’s enviornment.
- Phishing and Social Engineering: Attackers customarily employ social engineering tactics to lie to victims into giving up deepest files or taking certain actions. They convince other folks to imagine the fraudulent emails and attain the supposed acts by assuming the identities of respected corporations and the employ of psychological manipulation.
- Malware and Botnets: Immense-scale email spoofing attacks will possible be applied via malicious machine and botnets. It’d be considerable to identify the provide of assaults when a botnet’s compromised computer programs are utilized to send out nice portions of faked emails.
- Birth Relay Servers: Attackers also can merely employ email servers which have been improperly configured or insecurely secured as commence relay servers. These servers allow email spoofing attacks by allowing unauthorized users to send emails with out the basically the major authentication.
- Domain Title Machine (DNS) Vulnerabilities: Attackers also can merely adjust a online page’s DNS records by taking wait on of DNS-connected flaws or configuration errors. They’ll send faked emails from domains that appear legitimate by changing the DNS settings, which enables them to redirect email online page online traffic.
- Lack of Particular person Awareness: Of us are more prone to topple for phishing scams if they are ignorant of email spoofing tactics and most attention-grabbing practices. Attackers count on receivers not thoroughly examining email files and believing the obvious sender with out checking its legitimacy.
Systems to Name Spoofing E-mail
Figuring out spoofed emails will possible be though-provoking as attackers employ rather about a tactics to build them appear authentic. Nevertheless, there are some options you would employ to wait on identify ability spoofing attempts.
Listed here are about a tips:
- Take a look at the Sender’s E-mail Address: Survey intently at the email take care of of the sender. The enviornment title or sender’s title in spoof emails customarily has subtle adaptations or misspellings that will drag skipped over before all the issues explore. It’d be compared with the authentic email addresses you have gotten on file.
- Review E-mail Headers: The starting place of an email is fully disclosed in the email headers. You might perhaps perhaps perhaps also scrutinize irregularities in the email headers, equivalent to mismatched enviornment names or IP addresses that don’t correspond with the claimed sender.
- Analyze the E-mail Screech: Rob terminate attention to the email’s usage of phrases, grammar, and tone. Spelling errors, heart-broken grammar, or an urgent and aggressive tone all be indicators of a spoof email. Educated dialog requirements are normally upheld by authentic organizations.
- Flit Over Hyperlinks: Invent not right this moment on any of the email’s hyperlinks. To seem the underlying URL, merely movement your mouse cursor over the link. Take a look at to gaze if the link hyperlinks to the genuine space or if it takes you to a suspicious or unrelated online page. Be wary of URLs which might well be shortened or have extraordinary enviornment names.
- Survey for Irregular Requests or Urgency: Emails which have been cast customarily query recipients for deepest files, money, or immediate motion. Be cautious of emails that query for deepest files that the sender must have already purchased, demand urgent responses, or build threats in opposition to you when you don’t comply.
- Imperfect-Reference with Known Contacts: Earlier than appearing on an email that appears to be from any individual , mediate about entering into touch with them via a separate channel of contact to substantiate the email’s validity.
- Enable E-mail Authentication: Review that SPF, DKIM, and DMARC email authentication requirements have been applied by your email supplier or company. These tactics can wait on in figuring out and removing cast emails.
- Exercise Anti-Unsolicited mail and Anti-Phishing Instrument: Set off and take care of your email consumer’s spam and phishing filters updated. The likelihood of falling for spoofing attempts will possible be decreased by the employ of these filters to seem and warn in opposition to questionable emails.
- Have confidence Your Instinct: Have confidence your instinct if anything appears extraordinary or too upright to be loyal. When unsure, err on the aspect of warning and steer clear of responding to emails unless their legitimacy has been confirmed.
Motivations Within the encourage of E-mail Spoofing
The motivations in the encourage of email spoofing can vary depending on the desires and intentions of the attacker. Listed here are some odd motivations observed in the encourage of email spoofing:
- Phishing and Id Theft: Spoofing emails is a odd component of phishing campaigns. Attackers send spoof emails to recipients as a ability to acquire them to give sensitive files equivalent to passwords, credit ranking card numbers, or deepest files. The exploitation of this files for financial fraud, identification theft, or other unlawful crimes is then ability.
