What is Spoofing? How It Works and How to Prevent it
Spoofing is a malicious note that disguising as a sound supply to reach at ease recordsdata, or to reach gain admission to to victims’ gadgets. An attacker can trick you into believing that he’s from the supply by spoofing.
Spoofing is a form of attack where, “what we peep will inquire of respect it, however it indubitably is no longer”.
Kinds of Spoofing
Email Spoofing:
About 90% of Cyber Attacks are conducted by emails. Email spoofing is one thing where the attacker sends an email posing as a sound sender by spoofing the “From:” contend with. The Victim will no longer perceive the sender’s contend with and falls for the attacker.
Prevention: Test the sender’s contend with if an undesirable email is got and assemble no longer obtain attachments except the sender is verified. Test the email header and be sure the header is no longer modified.
Name Spoofing:
Name Spoofing is a uncommon note wherein attackers carry out a call in half of the legitimate organizations and in quest of deepest recordsdata reminiscent of bank card and debit card tiny print, financial institution tiny print and diversified deepest recordsdata.
Prevention: Attain no longer give away at ease recordsdata reminiscent of bank card tiny print, checking story tiny print, or social security amount over the phone.
Internet contrivance Spoofing: This attack is technically called Phishing where the attacker creates a internet internet site and tips us into entering credentials.
Prevention: In any respect times test the internet sites URL earlier than entering credentials. If the URL does no longer match the usual internet sites URL assemble no longer enter credentials.
ARP Spoofing: Expanded as Tackle Resolution Protocol Spoofing. This Spoof is of two kinds,
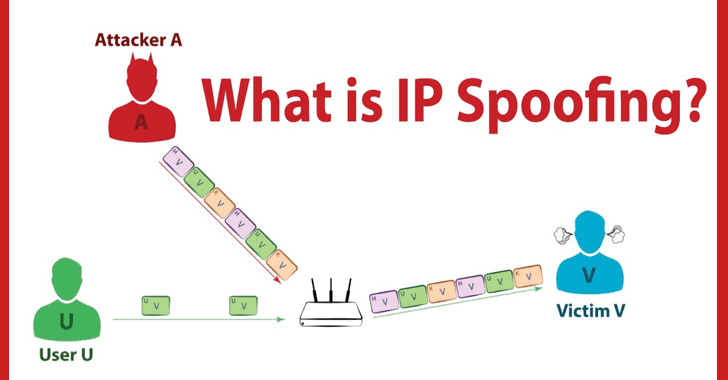
- IP Spoofing: The attacker finds the deepest IP contend with, and tips the router in believing he’s furthermore from the identical community. Generally, this attack is executed to reach gain admission to to a server that is most efficient accessible for specified systems internal a community.
Prevention: Reducing the Subnet and Clearing the log of empty IP addresses will lower this fashion of attack.
- MAC Spoofing: All of us know that MAC Tackle is the permanent contend with given by the manufacturer. And the attacker can spoof the MAC contend with of a particular contrivance internal a community to reach illegitimate gain admission to to a server.
Prevention: Installing Packet Filters or Dynamic ARP Inspections will lower these form of Spoofing Attacks.
Spoofing Infographics

Source credit : cybersecuritynews.com


