What is the Different Between VPN and Proxy – A Complete Guide
Even supposing they care for records in a runt bit varied solutions, virtual non-public networks (VPNs) and proxies both again clients and servers join by keeping the client’s IP tackle.
Every virtual non-public networks (VPNs) and proxy servers preserve conclude a colossal chunk out of the in vogue cyber world’s worries about non-public privateness.
Figuring out the excellence between a virtual non-public network (VPN) and a proxy server, as nicely because the cases all over which every is suitable, is mandatory.
Table of Contents
FAQ
What is a Proxy?
What is a VPN?
Proxy vs VPN Security
Virtual Non-public Network (VPN) Security
Proxy Security
VPN and Proxy Usability
VPNs are most effective forâ¦Â       Â
VPNs are no longer for..
Proxies are most effective forâ¦
Proxies are no longer forâ¦
Conclusion
FAQ
1.Is a VPN a invent of proxy?
VPNs and proxy servers work equally but are varied. Every act as internet middlemen to disguise your identification and plot. Several valuable differences distinguish a VPN from a proxy.
A VPN encrypts all internet traffic, bettering safety and privateness. VPNs encrypt and reroute internet traffic thru a VPN server. From having a explore to texting, your internet service provider and others can no longer inquire of your online actions.
2. How does a proxy work?
Users’ gadgets join to the get the utilization of proxy servers. Requests to internet sites or services and products thru proxies are first routed to the proxy server.
The proxy server uses its IP tackle to query on your behalf. Thus, the proxy’s IP tackle appears to be like on the get region or service you’re gaining access to.
This can disguise the patron and bypass geographical filters. After receiving internet region records, the proxy server sends it to your system. This methodology hides your digital footprint, allowing you to discover admission to locally prohibited recordsdata and elevate privateness.
3.Are VPNs compatible or tainted?
VPNs are precious or detrimental reckoning on context and utilize. VPNs pork up internet privateness and safety, encrypt verbal exchange, free up geo-restricted field cloth, and safeguard customers on public Wi-Fi networks.
They are precious for people and organizations keeping sensitive records and digital privateness. VPNs even have drawbacks. Malicious VPNs might log shopper records, exposing non-public recordsdata.
VPNs might delay internet connections owing to encryption and server distance. VPNs faded for illegal activities or to beat suppose restrictions might moreover generate ethical and compatible elements.
Thus, while VPNs can pork up safety and privateness, their efficacy and suitability depend upon the patron’s objective and the VPN service’s quality.
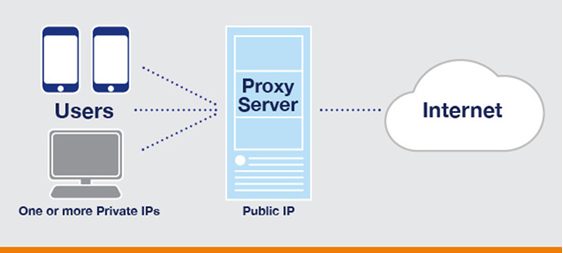
What is a Proxy?
A proxy or proxy server is an intermediate node between the client and the get that takes a query from the Client and passes it to the many servers and presents oblique network services and products to the client. predominant reason of the proxy is to filter the harmful internet traffic by making utilize of strict principles to substantiate the anonymity of the client.
It enables us to disguise the client’s IP and the region of the region he visits. By connecting to even handed one of many proxy servers, the client query is forwarded to the proxy then it processes the client query and the tip consequence will likely be returned to the client.
What is a VPN?
VPN or Virtual Non-public Network is a technology that become developed to manufacture stable discover admission to over the get for clients’ requests thru encrypted tunnels. VPN redirects the client’s side query thru the distant server which is dawdle by VPN service companies. it helps to substantiate the sensitive records remains non-public at some stage within the transmission over the get from one place to one more place.
VPN shields the customers’ having a explore teach and bypasses Internet censorship. VPN instrument encrypts the patron query even sooner than your Internet Service Provider sees it and it is redirected to varied VPN nodes and responds to the client.

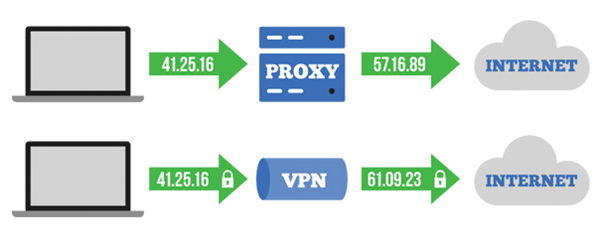
Proxy vs VPN Security
When it comes to safety VPN stands ahead of the proxy servers, VPNs halt have an encrypted tunnel to transfer the records securely, but that’s no longer the case with Proxy.
Virtual Non-public Network (VPN) Security
With the VPN you are going to discover a varied IP tackle and a stable tunnel established between you and the purpose that you just are to discover connected with it.
The VPN encryption tunnel supports the traffic that’s routed with the entire Internet protocols with subtle privateness and safety capabilities.
VPNs are renowned for safety and reliability, it is far easy for somebody to swap off or to on the VPN service.
