What is a Security Operations Center (SOC)? A Detailed Overview
What is a Security Operations Center (SOC)? A Detailed Overview
Listed here, we are in a position to uncover the theory that of a Security Operations Center (SOC) in higher detail, including its capabilities, benefits, and key substances.
In this day’s digital world, cyber security risks are changing into increasingly more severe. Organizations are at elevated threat from recordsdata breaches, cyberattacks, and diverse security incidents that can possess a solid affect on them.
In command to take care of these assaults, many organizations possess established security operations services.
Table of Contents
- What Is a Security Operations Center (SOC)?
- How a Security Operations Center Works
- What are the roles in Security Operations Center?
- What are the SOC Factors?
- Key Functions of a SOC
- What Are the Benefits of a SOC?
- What are the SOC Challenges?
- Conclusion
What Is a Security Operations Center (SOC)?
A Security Operations Center is a central unit interior a company that affords administration and monitoring of its cybersecurity operations.
It’s generally staffed by cyber experts who’re to blame for detecting and examining security incidents, moreover to responding to them.
The heart is designed to supply a complete witness of a company’s safety posture when it combines security alerts with community logs from diverse techniques and capabilities.
The predominant responsibility of the safety operations middle shall be to await, uncover, and react in the match of a security incident.
These activities encompass surveillance of that it is possible you’ll well possible also imagine threats, examination of security occasions and logs, and vulnerability assessments in command to name potentially unhealthy vulnerabilities.
The SOC personnel shall be to blame for helping with incident response, collaboration with diverse IT groups to diminish threats, and reporting incidents to administration and diverse alive to occasions.
The predominant substances of the SNE are SIEM techniques, threat intelligence feeds, advice on facing incidents, and qualified cyber security consultants.
Security match logs from a vary of sources are unruffled and analyzed by the SIEM plan, as are threat intelligence feeds that supply updated recordsdata on that it is possible you’ll well possible also imagine threats.
Detailed instructions on take care of every fabricate of security match are incorporated in the Incident Response Handbook.
The responsibility of qualified cybersecurity consultants lies in the implementation of those procedures and in responding to occasions that occur.
In a nutshell, the Security Operations Center (SOC) is an well-known ingredient of a company’s cybersecurity infrastructure.
Setting up a central location to visual display unit, analyze, and answer to security incidents, would possibly maybe well assist construct sure the safety, integrity, and availability of noteworthy recordsdata and techniques.
How does a Security Operations Center work?
A Security Activities Center (SOC) is designed to assist as a centralized place for controlling and keeping an survey on a firm’s cybersecurity activities. Listed below are the major steps furious by how a SOC in most cases works:
Collecting and examining security occasions:
- An SOC collects recordsdata from a necessity of sources, e.g., security frameworks fancy firewalls, interrupt identification schemes, and endpoints.
- This recordsdata is unruffled and broken down by a Security Files and Cases Management (SIEM) framework to acknowledge possible security risks.
Detecting possible threats:
- The SIEM framework will possible be examined by the SOC personnel in command to command any unforeseen actions or that it is possible you’ll well possible also imagine risks.
- Thru a combination of guidelines-essentially essentially based mostly and habits-essentially essentially based mostly analysis, the SIEM System finds risks.
Investigating possible threats:
- The SOC personnel investigates possible threats and assesses their seriousness in command to construct if they are a accurate hazard or a fraudulent obvious.
- To prefer the starting place and fabricate of a threat, additional recordsdata want to be gathered, a forensic investigation want to be performed, and threat intelligence recordsdata want to be aged.
Responding to security incidents:
- The SOC personnel will initiate a reaction to end and lessen the keep of the incidence if a security phase is confirmed.
- This entails adhering to established incident response requirements and offering detailed instructions on take care of particular match forms.
Reporting and documenting incidents:
- The SOC personnel shall document every incident alongside with its nature and the action that has been taken to answer to it, moreover to classes learned.
- These recordsdata shall be aged for the capabilities of growing cybersecurity legislation in the Association and reporting to its diverse presidents and companions.
Continuous enchancment:
- The SOC personnel will continuously review and update its processes, tools, and procedures in command to construct sure that they proceed to play an efficient role when faced with continuously evolving threats.
- Monitoring of novel threats, evaluate of incident recordsdata, and adaptation to augment the organization’s security posture are phase of this direction of.
Temporarily, the Security Operations Center SOC is gathering and examining safety occasions, figuring out that it is possible you’ll well possible also imagine risks, assessing these threats, facing them, responding to incidents, recording occurrences, and continuously improving its practices and procedures.
