What is Linux Firewall? How to Enable Packet Filtering With Open Source Iptables Firewall?
What is Linux Firewall? Discover how to Allow Packet Filtering With Commence Offer Iptables Firewall?
One in all the ideally suited security instruments for Linux is the firewall, which controls incoming and outgoing community traffic in step with established security insurance policies and prevents unauthorized customers from accessing the machine.
One popular open-offer firewall software for Linux is iptables, which lets customers situation up community traffic rules and give an explanation for packet filtering. One must set rules that govern the therapy of varied packet kinds to enable packet filtering the usage of iptables.
A default protection for chain traffic will seemingly be specified, rules might perchance also be added to allow or announce specific kinds of verbal replace, and these settings might perchance also be saved to verify that that they are retained even after reboots.
You wish know the syntax of iptables and the protocols that it controls to get basically the most of it effectively.
Table of Contents
What is a Linux Firewall?
What is Iptables? How does it work?
How Does Packet Filtering Work with Iptables?
Tables Overview
Blocking off Attacks with IPtables:
Different Straightforward rules to Are trying
What is a Linux Firewall?
A Linux firewall is a instrument that inspects Community traffic ( Inbound /Outbound connections ) and decides to lope or filter out the traffic. Iptables is a CLI software for managing firewall rules on a Linux machine.
Community Safety evolved with diversified kinds of Linux firewalls in the abilities. Fashioned packet-filtering firewalls deal with Routing and filtering packets ( OSI Layers 3 and 4 ), Where else NGFWs will work with extra capabilities as with OSI layers ( L4-L7 of OSI model ).
What is Iptables? How does it work?
Iptables is a CLI ( Command-line interface ) utility that permits the administrator to configure specific rules that will build in power the Linux kernel ( Netfilter framework) to act akin to glance, alter, or tumble community packets. Enabling these Iptables in any Linux machine or instrument will seemingly be acting as a Community Firewall and/or a router.
Different kernel modules and applications are veteran for diversified protocols; IPtables discover to IPv4, IP6tables to IPv6, ARP tables to ARP, and ebtables to Ethernet frames.
Later Netfilter Mission developed Nftables for performance and scalability. This is a packet filtering framework that does the same work as Iptables.
How Does Packet Filtering Work with Iptables?
An iptables protection is constructed with an ordered situation of rules, which portray to the kernel the actions that need to be taken against certain kinds of packets.
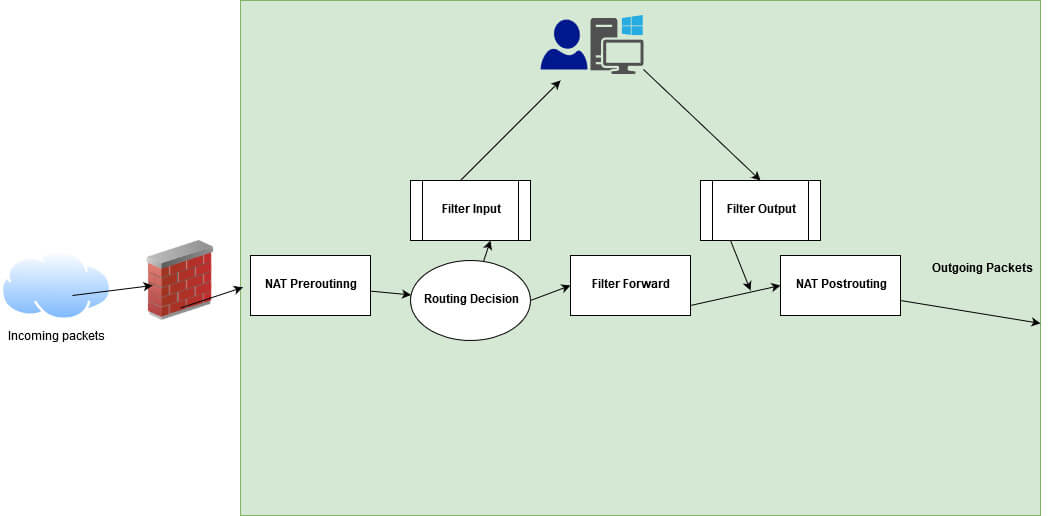
Tables Overview
Iptables functionality is classed into Four tables which will seemingly be NAT desk, packet filtering desk, Mangle desk, and Raw desk.
NAT Table:
- Community Contend with Translation ( NAT ) is processed for incoming packets and outgoing packets with routing choices in the desk.
- Community Routing is processed with Pre-routing and Post-routing of packets from origination to high-tail space.
Packet Filtering Table:
Packet filtering is processed with the below chain rules.
Chains:
- Chains are labeled into 3 kinds INPUT CHAIN, OUTPUT CHAIN & FORWARD CHAIN.
- Enter Chain â Incoming connections that are traversed from Prerouting. Instance: External IP attempting to set an SSH connection in your machine.
- Output Chain- Packets that are handed or outgoing connections from your machine. Instance: If youâre attempting to lope to cybersecuritynews.com, user traffic is verified in the chain rule to allow or announce the connection.
- Forward Chain â Forwarding connections to specific networks or ports.Instance: Port Forwarding.
Mangle desk
- The mangle desk might perchance also be veteran for particular-reason processing of packets.
- It involves a mix of NAT Tables & Chains.
Raw desk
- Raw tables are veteran easiest for packets processed with particular prerequisites, akin to exemption from connection monitoring.
Matches:
Every iptables rule has a situation of suits that tells the iptables what to get with a packet.
âoffer (-s) offer IP tackle or community
âhigh-tail space (-d) Destination IP tackle or community
âprotocol (-p) IP price
âin-interface (-i) Enter interface (e.g., eth0)
âout-interface (-o) Output interface
ârelate connection states
âstring sequence of utility layer records bytes
Target:
ACCEPT â Lets in a packet.( Settle for the incoming/outgoing connection )
DROP – Drops a packet. ( Drop the connections )
LOG â Logs a packet to Syslog.( Log the connection place for community monitoring, TCP Constructed/teardown )
REJECT – Drops a packet sends a appropriate response packet (TCP Reset or an ICMP Port Unreachable message).
RETURN- Continues processing a packet all over the calling chain.
Blocking off Attacks with IPtables:
- Let’s write a straightforward rule to block & allow ICMP probs.