- Financial Fraud: Spoof emails will possible be sent to trick recipients into offering banking files or taking part in financial transactions. Attackers also can merely mediate the identification of a company leader, a financial institution, or a industry partner in scream to convince victims to switch money to fraudulent accounts.
- Malware Distribution: Malicious attachments or viruses will possible be allotted by strategy of email spoofing. Attackers trick recipients into opening phishing emails that embody malicious recordsdata, equivalent to paperwork with macros or executable functions. When these attachments are opened, malware will possible be build in on the recipient’s machine, giving attackers acquire entry to or take care of watch over with out authorization.
- Social Engineering and Impersonation: Attackers can pose as other folks or honest entities, equivalent to coworkers, mates, or superiors, the employ of email spoofing. They’ll persuade recipients into conducting certain acts or disclosing deepest files by taking wait on of belief and authority, customarily for financial build or other malicious ends.
- Recognition Damage: Spoofing emails will possible be weak to misery any individual’s or a company’s status. Attackers also can merely send horrible or offensive emails from spoof addresses with the arrangement of harming the arrangement’s status.
- Disruption and Sabotage: E-mail spoofing also can merely also be weak as a sabotage or disruption plan. With the aim of making confusion, miscommunication, or turmoil within a company or community, attackers also can merely send fraudulent emails with mistaken files or misleading instructions.
Easiest Practices and Systems to Steer certain of E-mail Spoofing
- Enable E-mail Authentication: SPF (Sender Coverage Framework), DKIM (DomainKeys Known Mail), and DMARC must be weak as email authentication programs (Domain-basically basically based Message Authentication, Reporting, and Conformance). These measures reduce the ability for getting faked messages and wait on in confirming the legitimacy of incoming emails.
- Review Sender Recordsdata: Take a look at the hide title and email take care of of the sender. Survey out for small adjustments, misspellings, or domains that aren’t the sender’s genuine enviornment. If unsure, talk about over with known contacts or acquire in touch via a particular dialog channel to substantiate the sender’s identification.
- Be Cautious of Sudden Emails: Must you acquire unexpected or unwanted emails, be wary, especially if they query for deepest files, money, or immediate motion. Be wary of emails purporting to be from respected corporations, financial establishments, or governmental bodies because attackers customarily spoof these organizations.
- Don’t Click on on Suspicious Hyperlinks or Attachments: When opening hyperlinks or downloading recordsdata from emails that appear suspicious or are sent by unknown sources, employ warning. Must you flit your pointer over hyperlinks, scrutinize any recurring enviornment names or errors in the underlying URL.
- Be Vigilant with Deepest Recordsdata: When sending deepest files over email, employ warning. Sensitive files just is not very requested by email by honest organizations. Passwords, Social Security numbers, credit ranking card files, and other sensitive files must never be shared with out first confirming the email’s legitimacy.
- Educate and Practice Staff: Agencies must on a frequent foundation scream crew members and educate them about email safety, alongside with email phishing dangers and the technique to space fraudulent emails. The IT department must be notified of any phishing attacks or suspicious emails which might well be thought to have been sent.
- Put in power Anti-Unsolicited mail and Anti-Phishing Filters:Exercise spam filters and email safety instruments that will perhaps perhaps wait on in figuring out and removing phishing or horrible communications. Earlier than they reach your inbox, these applied sciences can wait on in blocking or quarantining suspicious messages.
- Keep Instrument and Programs Updated:Make certain that your working system, antivirus program, and email consumer are all updated. Patching safety flaws and defending in opposition to known exploits weak in email spoofing attacks are made ability by frequent upgrades.
- Exercise Caution on Public Wi-Fi Networks: Be conscious that public Wi-Fi networks is possible to be insecure and prone to man-in-the-heart attacks while the employ of them to acquire entry to your email. When the employ of public Wi-Fi, steer clear of gaining access to deepest emails or signing into accounts that have financial or deepest files.
Source credit : cybersecuritynews.com