This would possibly maybe also assist to construct sure that every body the core recordsdata and techniques of a company are kept confidential, pure, and accessible thru proactive detection and response to security risks.
What are the Roles in the Security Operations Center?
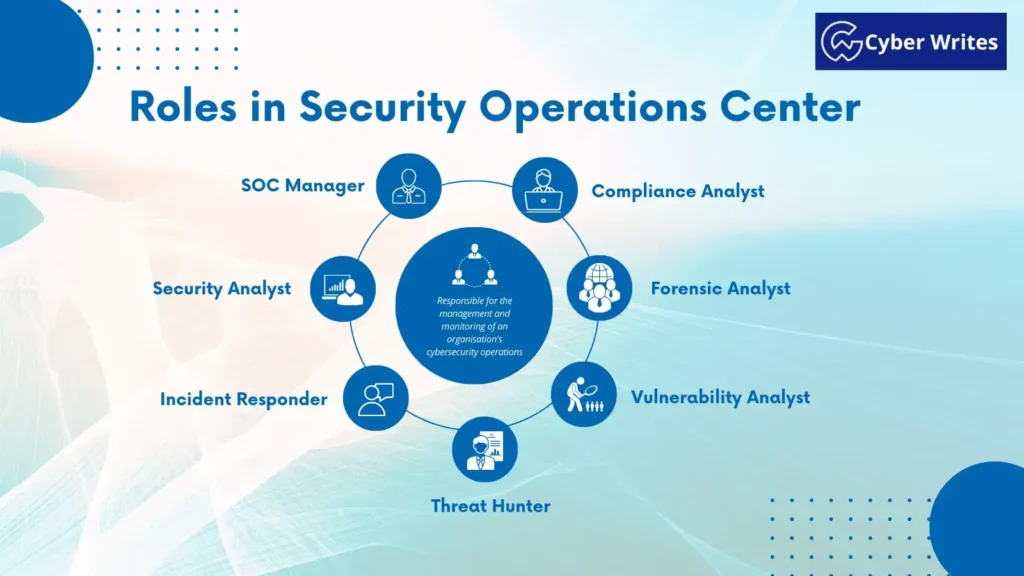
A Security Operations Center (SOC) contains cybersecurity consultants who’re to blame for the administration and monitoring of a company’s cybersecurity operations. Listed below are about a of the major roles in most cases command in a SOC:
SOC Supervisor:
- The SOC manager is to blame for the day’s operations of the center.
- This entails keeping the Security Operations Center in step with the organization’s overall security approach, growing and imposing safety policies and procedures, and managing a SOC personnel.
Security Analyst:
- Security analysts are looking forward to security occasions and figuring out that it is possible you’ll well possible also imagine threats.
- They’re reviewing security logs, investigating incidents, and recommending systems to diminish risks in the area of safety.
Incident Responder:
- Security incidents want to be handled by incident responders as snappy as that it is possible you’ll well possible also imagine.
- They shall construct sure that they follow predefined incident response manuals and work on restoring techniques and services which possess been affected, to end and crop again the affect of an incident.
Possibility Hunter:
- It is the threat hunters themselves who’re to blame for the proactive detection and identification of without doubt severe security threats by making use of standard Analytics and Possibility Intelligence feeds.
- They undertake a review of possible threats, behavior forensic analysis, and impart recommendations for improving corporate security.
Vulnerability Analyst:
- Vulnerability analysts ought to end vulnerability assessments and penetration checks in command to stumble on possible security flaws.
- They uncover on the outcomes of those research and supply recommendations for reducing the dangers they stumbled on.
Forensic Analyst:
- Investigating security issues moreover to gathering and examining digital proof are the tasks of forensic analysts.
- To take a look at the starting place and scope of security issues, they employ forensic tools and systems.
- They then supply recommendations for strengthening the organization’s security posture.
Compliance Analyst:
- The Compliance Analyst is to blame for guaranteeing that the affiliation meets in general pertinent security guidelines and norms.
- They display consistency with managerial necessities, focus on up and accomplish security tactics and philosophy, and gives propositions to additional foster the affiliation’s consistency.
The safety operations middle is made up of a community of cybersecurity consultants performing a huge need of roles, just like SOC Supervisor, Security Analyst, Incident Response, threat hunter, vulnerability analyst, forensics analyst, and compliance analyst.
