What is ICMP Protocol ? – How Does ICMP Works – Guide
ICMP protocol is mainly feeble for error facing and primarily feeble for network gadgets (routers). Many various kinds of errors exist within the network layer that time ICMP can utilize to debug these errors. ICMP’s elephantine rating is Recordsdata superhighway Delight in watch over Message Protocol, one network layer protocol form.
This form of IP protocol has no error-correcting or error-reporting mechanism to utilize the message to bring the recordsdata. If someone sends the message, that will get stolen from the sender to the destination. If any likelihood there’s no error, then the sender has to attain that message has reached to the destination.
If someone is between, the sender will rating the error message and have to resend the message as quickly as that you would contemplate of.

Classes of ICMP protocol Message:
These ICMP protocol messages are divided into two kinds.
- Error-reporting messages: In this router would possibly perhaps presumably perhaps hang stumble upon a philosophize when it will get processed the IP packet; the actual person will rating a message.
- Question messages: Here is one form of message which helps the host to rating recordsdata of one other host. Whenever you hang got a consumer and a server, clients desire to clutch whether or now now not the server is going for dwell or now now not. That time it sends the ICMP message so that it would possibly perhaps presumably perhaps rating the affirmation.
Variety of Error Reporting messages:
The error-reporting messages are labeled into four lessons. Those are under:
- Toddle sing unreachable: When the packet recordsdata would now not reach the destination for the time being, itâs referred to as destination unreachable. If the sender sends a message, this would possibly perhaps presumably well now now not reach the destination that time the intermediate router will file.
- Source Quench: In this, there’s no waft of control mechanism that works; whereas sending the packet to ship, kill now now not contemplate whether or now now not the receiver is ready to receive these packets or now now not. In this case, ICMP provides the feedback. Most incessantly sender sends the packet in a increased rate which the router will now not take care of and manufacture this misfortune true supply quench bring the sender to ship the packet in a lower trace.
- Time exceeded: Most incessantly the misfortune turns into cherish this in that many routers are between sender and receiver. The sender in general sends the packet then it will get to switch to the routing loop. Time will rating exceeded reckoning on the time-to-dwell cost. The associated price will decrease as quickly because the packet traverses during the router that time. When the router will get discarded, that time will rating exceeded when in contrast with the contemporary one.
- Parameter philosophize: Typically, the destination host desires to ship the parameter philosophize message when the parameters are now now not situation effectively.
- Redirection: As quickly as packet will get sent the routing table will get up up to now and the actual person will get the redirection message.
What for ICMP to rating feeble?
Whenever you will need to have to win the reporting error, then ICMP is the finest one. Each and each time two gadgets are connected during the web, ICMP can plan the error from the receiving tool to sending tool so that recordsdata have to never near as expected.
One more utilize of ICMP protocol is to abet dragonise the instrument into assets for the networkâs performance. Traceroute and ping rating feeble for the ICMP, and messages are sent for the recordsdata and efficiently transmitted. It has traceroute utilize the set the tool receives its packet recordsdata and went through with the destination to repeat the file. This also entails the bodily route that can also merely take care of the recordsdata.
This traceroute can also also expose you how great time it took recordsdata to switch from one tool to 1 other and the arrangement in which great time it required to reach to 1 other router. This outing is in general customarily known as a hop. This recordsdata is de facto revealed by the traceroute that would possibly perhaps resolve out the upright tool, that can also merely trigger delays.
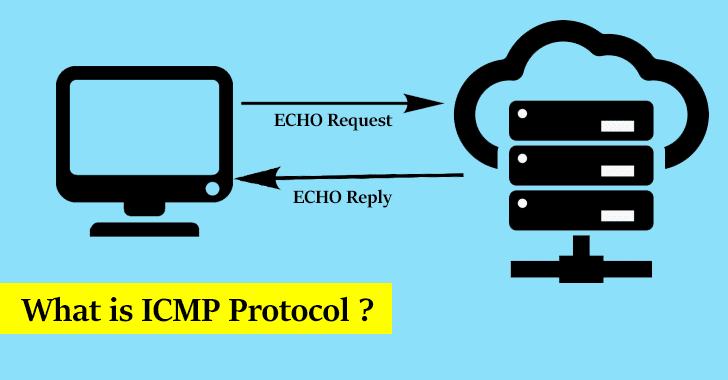
This ping is analogous to the traceroute, and it’s vital. This file reveals that how the recordsdata plod between two aspects. Here is incessantly facilitates the ping the set ICMP does the echo establish apart a query to and acknowledge, which does the ping project.
