XSS Vulnerability in Google Subdomain Let Hackers Hijacks the User Sessions

Security researcher Henry N. Caga has identified a principal depraved-location scripting (XSS) vulnerability interior a Google sub-area that enables hackers to fabricate diverse assaults, including session hijacking, phishing assaults, malware distribution, and facts Theft.
This vulnerability exposed a harmful actor entry level and highlighted the significance of solid cybersecurity insurance policies.

Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no person as security groups must triage 100s of vulnerabilities. :
- The difficulty of vulnerability fatigue at the moment time
- Difference between CVSS-relate vulnerability vs risk-essentially based mostly vulnerability
- Evaluating vulnerabilities in response to the exchange impression/risk
- Automation to diminish alert fatigue and provides a raise to security posture enormously
AcuRisQ, that lets you quantify risk precisely:
Let’s earn into the parable.
The Discovery
All around the investigation, he suspects the URL that associated with https://aihub.cloud.google.com will be predisposed then he skilled an unsuccessful strive to exploit the ‘q’ parameter with diverse payloads, in the end crafting a double-encoded payload that printed the XSS vulnerability.
Upon realizing the aptitude severity of the vulnerability, the researcher meticulously documented the job utilizing Burpsuite and crafted a detailed myth for Google’s security personnel. Nonetheless, the preliminary myth hit a snag when the Google personnel may possibly well well also no longer replicate the XSS pop-up.
Undeterred, the researcher delved deeper, growing a bash script to again and again quiz the inclined URL, which confirmed the inconsistency of the vulnerability’s arrangement off.
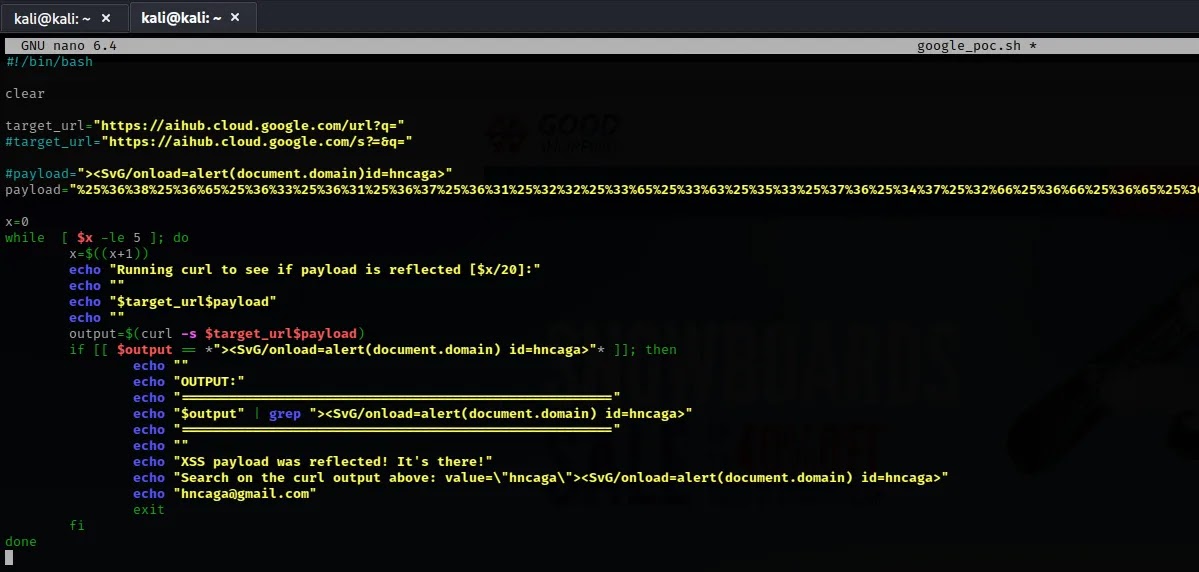
While perusing Google’s subdomains, a relate URL sparked suspicion:
https://aihub.cloud.google.com/url?q=https://cidadesmineradoras.com.br Intuition urged a possible flaw, prompting an investigation.
The researcher began trying out diverse payloads on the ‘q’ parameter, specializing in a appreciated XSS payload:
">Irrespective of encoding the payload to bypass possible filters, preliminary makes an try were ineffective.
Persistence resulted in double encoding the payload, one diagram that, surprisingly, induced the XSS vulnerability.

