What is .NET Malware Obfuscators? – Develop & Dismantle a Simple Obfuscator
What is .NET Malware Obfuscators? – Make & Dismantle a Straight forward Obfuscator
The .NET malware obfuscators are instruments venerable to obfuscate the source code of .NET strategies, making it worrying for reverse engineers to treasure and analyze the code.Â
They rename variables, alter code structures, and add deceptive instructions to veil detection and analysis by enhancing the malware’s strength in opposition to security measures.
It’s rare to win neat malware, as they’re veritably altered to discontinuance analysis with obfuscators. Some mutate machine code (C/Asm/Rust), while others modify .NET IL code.
In conserving with ANY.RUN Technical write-up Fragment 1, to treasure obfuscators, we must mediate be pleased their creators. To defend correctly, you choose to label the offensive, be pleased the crimson/blue workers in cybersecurity.
ANY.RUN is a developer of a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams, to boot as Possibility Intelligence Feeds and Possibility Intelligence Search for. On each day foundation, 300,000 experts exercise our platform to compare incidents and streamline risk analysis.  Â
Technical Diagnosis
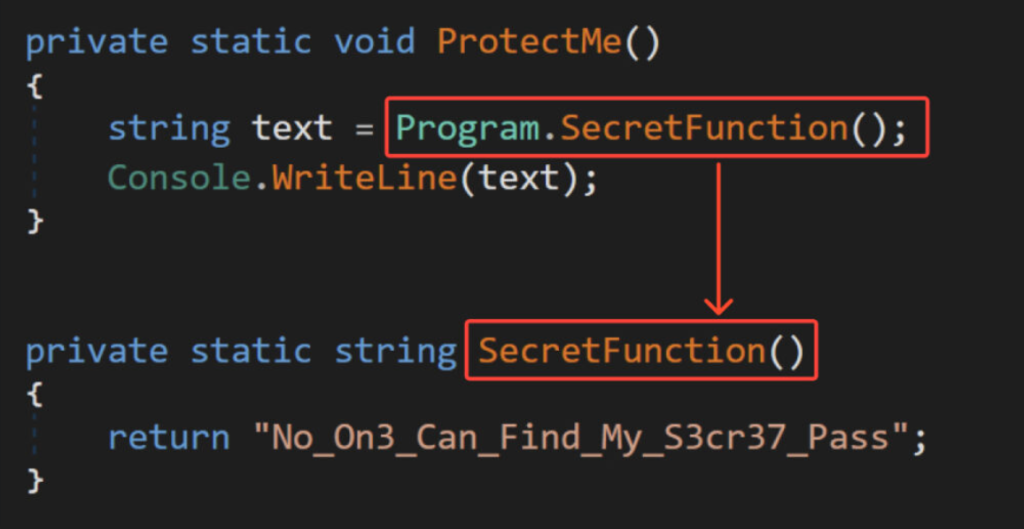
ANY.RUN researchers built a easy obfuscator by which the one characteristic below the image, “ProtectMe,” which outputs “No_On3_Can_Find_My_S3cr37_Pass,” comprises about a traces of code and one variable.
Within the .NET debugger “DnSpy” the decompiled code appears to be like be pleased the next:
Opening the built-in tool within the connected tool presentations that anybody can also simply quick and readily ogle the password.
To give protection to the password. following strategies are instructed:
- proxy strategies
- persona breakdown
- numeric conversion
- heavy math
- CFG obfuscation
The proxy strategies place every static string in its maintain characteristic with an absurd title that presents larger care for watch over over these particular particular person strategies.
Researchers informed that the IL code must be modified to maintain the goal. Then, on the compiled “Supply code,” the lawful analysis and implementation are required the exercise of the “Dnlib” library.
Loads of steps are desired to be adopted to full this course of, and here now we relish mentioned them:
- Detect characteristic âProtectMeâ.
- Fight thru your total instructions and win every event of âldstrâ (load string).
- Manufacture a unique class and a unique characteristic with a random title.
- Add âldstrâ and âretâ instructions to the body of the created characteristic.
- Replace the unique âldstrâ with a call to the unique characteristic.Â
Researchers obscured the unique string, nonetheless it absolutely stays without complications discoverable. The cybersecurity analysts fragmented the secret into characters to present a boost to security by enabling later shuffling for a extra worrying code presentation.
Changing the symbols with numerical representations within the source and decompiled code obscures characters successfully.
Using the “Conv.U2” instruction, every persona is converted to an unsigned int, reverted to a string, and appended to the .Â
Researchers tweaked their obfuscator, the place the “MaskCharsWithNumVal” characteristic facilitates this conversion.
IlSpy is some other effective IL code analysis tool that adeptly reverts numerical representations to characters, rendering them readable.Â
Besides this, inspecting the file’s binary ogle finds the scattered presence of the researchers’ secret.
Strive ANY.RUN Yourself with a 14-day Free Trial
Possibility Intelligence Search for centralized repository of millions of IOCs extracted from ANY.RUNâs intensive database of interactive malware analysis sessions..
Right here below, now we relish mentioned your total ingredients that can presumably be venerable to assault the easy obfuscator:
- Breakpoint
- Memory dump
- The De4dot
Contemporary obfuscators make exercise of developed versions of these ways. With an enhanced working out, researchers are well-ready to appear up-to-the-minute obfuscators completely, which helps them delve into their core difficulties.
Fragment 2 will duvet extra code security strategies. How obfuscators counter breakpoints, De4dot, and memory dumps. Learn how to circumvent their defenses to treasure the code and various spell binding ingredients will additionally be examined. We can care for you posted.
Strive all aspects of ANY.RUN Interactive malware analysis premium access at zero payment for 14 days with a Free Trial.
Source credit : cybersecuritynews.com