Effective administration and control of an enterprise’s cyber security activities is well-known to every of those roles.
What are the SOC Factors?
The organization’s major security-related unit is the Security Operations Center, or SOMC.

The Security Operations Center frequently is the central entity to display and dissect security cautions, distinguish and answer security episodes and accomplish and uphold successfully-being systems.
The substances of a SOC in most cases encompass:
Folks:
- Duty for monitoring, examining, and responding to security incidents lies with the SOC personnel.
- The personnel is also made up of safety analysts, incident response personnel, threat hunters, and executives.
Processes:
- The SOC shall note the procedures in place for detecting, examining, or reacting to incidents.
- In command to accumulate shut into memoir adjustments in the threat landscape, such processes shall be recorded, repeated, and updated generally.
Expertise:
- SOCs rely on diverse applied sciences to visual display unit and analyze security occasions.
- These would possibly maybe well also encompass SIEM (Security Files and Events Management) tools, intrusion detection/prevention techniques, endpoint detection and response (EDR) alternate strategies, and intelligence feeds in regards to the threat.
Files:
- The Security Operations Center need so as to uncover admission to relevant sources of recordsdata, including community logs, plan logs, and diverse security match recordsdata.
- In command to name security issues and review safety breaches, this recordsdata will possible be aged.
Services:
- SOCs need a stable and legitimate location to operate from, with acceptable backup, community, and uncover admission to controls.
The substances of the Security Operations Center work together to construct an built-in security approach that can assist organizations in figuring out and facing safety threats all of sudden and successfully.
Key Functions of a SOC
The SOC performs a vary of key capabilities to succor the protection of a company’s assets and give protection to them from cyber threats. One of the most predominant capabilities of a SOC encompass:
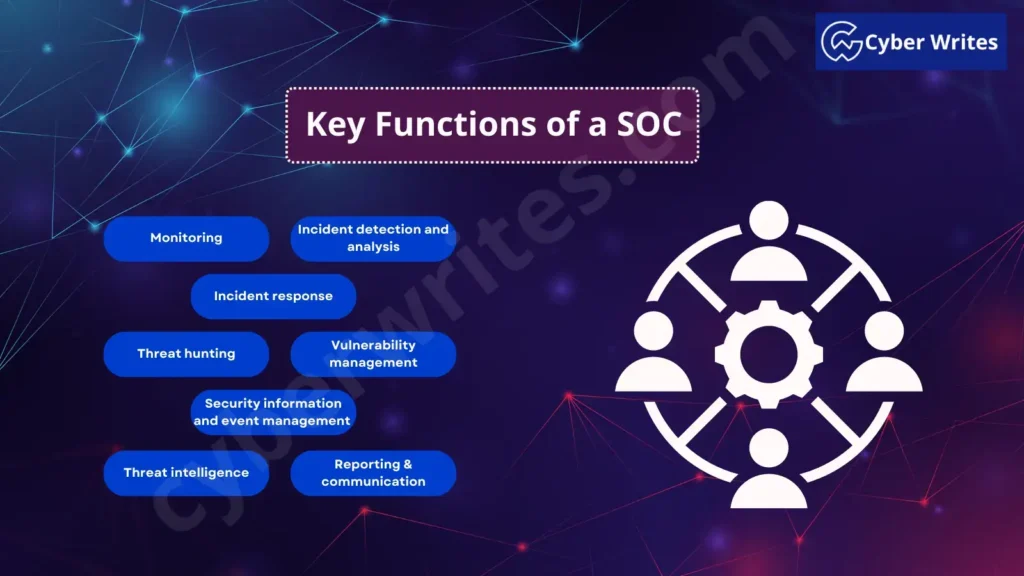
Monitoring:
- One in every of the major tasks of a SOC is to visual display unit a company’s networks and techniques for that it is possible you’ll well possible also imagine security incidents.
- This additionally capacity taking a uncover at logs or diverse recordsdata sources to detect irregular habits just like irregular web traffic on a community and attempts of unauthorized uncover admission to.
Incident detection and analysis:
- When a security match is detected, the SOC personnel investigates the incident to prefer its space off, scope, and severity.
- This entails conducting an intensive analysis of the incident and its affect on the organization’s techniques and recordsdata.
Incident response:
- The SOC personnel conducts an investigation right into a security match to take a look at its nature, extent, and severity.
- The incident’s investigation, moreover to its outcomes on the organization’s recordsdata and techniques, will additionally be completely examined.