ICMP has huge utilize for network performance. Here is also to rating feeble for the ICMP flood and Smurf attack. The demise attack ping will crush the tool, that can also merely discontinuance the now not original functionality.
What all are the ICMP message code?
ICMPâs predominant motto is to supply the recordsdata and the feedback connected to the error. It also helps to manipulate messages and arrange queries. The first code will get a field into the ICMP block, that can also merely rating mange with out bother. It also conveys a huge deal concerning recordsdata. You would possibly perhaps presumably perhaps be ready to fetch the few connected values, that are described under:
- Eco Retort: Itâs mainly got feeble for ping.
- Toddle sing: In this destination is unreachable.
- Source quench: This skill demonstrate that the router is overloaded.
- Redirect: It system itâs donate to 1 other router.
- Echo Demand: It is analogous to 0, and it will get feeble for ping.
- Router solicitation: Here router will rating solicited.
- Traceroute: Here, after time will rating exceed, it rating feeble for traceroute.
How does the ICMP protocol work?
ICMP is one other rating of Recordsdata superhighway Protocol (IP); the model is six and IPv6 is now now not connected to the TCP (Transmission Delight in watch over Protocol). There will not be this form of thing as a tool out there to that can also merely rating connected to one other ICMP message.
TCP has two gadgets that rating talking first have interaction, and it takes several steps. After this handshake will get total, recordsdata will rating transferred to the receiver from the sender. This recordsdata will rating observed by utilizing this tcpdump instrument.
ICMP is barely various, and in that connection did now now not rating formed. The message is in general sent the set TCP and UDP are included. The recordsdata got sent, and it’s dedicated to the port. ICMP message will get directed to the port, and the tool will receive it.
ICMP protocol in DDoS assaults:
When customers distribute the DDos, attackers in general crush the target with the undesirable target. This target would now not present the provider, and it has multiple ways the set attackers uses the ICMP protocol and kill the attack. Here few ways are described under:
- Ping of demise: The attacker will ship the IP packet that has to be greater than the need of bytes allowed by IP. It has an supposed destination, which makes the oversize fragmented packet. When the recipient tool reassembles, the measurement exceeds the restrict, that can also merely trigger a buffer overflow. The more moderen tool does the feeble attack, nonetheless legacy networking is susceptible.
- ICMP flood attack: Here is also properly-identified as a ping flood attack. This attack plan is to crush the target tool so that it would possibly perhaps presumably perhaps kill echo-establish apart a query to packets. Every echo-establish apart a query to packet have to rating processed by the target. They also will acknowledge through an echo acknowledge message. This will get in general sucks up with the focused computerâs resource which is a motive within the back of the denial provider, and it has other customers of the target computer.
- Smurf attack: This attacker has to ship an ICMP packet with IP address and network layer equipment. Users can also also ship the packets to the spoofed address. As a ping of demise, the Smurf attack works because the undefended legacy equipment.
Ideal Solutions
ICMP works for the protection, and this would possibly perhaps presumably well also also preserve your network win so that ICMP have to never rating misuse. Here you are going to rating each form of data about ICMP protocol. We hope this article will let you by offering you the upright recordsdata.
You would possibly perhaps presumably perhaps be ready to utilize us on Linkedin, Twitter, Facebook for each day Cybersecurity and hacking news updates.
Moreover Read
What’s WarXing in Cyber Security? What are the Advantages?
What Is SOAR and How It Works? Aspects and Advantages
What’s OAuth 2.0 ? How it Works ? A Detailed Explanation of Authorization Framework
Source credit : cybersecuritynews.com