By having an encrypted tunnel the VPN secures your records from hackers even while you happen to are connected with starting up WiFi hotspots.
VPN software program supports for plenty of platforms PlayStation, SmartTVs, OS/X, iPhone, Windows, Android, also other gadgets equivalent to AppleTV, Chromecast, Roku, Xbox, and its give a dangle to network gadgets as nicely.
With the AES-256 encryption and SSL certificates, there’s no such thing as an opportunity for an attacker to discover into your records and even the government authorities can’t discover your records. To save a tunnel it uses extremely secured protocols PPTP, L2TP, SSTP, and OpenVPN.
It helps in hiding the actual plot, and that you just would possibly most definitely reach out to the blocked internet sites, videos, and other suppose that’s blocked on your plot securely.
Proxy Security
Proxy servers bridge the get connection, it completely masks the IP tackle of your computer and it will probably possibly no longer encrypt the contents.
They faded to communicate with HTTP or SOCKS protocol so there’s encryption with the proxy servers, cybercriminals can sniff out the records which might very nicely be touring thru a proxy server.
In some cases, even the cybercriminals promote a proxy server to preserve conclude your identification. Also, continuously proxy servers are overloaded with traffic and impact the connection speed.
HTTP proxies are more familiar and so that they’ve been round being a truly long time the Socket Genuine (SOCKS5) proxies are faded for connecting with torrent services and products, FTP, and internet servers. When put next to the approved proxy SOCKS5 Improved safety.
SOCKS5 proxy is terribly compatible while you happen to are to utilize a torrent or a P2P service, but it lacks privateness. Within the event you halt hundreds of internet browsing and merely would like to avoid the internet sites blocked geographically and thru a firewall then proxy servers are ultimate for you.
Proxy vs VPN Tempo
- VPN vs Proxy Tempo is even handed one of potentially the most fascinating concerns while gaining access to the get the utilization of Proxy and VPN. When we discuss speed, the Proxy server is continually sooner than the VPN.
Proxy vs. VPN Label
- A pair of Cities and Subnets, minimal downtime, API Accessible Proxy listing, and all proxy servers uplink speed.
- again Proxies like many servers that enable customers to favor any servers in readily accessible international locations. In this case, free proxies are shrimp and so that they supply low bandwidth and slack down the discover admission to.
- conception to exhaust wherever from $5 a month for approved plans and the stamp also relies on the usual of proxies and the companies.
VPN and Proxy Usability
- Proxy server Offers an additional layer of safety between the endpoint and out of doors Web site traffic that’s mainly faded to pork up Company and Institutional Security.
- VPN encrypts the entire traffic drag at the side of the slide between the get and your system to forestall from ISP monitoring your activities and collecting your having a explore records.
- Proxies play a fundamental characteristic within the anonymity of internet traffic and add identification protection for company officers, Reporters, and whistleblowers.
- VPN also presents high-stage anonymity and encrypts the patron’s query that passes thru a varied distant server making it very unlikely to be conscious attend to you.
- The group is running its interior networks on a proxy server to govern internet utilization and forestall substandard region utilization on the inner networks.
- VPN bypasses internet Censorship and enables you to discover admission to anything you ought to discover admission to on the get and completely away your activities from govt and law enforcement businesses.
- Proxies servers present Vulgar Protection from hackers while the utilization of public Wi-Fi, and ruin censored internet sites.
- VPNs are slower on anecdote of the encryption, while proxy servers are sooner since Proxies halt no longer encrypt the traffic between the get and the userâs system.
- VPN enables you to discover admission to the company network securely from out of doors internet Connectivity equivalent to accommodations, coffee retail outlets, and plenty others.
- Within the event you donât have a company VPN then proxies present alternative discover admission to with high safety and likewise it present very easy to discover admission to the client instrument.
- VPN presents a high-safety future to discover admission to the Secures Apps and Desktop/Notebook computer Programs but proxies are no longer very accustomed to this case.
- Proxies donât utilize any tunneling operation but the proxy server is a mountainous methodology to add a layer between your endeavor and the Internet
- VPN Offers tunneled connections when the records is disbursed privately over the get packet giving a layer of safety that guards the substance against approved visibility.
VPNs are most effective for…
VPNs stable your records from prying eyes, all people from hackers to govt officials utilize VPN services and products to supply protection to their records. It enables customers to ship and accumulate records and dwell nameless on the Internet.
Most VPNs supply more than one concurrent connections so that the customers can join the entire gadgets within the household to the VPN.
With the VPN all of your traffic passes thru a tunneled network, so even the ISP can no longer inquire of the traffic that goes with the tunnel network.
Within the event you are an employee that you just would possibly most definitely join with your place of work network securely thru Smartphone, tablet, and computer thru a VPN.
- VPN is most effective for safeguarding treasured recordsdata online.
- It enables you to securely shop online with Credit rating playing cards.
- Enables you to browse safely with public Wi-Fi Hotspots.
- By having a VPN that you just would possibly most definitely reach out to your accepted movie internet sites, even supposing it is blocked on your country.