The second of success became captured by a Burpsuite-recorded video.
Extra investigation printed that the XSS vulnerability became no longer isolated to a single URL but affected all URLs from the aihub.cloud.google.com area when the ‘q’ parameter became appended.
Reporting and Decision
Adhering to to blame disclosure protocols, the researcher promptly reported the expanded findings to Google’s security personnel.
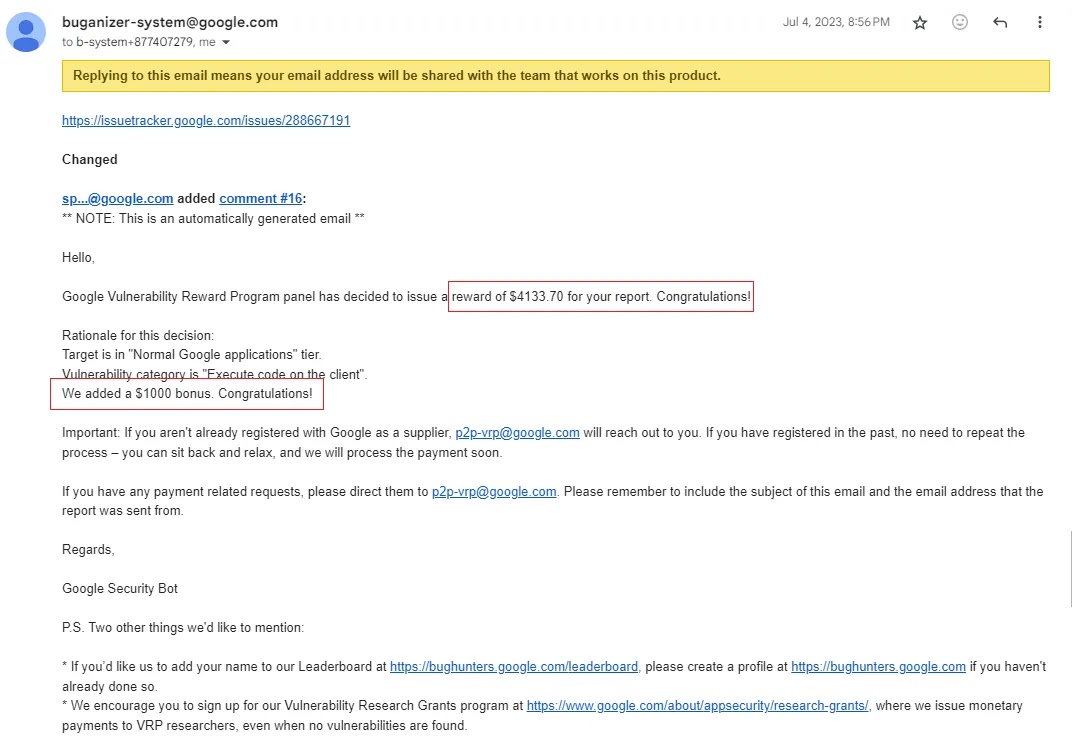
The personnel responded fleet, upgrading the verbalize’s precedence and severity ranges and expressing appreciation for the “Nice Earn!” The researcher became rewarded $4,133.70, including a $1,000 bonus for their comprehensive myth and proof of thought scripts.
The Affect
The XSS vulnerability posed principal dangers, including:
- Session Hijacking: Attackers may possibly well well also indulge in exploited the vulnerability to raise over user sessions.
- Phishing Assaults: The flaw may possibly well well also indulge in facilitated the advent of phishing pages to deceive users.
- Malware Distribution: Users may possibly well well also were redirected to malware-weighted down internet sites.
- Data Theft: Sensitive facts cherish cookies and tokens were at risk of theft.
- Recognition Damage: Such security lapses may possibly well well also hurt Google’s fame for stable services.
The incident reminds us of the chronic need for tough cybersecurity measures, even contained within the infrastructure of craftsmanship leaders cherish Google. The collaborative efforts of users, developers, and security mavens are a truly great in affirming a stable online ambiance.
Acknowledgment
The researcher expressed gratitude to Google’s security personnel for their suggested and legit going by of the vulnerability, which ensured the persevered security of users worldwide.
On March 15, 2024, the researcher bought an update from the Google security personnel informing me that the vulnerability had been resolved. Nonetheless, the placement began returning a 502 error, which Google clarified became attributable to the deprecation of aihub and its migration to Vertex AI since January 2024.
Are you from SOC and DFIR Groups? – Analyse Malware Incidents & earn are residing Obtain entry to with ANY.RUN -> Commence Now for Free.
Source credit : cybersecuritynews.com