Possibility looking out:
- The SOC proactively searches for possible security threats or vulnerabilities interior the organization’s community and techniques.
- This would possibly maybe also accumulate examining community traffic, plan logs, and diverse recordsdata sources to name possible threats that can possess gone undetected.
Vulnerability administration:
- The SOC has responsibility for figuring out, prioritizing, and mitigating security vulnerabilities in the organization’s techniques and networks.
- On this vogue, it would possibly maybe possibly well also accumulate vulnerability assessments, software patching or updates, and the introduction of security checks to diminish the threat of exploitation.
Security recordsdata and match administration (SIEM):
- System operators shall use SIEM tools to rep and analyze recordsdata on security occasions from a vary of sources, just like community recordsdata or plan logs.
- The identification of possible security risks helps the organization assess its safety postures, which in turn gives invaluable perception.
Possibility intelligence:
- To succor an survey on essentially the most standard security threats and to protect against them in a proactive manner, SOCs are using threat intelligence feeds.
- To search out that it is possible you’ll well possible also imagine threats, it is miles also well-known to review recordsdata from open-supply intel feedsOSINTs, darkish web boards, and diverse sources.
Reporting and dialog:
- The Security Operations Center (SOC) is to blame for offering periodic updates on a company’s safety impart to key stakeholders, just like administration and recordsdata know-how workers.
- It likewise assists with illuminating financial backers and security approach producers concerning conceivable playing, which is able to supply them with a more noteworthy comprehension of their decisions.
The SOC is playing a severe role in the protection of a company’s assets from security threats, thru inserting forward active safety measures, snappy response, and incident detection, moreover to constant enchancment to its security posture with vulnerability administration and threat discovery.
What Are the Benefits of Having a SOC?
There are several benefits to having a Security Operations Center (SOC) interior a company, including:
Improved security posture:
- The Security Operations Centre can assist an enterprise’s complete safety posture with rapid detection and elimination of threats in command to supply a centralized location for the control and decision of security issues.
Reduced threat:
- The Security Operations Center would possibly maybe well also assist decrease a company’s overall threat of security breaches or incidents by proactively monitoring possible security threats.
Faster incident response:
- Security operations services can answer to security issues more snappy and efficiently, which lessens the detrimental outcomes on the synthetic operations and repute of their organization.
Better visibility:
- Thanks to the SOC’s uncover admission to to a company’s community and techniques, IT consultants would possibly maybe well also better realize their atmosphere and command that it is possible you’ll well possible also imagine risks.
Compliance:
- Many piquant regimes would possibly maybe well also ask the creation of a security operations middle (SOC) in command for enterprises to possess a solid security program in place.
Cost savings:
- The Security Operations Center can assist decrease the aptitude costs of a security incident, just like misplaced productiveness, recordsdata, or repute, by figuring out and responding to security risks more snappy. broken.
Proactive threat looking out:
- In the match of an emergency, SOC would possibly maybe well proactively name vulnerabilities or that it is possible you’ll well possible also imagine threats to organizations’ networks and techniques which would possibly maybe well also assist mitigate security issues sooner than they occur. occur.
A SOC would possibly maybe well also present a company with a proactive and efficient security program that can assist to beat again that it is possible you’ll well possible also imagine security risks and lessen the affect of security occasions.
What are the SOC Challenges?
A Security Operations Centre (SOC)’s setup and repairs will possible be grand for a necessity of reasons.
These encompass an absence of sources, just like knowledgeable workers, infrastructure, and know-how, alert fatigue attributable to an abundance of security alerts; the complexity of security threats, the placement of integrating a vary of IT techniques and capabilities; the expense of inserting forward and coaching qualified workers, and compliance with regulatory frameworks.
Property, recordsdata, and unwavering effort are well-known to meet these barriers in command to succor an efficient SOC and retain a solid security posture.
Conclusion
A Security Operations Centre (SOC) is, in essence, a centralized location interior a company that is to blame of keeping song of, figuring out, and responding to security issues.
It performs an crucial phase in a company’s security program by proactively monitoring that it is possible you’ll well possible also imagine security threats, snappy figuring out and mitigating security occasions, and reducing the overall threat of security breaches or incidents.
No matter the benefits, growing and sustaining an efficient SOC is also grand and want money, recordsdata, and power work.
Total, a company would possibly maybe well also succor a solid security posture and give protection to itself from that it is possible you’ll well possible also imagine security risks with the aid of a successfully-established and successfully managed SOC.
Source credit : cybersecuritynews.com