- Yes, it labored. It has blocked all incoming packets with the protocol as ICMP in the community. Now letâs allow the ICMP probs to enter the community.

- You can perchance presumably also additionally write any customized rule in step with your ambiance, Reminiscent of ALLOW traffic over port 1443 or any, protocol, and Log those connection logs with -L parameter.
NOTE: In case you is seemingly to be a Pentester /Purple crew guy, Iptables Linux firewall can cloak some systems in the community as ICMP probs are blocked. But this machine might perchance also be enumerated and identified in-community with crafted ARP packets. Smooth, as a Defense guy, they’ll exhaust Arp-tables to discontinue you. This is a fully HIDE and Search GAME eternally.
Different Straightforward Principles to Are trying :
Application Layer Defense:
- This can log the connections when any Web purchasers are attempting to entry a Web server shadow file route.
iptables -I FORWARD 1 -p tcp âdport 80 -m relate ârelate ESTABLISHED -m string âstring â/etc/shadowâ âalgo bm -j LOG âlog-prefix âETC SHADOWâ
Malformed Packets Transport Layer:
- This can DROP and teardown the TCP connections because it is some distance malformed.
iptables -A INPUT -p tcp âtcp-flags ALL NONE -j DROP
Blocking off Outbound Emails:
- Block all SMTP outbound connections in the community.
iptables -A OUTPUT -p tcp âdport 25 -j REJECT
Commence Offer Linux firewalls might perchance also be veteran for minute-scale firms, VPS hosted on third-celebration clouds, and further. Enterprise firewalls also play a identical construct of methodology. But it’s factual to resolve the lawful Firewalls ( Proprietary/OpenSource ) in step with your enterprise needs.
Cosy Packet Shedding!
Furthermore Read: What is the Different Between VPN and Proxy â A Total Handbook
Source credit : cybersecuritynews.com




-1.webp)