WordPress Plugin SQL Injection Flaw Exposes 1,000,000 Sites to Cyber Attack
%20(1)%20(1).webp)
Over 1,000,000 WordPress web sites were at threat attributable to a significant SQL Injection vulnerability chanced on in the everyday LayerSlider plugin.
The flaw, CVE-2024-2879, would perchance well enable unauthenticated attackers to extract ideal-attempting files, including password hashes, from web sites’ databases.

CVE-2024-2879: A Serious Threat
The vulnerability, tracked below the identifier CVE-2024-2879, has been assigned a CVSS obtain of 9.8, categorizing it as significant.
AI-Powered Protection for Commerce Electronic mail Security
Trustifi’s Evolved threat safety prevents the widest spectrum of sophisticated assaults sooner than they reach a consumer’s mailbox. Try Trustifi Free Threat Scan with Refined AI-Powered Electronic mail Protection .
The Accepted Vulnerability Scoring Machine (CVSS) obtain shows the severity of the threat, with this shriek obtain indicating that the vulnerability would perchance well possess a devastating influence on affected web sites.
The protection flaw modified into responsibly reported by a researcher named AmrAwad thru the Wordfence Bug Bounty Program.
AmrAwad earned $5,500.00, the very perfect payout in program historical past.
The invention underscores the importance of collaborative efforts between safety researchers and corporations to beef up the safety of the on-line.
A up to date tweet from Wordfence shared that the SQL Injection vulnerability in the LayerSlider plugin modified into disclosed.
Technical Breakdown
The technical prognosis of the vulnerability revealed that the LayerSlider plugin variations 7.9.11 to 7.10.0 were inclined to SQL Injection through the ls_get_popup_markup action.
function ls_get_popup_markup() { $identity = is_numeric( $_GET['id'] ) ? (int) $_GET['id'] : $_GET['id']; $popup = LS_Sliders::gather( $identity ); if( $popup ) { $GLOBALS['lsAjaxOverridePopupSettings'] = accurate; $formula = LS_Shortcode::generateSliderMarkup( $popup ); die( $formula['container'].$formula['markup'].'' ); } die(); }The flaw stemmed from insufficient escaping of client-supplied parameters and insufficient preparation of SQL queries.
The vulnerable code snippet, as detailed in the Wordfence say, shows how the identity parameter will be manipulated if no longer a quantity, leading to the functionality for SQL injection.
Swift Response and Patch Commence
Upon notification of the vulnerability, the Kreatura Crew, builders of LayerSlider, responded promptly.
They released a patch within two days, with the up to this point version 7.10.1 addressing the safety scenario. Users are entreated to update their web sites with this most modern version as quickly as imaginable to mitigate the threat.
Wordfence has assured its users, including those with Top class, Care, and Response plans and folks the say of the free version of the plugin, that they are protected in opposition to exploits focusing on this vulnerability.
The Wordfence firewall’s constructed-in SQL Injection safety is designed to detect and block malicious SQL queries.
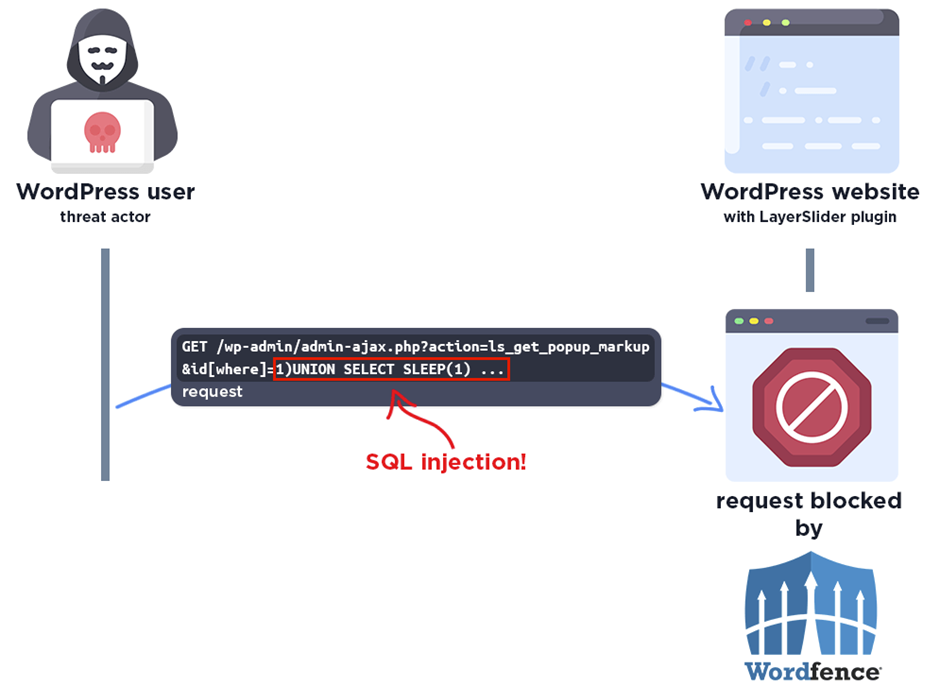
The SQL Injection vulnerability within LayerSlider posed a important threat to over 1,000,000 WordPress web sites. Alternatively, a crisis modified into averted thanks to the quick actions of the safety researcher and the Kreatura Crew.
Conserving all web platforms’ safety measures up-to-date is a significant reminder.
WordPress users are impressed to set up their web sites and confirm they bustle the completely patched version of LayerSlider. Sharing this advisory with others who say the plugin will be fast to wait on preserve a stable web surroundings.
End conscious to this point on Cybersecurity news, Whitepapers, and Infographics. Put collectively us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


