What is SYN Attack? How Does the Attack Works ?
TCP SYN Flood attacks are essentially the most in vogue ones amongst DDOS attacks. Right here we can discuss, intimately, the premise of the TCP SYN assault and to quit it before it reaches those servers.
It’s been greater than twenty years since the first DDOS assault modified into once tried on the College of Minnesota, knocking it down for 2 days. Loads followed that, alongside side thought to be one of the major excellent in the history of DDOS, which modified into once in opposition to Github and alive to a 1.35 TBps assault in opposition to the positioning.
DOS attacks pose severe threats to servers and web sites by flooding the targeted servers with bogus web page web page visitors, denying official web page web page visitors get entry to.
How the SYN Attack Works
TCP SYN assault is believed to be one of essentially the most in vogue DDOS attacks, which goal the hosts that bustle TCP processes and exploit the long-established TCP three-procedure handshake direction of.
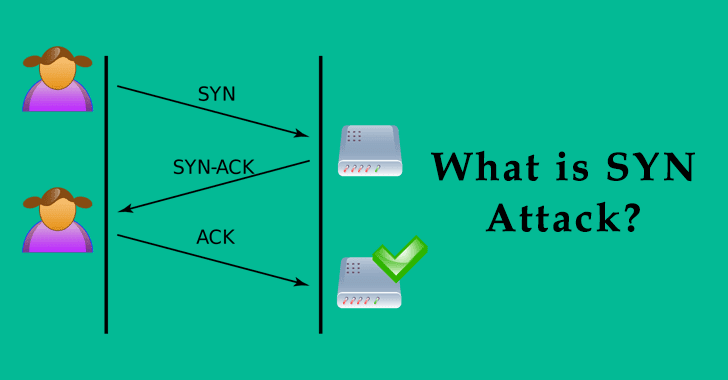
In a long-established TCP advise, dialog between the patron and server begins after organising a virtual connection. The patron initiates a connection by sending SYN requests to Server, and Server then responds abet by sending SYN/ACK.
This SYN/ACK is an acknowledgment of the preliminary SYN ask from the patron. The patron responds by ACK packet, finishing the connection to delivery dialog.
In a DDOS ambiance, a malicious actor spoofs the Client and sends excessive SYN requests from random IP addresses to the targeted server.
The server, assuming it to be official requests responds with SYN/ACK, but never receives a final ACK abet, thus tying up the Server’s sources with half of-open TCP classes which in the end outcomes in denying the official connection requests.
The excellent option to Prevent SYN Flood Attack
SYN Cookies
Not like long-established TCP handshakes, it works by warding off the necessity to defend a sing desk for all TCP half of-open connections. This procedure employs the utilization of cryptographic hashing. The server crafts the ISN (Preliminary Sequence Number) alongside with the preliminary SYN-ACK flood despatched to the patron.
This ISN is calculated per Source IP, Vacation draw IP, port numbers, and a secret number. When the server receives ACK from the Client, it validates it for its legitimacy by checking if the incremented ISN fits after which allocating memory for the connection.
Increasing Backlog Queue
Every Running System allocates memory to half of-open connections and there might well be a limit to the option of those connections it will most likely possibly defend. As soon as that limit is performed, it begins dropping off the connection.
Within the case of the SYN assault, the limit of the backlog will also be increased and would forestall the dropping of official connections.
Firewall Filtering
Firewall filtering will also be enabled on the firewall to detect and forestall these SYN attacks. To illustrate, the provision threshold will also be modified. In this case, a particular threshold will also be arrange before the firewall drops connections from one provide.
It would be major to tag that, not like other attacks, SYN assault doesn’t require tough systems; the complete attacker need is a PC with a dial-up connection to originate high-affect attacks.
Linked Read
Source credit : cybersecuritynews.com


