Xiaomi Phones with MediaTek Chips Found Vulnerable to Forged Payments

CheckPoint researched the payment machine constructed into Xiaomi smartphones powered by MediaTek chips. From the evaluation, they identified vulnerabilities that can allow the forging of payment capabilities or disabling the payment machine in an instant from an unprivileged Android application.
Xiaomi’s TEE
The relied on execution atmosphere (TEE) targets to process and retailer sensitive safety files resembling cryptographic keys and fingerprints. TEE safety is in line with hardware extensions (resembling ARM TrustZone) that preserve the TEE world safe even on rooted devices or these compromised by malware.
Generally, in trend implementations of the TEE for mobile devices are Qualcomm’s Ranking Execution Atmosphere (QSEE) and Trustronic’s Kinibi.TEE creates a receive digital world managed by a relied on OS that runs relied on apps, also a relied on app implements a selected safety aim.
Xiaomi devices on Qualcomm chips use QSEE relied on OS. MediaTek-primarily primarily based fully devices use Kinibi. Researchers examined Xiaomi Redmi Label 9T 5G with MIUI Worldwide 12.5.6.0 OS.
Depended on App Layout
Researchers cloak that a relied on app can have a couple of signatures following the magic fields. The magic fields are the same across all relied on apps on the instrument. Furthermore, they are connected to the app fields of all other devices, resembling Xiaomi T11 and Xiaomi Label 8 Pro.
“An attacker can bypass safety fixes made by Xiaomi or MediaTek in relied on apps by downgrading them to unpatched variations”, CheckPoint.
Within the case of Xiaomi, it follows the GlobalPlatform TEE Inner Core API Specification in imposing relied on apps. Every app exports the “TA Interface” capabilities, which are the entry beneficial properties to keep the app event, narrate the event that a brand unusual client is connecting, narrate the event when the client invokes a issue, etc.
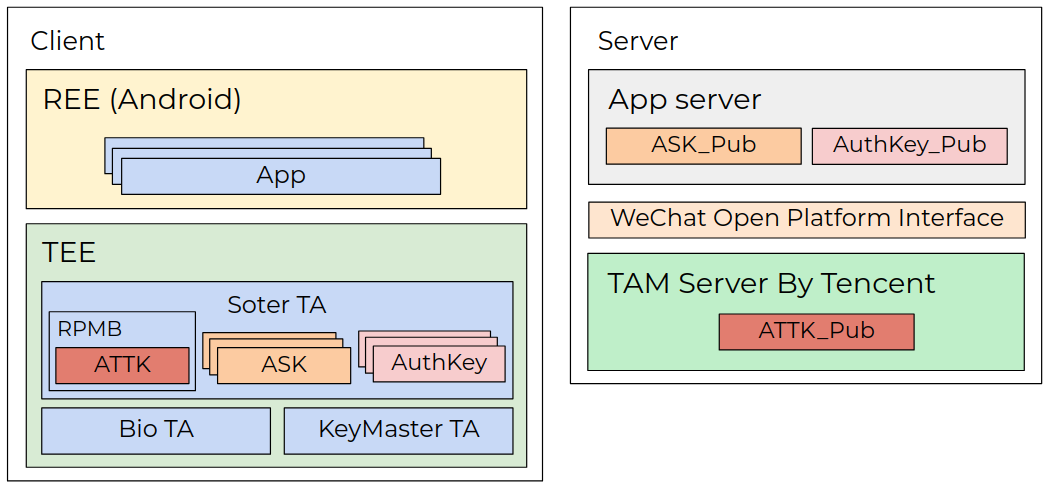
Xiaomi devices have an embedded mobile payment framework called Tencent Soter that provides an API for third-celebration Android capabilities to integrate the payment capabilities.
An unprivileged Android application would possibly perchance well well exploit the CVE-2020-14125 vulnerability to attain code within the soter relied on app and forge payment packets.
Xiaomi, following responsible disclosure, has rolled out patches to tackle CVE-2020-14125 on June 6, 2022. “The downgrade fret, which has been confirmed by Xiaomi to belong to a third-celebration vendor, is being mounted,” Take a look at Level added.
Sponsored: Your SWG Battle Plan: 3 Steps to Achieve Web Security
Source credit : cybersecuritynews.com