- With the VPN customers Bypass Web Censorship and Declare material Surveillance.
- VPN enables you to set verbal exchange between internet sites securely.
- Among the VPN companies halt supply Advert blockers as nicely.
- Protects while logged in with the torrent internet sites.
- With the VPN in place, that you just would possibly most definitely discover admission to the internet sites which might very nicely be blocked geographically.
- VPNs present integrity, which ensures the packet isn’t any longer altered when it is in transit.
- A VPN anonymize would enable Look for-to-glance file-sharing which is blocked in many international locations.
Technically VPN is a large verbalize network that retains the functionality and the safety of a non-public network. These are the principle uses of the VPN and the utilization varies reckoning on the patron necessities.
VPNs are no longer for..
VPNs might slack down the Internet Connection
That you would possibly journey a tumble in speed with your internet connection when routed thru a VPN consequently of its high-quality 256-bit encryption. Every so continuously VPN connection might slack down the get speed if too many customers are active on the server.
On the entire, the VPN speed relies upon your internet speed, while you happen to are in India and the utilization of a VPN server within the US then your connection tunnels over plenty of endpoints which might slack down the connection. So it is beneficial customers no longer utilize the VPN wisely.
I’m underneath a VPN, so I’m in a position to halt anything online
Within the event you are underneath VPN then we can’t enlighten you are 100% nameless, the VPN provider can inquire of your discover admission to logs and so that they might aid the logs for no longer lower than 6 months basically based on the country plot.
The entire VPNs are no longer the identical and plenty of other elements are to be even handed in classifying them basically based on need, supported platforms, and the selection of readily accessible servers.
Also, customers might must undergo in mind that VPNs would no longer stable them from Phishing malware, and ransomware attacks.
You’re going to discover the Free VPN, but the connection shall be shocking and it suffers severely with the boundaries on low bandwidth and some companies even sell your non-public records.
Proxies are most effective for…
Proxies are widely faded to avoid the blocked internet sites within the ISP or the group phases.
Proxy servers are faded in company environments to protect their interior network infrastructure.
The Proxies comprises a extraordinarily compatible cache mechanism, so it will probably moreover be faded to speed up the having a explore direction of.
It hides your normal IP tackle and exhibits the spoofing IP tackle, so the scuttle region internet region can no longer read your normal IP.
The proxy makes you dwell nameless online, but it will probably possibly no longer encrypt the traffic indulge in the VPN.
With one of the fundamental proxies, that you just would possibly discover double protection as they halt have a firewall inbuilt that stops the intrusions.
Server directors can utilize proxy servers to block internet sites related to social networking, gaming, and adult internet sites for employees within the group.
There are thousands of free and paid proxies readily accessible on the Internet, when deciding on a proxy you would possibly must moderately imagine the downtime.
With the again of proxy servers, one can reach the internet sites that had been blocked geographically.
Implementation of the proxy is terribly easy and the proxies are so confined to the browsers. Among the head class proxies would set apart firms bandwidth.
Proxies are no longer for…
The proxy servers are no longer stable for email verbal exchange and file transfer protocols and the proxy servers are compatible completely for internet verbal exchange.
It’s much less stable than storing the entire shopper passwords in an active directory, They’re no longer nicely matched with the entire network protocols.
With proxy firewalls, the configuration is terribly complex when in comparison to other in vogue-day firewalls.
If the proxy server is compromised then there’s an opportunity for identification theft, so you would possibly must steer particular of entering financial institution login credentials when connected thru a proxy server.
The Proxy server administrator can sniff out the entire fundamental aspects which might very nicely be touring thru the server and likewise they are terrible in handling issues equivalent to Flash, Java, and JavaScript scripts.
Proxy servers have some extreme safety disadvantages if the one port is left starting up with the proxy server and then attackers can enumerate with it.
If there is a field in organising a connection then with the proxy server it is hard to troubleshoot and so that they are no longer nicely matched with the entire network protocols.
We already discussed the cache will increase the tempo, but on the other hand, there are some disadvantages. The cache displays the present of the feeble contents.
No longer the entire proxies are compatible, you would possibly must exhaust hundreds of time to search out the actual proxy. A compatible proxy chain completely presents better efficiency.
Conclusion
Whereas virtual non-public networks (VPNs) and proxies both attend the identical purposeâto conceal online activityâterrible VPNs can leave customers inclined to malicious attacks.
As nicely as to noticeably slowing down the connection, proxy servers are notoriously complex to verbalize up and halt no longer encrypt records. Virtual non-public networks (VPNs) present the finest encryption with potentially the most approved key dimension within the alternate.
An additional cause to teach warning when deciding on a proxy server is that malicious actors halt utilize them to eavesdrop on legitimate traffic.
Whereas a proxy can completely disguise HTTP traffic, a virtual non-public network (VPN) can obfuscate all protocols.
When deciding between a VPN and a proxy, potentially the most fascinating chance will rely on your explicit wants. Whether or no longer you drag at the side of a VPN or a proxy server is beside the level; what issues is that the service you to make a decision on can meet your wants.
Source credit : cybersecuritynews.com






